What is a Zero-Day Attack?
Zero-day attacks are the latest, never-before-seen generation of attacks. They are not volumetric or detectable from a known application signature. Security systems and experts must react instantly to solve the new issues, that is, they have zero days to react. Advanced application-level attacks typically fit into this category.

Two Distinct Phases
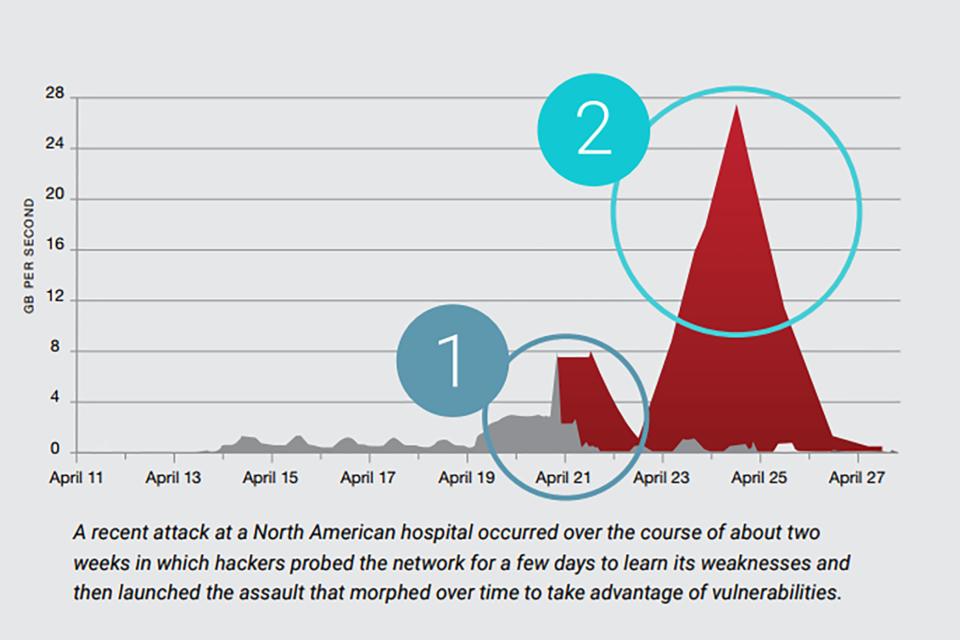
Probe and Learn: Hackers assess network defenses and probe for vulnerabilities, looking for different weaknesses and identifying the type of attacks that will potentially be effective. It’s like an archer who picks the best arrows to put in his quiver before battle. For example, a hacker may determine that a combination of encrypted attacks, attacks from a rotating IP address source, new low and slow attacks and headless browser attacks will be most effective.
[You may also like: Protecting Applications in a Serverless Architecture]
Optimize, Morph and Attack: Hackers launch the attack and then vary the attack vectors (or arrows from the quiver). In this case, hackers often understand that legacy DDoS mitigators need manual intervention to troubleshoot and mitigate a zero-day attack. So they attack the weakness of the legacy mitigator (multiple manual troubleshooting cycles to stop an attack) in addition to attacking the application vulnerabilities.
Who Are the Attackers?
Richard Clarke, former special cybersecurity advisor to the U.S. president, devised an acronym — C.H.E.W. — to categorize and explain the origin of cyberattacks (that specifically target carriers and enterprises):
- Cybercrime — the notion that someone is going to attack you with the primary motive being financial gain from the endeavor.
- Hacktivism — attacks motivated by ideological differences. The primary focus of these attacks is not financial gain but rather persuading or dissuading certain actions or “voices.”
- Espionage — straightforward motive of gaining information on another organization in pursuit of political, financial, capitalistic, market share or some other form of leverage.
- War (Cyber) — the notion of a nation-state or transnational threat to an adversary’s centers of power via a cyberattack. Attacks could focus on nonmilitary critical infrastructure.
[You may also like: How Cyberattacks Directly Impact Your Brand]
The attackers can range from a tech-savvy teenager to a highly organized group that taps into huge server farms in places like Russia and Ukraine to facilitate attacks.
The types of hackers are as varied that the methods they employ and include APTs (advanced persistent threats) agents, corporate spies, cybercriminals, cyberwarriors, hacktivists, rogue hackers, spammers and malware spreaders.

