WAFs Should Do A Lot More Against Current Threats Than Covering OWASP Top 10
Looking in the rearview mirror
The application threat landscape has rapidly evolved. For years, users consumed applications over the internet using the common tool – web browsers. At every point in time, there were 2-5 web browsers to support, and the variety of application development and testing frameworks was relatively limited. For instance, almost all databases were built using the SQL language. Unfortunately, not long before hackers began to abuse applications in order to steal, delete and modify data. They could take advantage of applications in different ways, primarily by tricking the application user, injecting or remotely executing code. Shortly after, commercialized solutions named Web Application Firewalls (WAF) emerged, and the community responded by creating the Open Web Application Security Project (OWASP) to set and maintain standards and methodologies for secure applications.
Fundamental Application Protection
The OWASP Top 10 list provides a starting point for ensuring protection from the most common and virulent threats, application misconfigurations that can lead to vulnerabilities, and detection tactics and mitigations. This list serves as an industry benchmark for the application security community and defines the basic capabilities required from a WAF.
In addition, there are other common attacks against web applications like CSRF, Clickjacking, web scraping, and file inclusions (RFI/LFI) to consider.
Challenges of Keeping Modern Applications Secure
Today, applications are not only web-based. There are cloud apps, mobile apps, APIs and in the latest architectures, even individual functions, that must be synchronized and supervised, as they all create, modify and process our data. New technologies and frameworks bring new challenges to the application lifecycle. This includes DevOps, containers, the internet of things (IoT), open source tools, APIs, and others.
This distribution of locations with the variety of technologies creates a very complex challenge not only to information security professionals but also to solution vendors that can no longer rely on a “one-size fits all” approach. Solutions must understand the business context of the applications they protect in order to minimize false-positives and optimize the customer experience.
[You might also like: Web Application Security in a Digitally Connected World]
A hacker’s ultimate goal would usually be either to steal data or to disrupt the application service. They too benefit from technological evolution. First, it creates more potential loopholes and vulnerabilities, and second, there are more tools and knowledge available to them to overcome traditional security heuristics. Organizations are left with a greater attack surface and bigger exposure to risk. As applications constantly change, security policies must keep up.
Thus, applications must be protected against an expanding variety of attack methods and sources and must be able to make educated decisions in real time to mitigate automated attacks. The result is increased manual labor and operational costs in addition to a weaker security posture. For us security vendors, there are more challenges to overcome.
Challenge #1: Bot Management
According to Radware’s web application security report, almost 60% of internet traffic is bot-generated, half of which is attributed to “bad” traffic. Organizations invest to increase network capacity, ultimately accommodating fictitious demand. Accurate distinction between human traffic and bot-based traffic, and between “good” bots (like search engines and price comparison services) and “bad” bots, can translate into substantial savings and an uptick in customer experience.
The bots won’t make it easy on you now as they can mimic human behavior, bypass CAPTCHA and other challenges. Moreover, dynamic IP attacks render IP-based protection ineffective. Often times, open source dev tools (Phantom JS for instance) that can process client-side JavaScript are abused to launch brute-force, credential stuffing, DDoS and other automated bot attacks.
To manage the bot-generated traffic effectively, a unique identification (like a fingerprint) of the source is required. Since bot attacks use multiple transactions, the fingerprint allows organizations to track suspicious activity, attribute violation scores and make an educated block/allow decision at a minimum false-positives rate.
Challenge #2: Securing APIs
Many applications gather information and data from services that they interact with via APIs. When transferring sensitive data via APIs, more than 50% of organizations neither inspect nor protect APIs to detect cyber-attacks.
Common API use cases are:
- IoT integration
- Machine-to-machine communication
- Serverless environments
- Mobile applications
- and event-driven applications.
API vulnerabilities are similar to those of applications and include injections, protocol attacks, parameter manipulations, invalidated redirects and bot-generated attacks. Dedicated API gateways evolved to secure the interoperability of application services that interact via APIs. However, they do not provide the end-to-end application security that a WAF can, with the necessary security controls such as HTTP parsing, Layer 7 ACL management, parsing and validation of JSON/XML payload and schema enforcement, and full coverage of the OWASP Top 10 vulnerabilities. This is accomplished by extracting and inspecting key API values using both positive and negative models.
[You might also like: Another Problem I Face: Securing APIs in Continuous Delivery]
Challenge #3: Denial-of-Service
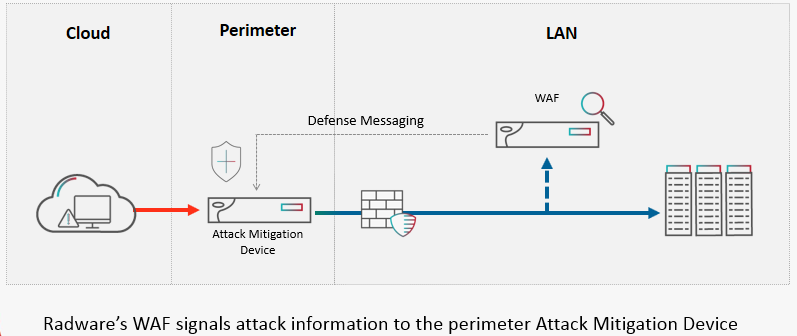
DoS is an old attack vector that has still proven efficient at attacking applications. A handful of appealing techniques are available to perpetrators who’d like to disrupt application services, such as HTTP or HTTPS floods, low-and-slow attacks (SlowLoris, LOIC, Torshammer) dynamic IP attacks, buffer overflow, Brute Force attacks, and more. Driven by IoT botnets, application-layer attacks have become the preferred DDoS attack vector. Most WAFs are stateful devices, as there is only a certain volume they can withhold. However, they have the ability to inspect HTTP/S traffic flows (some WAFs create baselines, very effective against unknown threats), and detect attacks and malicious attempts. Once an attack is detected, there is no reason to let it in again. To complement the WAF mitigation capacity limitation, a dedicated perimeter solution is required so the next bad packet is blocked automatically. For this to happen the two solutions need to communicate with each other:
Challenge #4: Continuous Security
Applications change frequently. Development and rollout methodologies, such as continuous delivery, mean applications are continuously modified with no human intervention or supervision. It is extremely difficult to maintain a valid security policy to safeguard sensitive data in dynamic conditions without creating a high number of false-positives. Mobile apps are modified far more compared to web applications, and how would you know when a third party app you rely on is changed?
Some folks strive to gain a greater visibility so they are aware of the risks. However, this isn’t always possible and a robust application protection must leverage machine-learning capabilities that map application resources, analyze possible threats, and create and optimize security policies whenever a modification to the application is introduced.
SUMMARY
As applications are playing a bigger and bigger role in our everyday life, they are also becoming a prime bounty for hackers. The potential gain for a hacker and the potential loss for a business are enormous. Securing these applications today is nothing less than very difficult considering the amount and variety of both applications and threats.
Luckily, we are at a point in time where artificial intelligence can give us a hand. Algorithms based on machine learning provide adaptive, real-time protection against the most sophisticated threats that target applications. They also update security policies automatically to safeguard web, mobile and cloud applications – as well as APIs – without generating false-positives.
We cannot be sure what will the next generation of application threats look like (probably based on machine learning too), but we sure can take action today to take a step towards securing our customer data, intellectual property and service availability, with great business value.