How Do You Create a Flight Plan to a Never-Ending Journey?
In April 2017, we conducted a global survey of C-suite executives. All respondents represent organizations with at least $250 million (or the equivalent) in annual revenue. Our goal: to understand their greatest challenges, threats and opportunities when it comes to cyber security.
When boarding a plane, have you ever wondered how much the pilot worries about the plane’s safety? His main job is to navigate through clouds and turbulence and land the aircraft at the right place at the right time.
A couple of advantages pilots have over executives today is that A) they have fully automated visibility into almost all real-time events, so they don’t have to rely on the human staff to collect and feed the information, and B) their journey has a definite destination and end.
We asked chief officers (CxOs) about their flight plan, from their cybersecurity concerns perspective. 200 executives from Europe and North America have expressed similar concerns, as well as similar goals, but showed different flight plans to get there.
Cyber Security can be ignored no longer
Neither can it be underestimated.
Executives today understand the importance of mitigating the risks posed by information security flaws to their business, and better yet – the opportunity in building cyber-resilience. Four out of five executives affirm that security threats are now a board-level concern. Further, almost all participants (94%) rate security as an extremely or very important priority. In addition, cyber-security is the number-one driver of their digital transformation programs, with 47% of executives citing improving information security as a major goal of their digital transformation.
60% of executives confirm having been a victim to at least one cyber-attack.
When the majority of the enterprises are under fire, no wonder this growing concern takes center stage at the board level discussions. While this finding is consistent with last year’s executive survey, it represents a much lower number than the 98% reported by information security practitioners in Radware’s Global Network and Application Security Report.
An interesting insight was the significant difference between European executives and their American counterparts – Europeans were more likely to report an attack than their American counterparts (75% vs. 36%). This is quite interesting and after scratching our heads for quite a while, we came up with few possible explanations:
- Cultural differences in reporting and sharing information regarding ‘non-events’
- Regulatory requirements where reporting upwards is mandatory
- A relatively higher preparedness level in the U.S. to cyber-security incidents
[You might also like: A View from the Corner Offices: New Research on C-Suite Security Mindset]
Willing to Invest in Intelligent Technologies
Four in five executives reported having already implemented more reliance on automated security solutions. Understanding the complexity of managing security these days, as the traditional network perimeter dissolves into an amorphous array of information hubs across platforms and third parties, and there is a need to facilitate and secure a growing number of data currents – this is becoming too demanding for organizations to try to handle themselves. The human factor is never ‘error-free’, and the need of the hour is automated solutions that dynamically update their controls and policies in real-time. Around the globe, two in five indicated that within two years, automated security systems—with machine-learning and artificial intelligence (AI) algorithms—will be the primary resources to maintain cyber security.
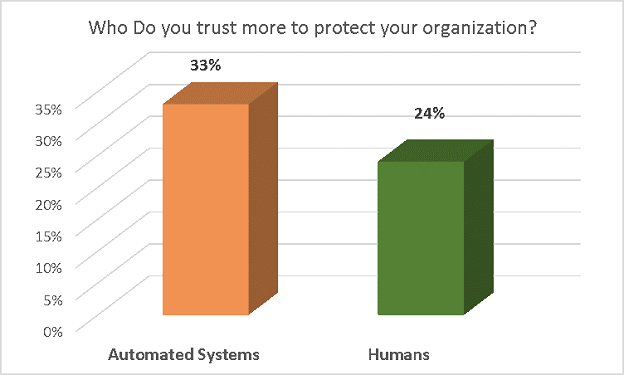
Radware’s research also points to a perceptional shift among C-suite executives—who seem to be warming to the idea of security supported by forms of automation rather than humans.
However, they are open to the idea of getting hackers onto their IT security teams (58% in Europe, 27% in North America). In fact, in Europe inviting hackers to test security systems, network infrastructure and databases is already a common practice. At the end of the day, hackers tend to think out of the box and can help with vulnerability mapping and forensics. At Radware, we see tremendous value in tapping into that experience and perspective.
Corporate Responsibility? Executives challenged with user privacy, despite a possible business impact
Two-thirds of executives agree that current laws related to information-security compromise privacy. Further, 79% think the government should do more to protect consumers’ personal information—and that is true even among those conceding that more stringent legislation could adversely affect their day-to-day operations.
Most-feared cyber-attacks
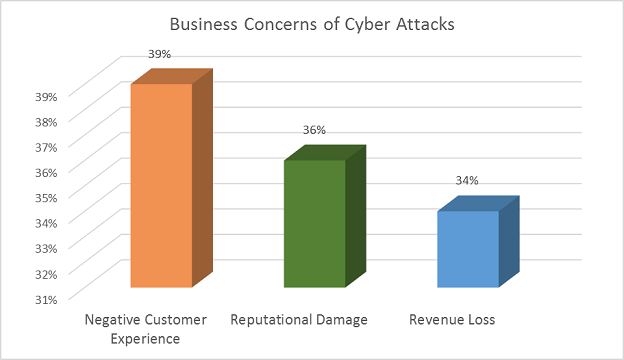
Business leaders worry mostly about corporate espionage, confidential data leakage or unknown, invisible impacts on their business. Concerning cyber-attack types, three in five executives claim that malware and bots or ransomware attacks would be extremely or very detrimental to their business. Other detrimental threats include Web application attacks and distributed denial of service, followed by APTs and socially-engineered infiltrations.
Today, they view a weakness in their cyber posture directly correlated with a risk to their competitiveness, particularly if it results in bad customer experience, reputational damage or revenue loss.
[You might also like: Cyber Security Recommendations from the C-Suite]
Ransom attacks: Reported decline
The survey took place before the worldwide WannaCrypt campaign on May 12th (read Radware’s full report on WannaCrypt here).
Globally, only 12% reported being the victim of such an attack. While the vast majority declare that they will not be paying any ransom if extorted, it is interesting to learn that this sentiment is stronger among executives who have already experienced a cyber-extortion attempt.
Although we saw a decrease in the prevalence of extortion attempts in the cyber space, the WannaCrypt campaign reinforces Radware’s 2016-17 Global Application & Network Security Report’s indication that ransom was the top motivation behind cyber-attacks in 2016. Cyber criminals looking for financial gain will not let go of such a rewarding tactic so easily.
Are we on the right track?
Reading the report, one can enjoy a sense of optimism, as despite the inevitable evolution of cyber threats, business leaders comprehend the challenge and take actions. These actions are to not only protect their organization by investing in cutting-edge defensive technologies, but also play a social role when guarding user privacy, collaborating with the regulators and sharing information within the community. With that notion, information security is becoming a top priority, and if organizations will implement dynamic mechanisms of continuously adaptive security, we may be able to stay close behind the cyber-delinquents.
However, this notion is not fully absorbed by the majority of organizations, and there is still a long way to go until it will become the common practice, and all solutions will be successfully deployed to protect companies and individuals. We would like to believe that in five years’ time, we will see a different picture.