Protecting APIs & Securing Applications So Business Can Thrive
This post is also available in:
 Japanese
Japanese
Happy New Year! How about we start it with a quick pulse check?
Does your organization have the desired visibility into application security events? Can you enforce consistent application protection across multiple platforms? How many APIs are you using and which data do they handle? Is application security well integrated into your continuous deployment pipeline?
Here’s what your fellow industry professionals have to say about these questions, and more.
Radware partnered with Osterman Research to study recent developments in the field of application infrastructure and data security. Together, we surveyed over 200 professionals worldwide from enterprises of >1000 employees globally, and would like to share the key insights in this blog.
The State of Application Development & Delivery
It is evident that application development as well as production environments are more amorphic and elastic than ever before, bringing together many independent components that interoperate and facilitate secure application delivery. The cement of these emerging architectures is APIs, that allows data exchange, integration, and automation.
Migration to Public Cloud
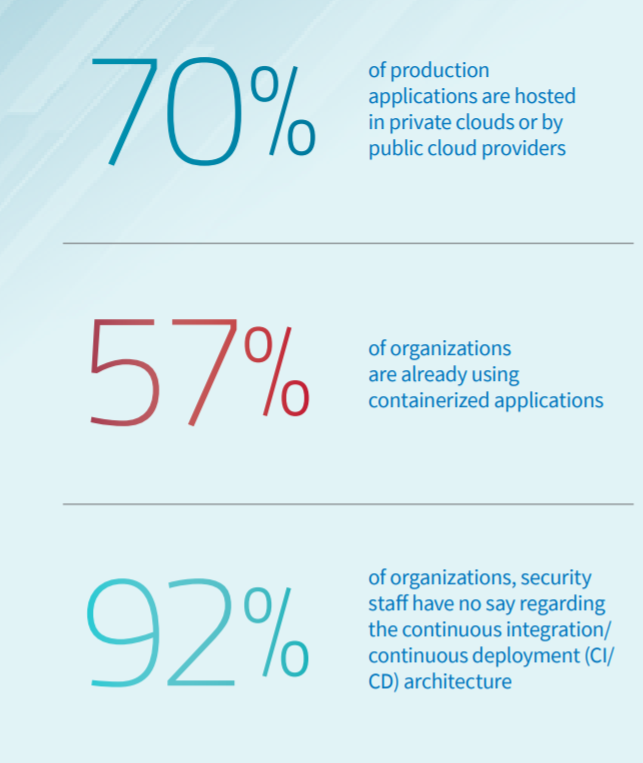
Much chatter touched upon the accelerated migration to public cloud infrastructure. Our research has found that 70% of applications in production already run in the public cloud, rather than hosted in the corporate datacenter. In addition, as enterprises disperse their apps and data across multiple providers (and datacenters), the top application security management concerns they mention (other than threat coverage) are consistency (of security policy) and visibility (into events).
Containerized Applications
57% are already using containerized applications and are in need of robust application and data security (in addition to pure container image security & vulnerability scanning). Also, it was interesting to learn that a little over half of respondents do not see how using containers contributes to financial efficiency.
Security Integration into ADLC
Despite the threats outlined in the report, security is not a top priority in application development practices:
- Only 45% of organizations agree or strongly agree that security is well integrated into their continuous integration/continuous delivery (CI/CD) pipeline, and more concerning,
- In approximately 90% of surveyed organizations, security staff are not the primary influencers on application development architecture or the budget. In most cases, they are asked to secure a “given” information network.
This brought us to look at roles and responsibilities in modern application development and delivery groups and found out that 43% agree or strongly agree that security considerations should not interrupt the application release cycle. Moreover, only 42% agree or strongly agree that their DevOps team and security staff know their responsibilities very well.
[You may also like: Application Delivery & Protection For the Multi-Cloud Era]
The Threat Landscape
APIs are the next big threat. Protecting APIs from cyberthreats is a growing concern in application security, and enterprises around the globe are telling us they perceive APIs as the #1 threat, the #1 concern (55%) and #1 investment priority (59%) in application security for 2021.
APIs interconnect systems, networks, applications, and devices today. They are used in IoT devices, microservices, mobile apps, event-driven processes and a variety of application integration use-cases.
Radware’s report analyzes API utilization’s business objectives vs. security risks across various development and production environments. Our research shows that more than half of applications of nearly half of organizations are exposed to the Internet or third-party services via APIs.
Enterprises are not prepared to properly manage bot traffic. With bot-generated traffic reaching nearly half of the overall internet usage, you’d expect businesses to take bot management seriously. It is important to remember that bots are not necessarily bad. In fact, some accelerate business productivity and decision making. However, in an age where sophisticated bots can mimic human behavior, it is imperative to differentiate bot from human, and good bots from bad bots, in order to fend-off illegitimate bot activity.
Moreover, those surveyed are more likely to admit that bot attacks were successful compared to other attack types – in fact, only 39% of those surveyed have confidence in dealing with sophisticated bad bots.
[You may also like: Malicious Bots Have Realized Your APIs Are the Weak Link]
However, our research shows that only one-quarter of organizations have a dedicated solution to deal with bot traffic. In other words, three out of four still count on other application security solution with limited bot detection capabilities. Perhaps this is the reason that so many bot attacks go under the radar?!
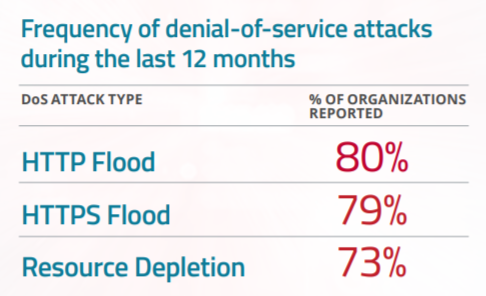
Most Denial-of-service (DoS) Attacks Are HTTP Floods. Considered a network level attack, DDoS is the most common attack vector against applications. Eighty-nine percent of those surveyed have experienced such an attack on their web applications, one-third of which occur on a weekly basis. DoS attacks at the application layer are frequently in the form of HTTP/S floods. Other vectors include low-and-slow attacks that are aimed at keeping connections open until the application server can accept no more user requests, or other forms of resource depletion attempting to get the CPU or memory to 100% utilization, thus causing a denial of service state to the application server.
Mobile Apps Are Less Secure By Design
In 2020, in light of the pandemic, the world population increased their day-to-day life management from their mobile devices – for working, learning, shopping, gaming, social interaction and what not.
Unfortunately, our research shows mobile app development is far less secure, and many organizations are not maintaining the same security practices they follow for web app development.
Only 36% of mobile apps have security fully integrated into their mobile application development lifecycle, with 22% admitting to have no security at all. A common practice among enterprises is having a third party to develop and maintain the mobile application. They are, however, the entity who owns the sensitive data, and should pursue and oversee there are no cracks in the barracks built around it.




