How To Achieve Application Protection Behind AWS/Azure CDN
Isn’t cloud-native application development exciting? You get to design the perfect CI/CD pipeline with all the latest and greatest tools, optimize resource utilization and time-to-release, and eventually show off to your bosses’ productivity as well as savings. Too awesome!
And then comes the security team. Oh no!
But wait, there are many solutions out there to protect cloud-hosted apps. Aren’t there?
Well, why don’t we put things in order?
The Web Application and API Protection market very much belong to cloud-based services. That sounds great too, doesn’t it? Outsource app-sec to experts, bundling it with CDN…. Wait! What?
Why you should rethink using a cloud WAF with a IAAS provider CDN service
- Cost – Using both services is not cost-effective. Also, you would be paying twice.
- Latency – Local application protection provides for a better user experience. In return, it provides for a better brand image as well as more revenue. There’s no point in sending each incoming HTTP request outside of the VPC for inspection and then back to the application. It eliminates all the above benefits of agile, continuous deployment.
- Data Privacy – Most enterprises today prefer keeping confidential data within the environment.
Suppose you are already using AWS CloudFront or Azure CDN services for traffic accessing your application development and delivery environment. In that case, another CDN/WAF service is less likely to fit your needs.
Local security for cloud-hosted applications
To keep enjoying all the benefits mentioned above and optimize your compute costs, service SLA, scalability, and agile development cycles, you’ll have to look another way.
Unfortunately, there aren’t too many technologies that provide complete application and data protection to these environments. Meaning, solutions that do not disrupt the software development lifecycle (physical or virtual web application firewall appliances come with a lot of tuning and overhead labor).
In other words, a solution that can deliver effective security from a broad set of threats as well as the required local installation, auto-scalability, high availability and did I say effective security?
Here’s something to think about. What do most choose when they feel security requirements overcomplicate everything? The easiest selection. However, those coming after your sensitive data know it won’t be easy and are upping their game time after time. Defenders shouldn’t be discounting themselves either.
[You may also like: How To Secure Applications At-scale From Code to Cloud]
Limitations of IaaS WAF
The easiest selection in our scenario would be the WAF technology provided by the public cloud vendor itself (AWS/Azure/GCP). All it requires is checking a box. However, they are not specialized application security vendors; analysts talk about the security gaps compared to those of market leaders. See below the image from Gartner’s latest “Critical Capabilities for Web Application and API Protection (WAAP), Nov. 2020”, where these offerings get low scores.
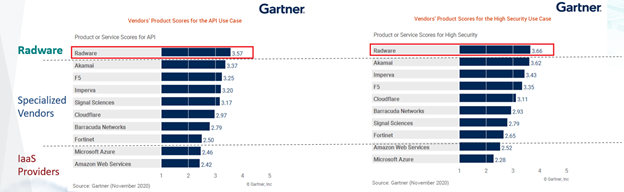
So, appliances out, other cloud services (i.e., not local) are out, and IaaS security is also out. Before talking about solutions, one additional aspect must be covered, which is:
The importance of API protection in cloud-native environments
Cloud-native development and delivery practices rely on synchronization and interoperability of multiple components, from orchestration to provisioning to event-driven apps and functions. All those different tools and open-source code, and third-party services (SaaS is a good example) are interconnected by an array of APIs. These APIs transfer sensitive data that requires protection.
However, many organizations can not tell:
- How many APIs they have
- Where all the API endpoints are
- What kind of data they are processing
- Their level of security
Once this is sorted out with a complete mapping and visibility, they can advance to evaluate detection and mitigation solutions. However, the whole CI/CD lifecycle depends on these APIs. Any introduction of a security solution is very delicate, at least in the eyes of DevOps/DevSecOps, as there are some risks of interruptions and hiccups in the service delivery.
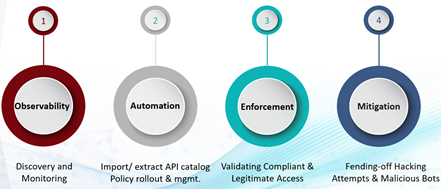
To summarize
Local, scalable application protection behind AWS/Azure CDN can be achieved by deploying a solution that provides provisioning, redundancy, and scale while delivering high quality of application security.
Radware Kubernetes WAF provides the #1 Web Application and API Protection solution for cloud-native applications. Learn more about protecting cloud native application development and delivery environments.



