Federal CISO: Superhero Needed
A famous leadership coach said, “Only Superman can leap tall buildings in a single bound, the rest of us must chip away at our goals one day at a time.” What a befitting quote for the position of Federal CISO! This role of organizing, equipping, training and leading the nation’s cybersecurity programs is not only ominous, it has thus far been an utter failure when historically approached.
On Tuesday, the New York Post reported that President Trump’s administration had eliminated the position of cybersecurity coordinator, with Rob Joyce leaving to return to the National Security Agency.

Let’s see if we can offer some brief lessons from past failures and find out what went wrong:
U.S. Cybersecurity Leadership: Historic Lessons Learned
First, let’s see how the nation has organized its past cybersecurity programs. Many would argue that the top leader of the information security program was the Cybersecurity Czar position first created by George W. Bush. Although the nation’s first Cyber Czar was outspoken and very knowledgeable, his style and approach left him unceremoniously departing the position within two years. Ironically many books were written about this time and many debates held, but I think one aspect of this position which is agreed to by most is that it accomplished little to prepare the country for cybersecurity posture and lead the country to the next level.
After Mr. Clark’s departure there was a period of over two times his original tenure to find a new replacement as the position was reevaluated and moved to a new reporting structure within the National Cybersecurity Center. In 2008, Rod Beckstrom lead this new position for approximately a year and was regarded mostly as a lame duck leader with the reality of a new incoming administration.
[You might also like: GDPR in Action, Even Facebook Impacted]
With the inauguration of Barak Obama in 2009, he not only kept this new position but ushered in a new Cybersecurity Coordinator center in the White House and appointed Melissa Hathaway as the nation’s new Cyber Czar. Unfortunately, once onboard, it was clear that Ms. Hathaway became disenfranchised and also unceremoniously departed after just two months on the job, providing the nation with the sobering realization that the top positions for U.S. Cyber Czar appears to be untenable.
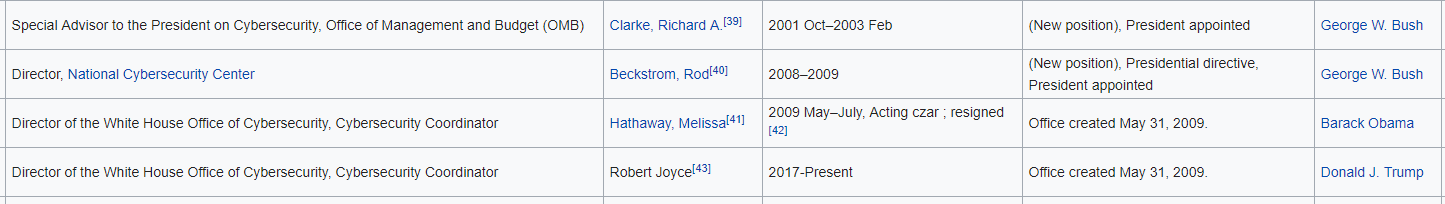
Federal CISO vs Cybersecurity Czar?
Now, one might venture so far as to ask, if we already have a Federal Cyber Czar, what is the difference between this role and the Federal CISO role?
Well, let’s look at the Responsibilities of the Cybersecurity Czar:
“Cyberspace is real. And so are the risks that come with it,” Obama said in a May 2009 speech establishing the cybersecurity coordinator position. At that time, he also outlined three principal duties for the role:
- Orchestrate and integrate the government’s cyber policies.
- Work with the Office of Management and Budget to make sure federal agencies have the necessary funds to deal with cybersecurity issues.
- Coordinate the response to a major computer incident or attack.
Fulfilling these duties requires the cybersecurity czar to collaborate with various government agencies. For example, working with the U.S. Department of Defense (DoD), which operates both a cyber-command to protect military computer networks and the Defense Computer Forensics Laboratory to deal with cases involving counterintelligence, terrorism and fraud. Within the DoD, he also works with the National Security Agency (NSA), which devises codes to protect sensitive information and monitors enemy communications.”
Now let’s look at the job description of the federal CISO illustrated by the previous Federal CIO, Tony Scott:
- Serve as the federal government’s lead cybersecurity strategist in the continuing cybersecurity risk assessment of the federal IT environment by employing widely accepted frameworks.
- Act as the liaison between the White House and the departments of Homeland Security and Defense, the Office of the National Intelligence Director and agencies’ CISOs for all federal cybersecurity activities.
- Receive top secret/sensitive compartmented information security clearance. The federal CISO will handle information concerning and derived from sensitive intelligence sources, methods and analytical processes.
- Meet certain qualifications to be certified by an Office of Personnel Management review board to receive “senior executive service” designation. A senior executive service position is somewhat analogous to a high-ranking military officer.
- Chair the Federal CIO Council’s Information Security and Identity Management Committee as part of his or her duty to effectively coordinate and align agencies’ CISO IT security governance.
- Establish a government-wide program to address the recruitment, retention and training of cybersecurity experts, with a focus on not just technical experts, but also versatile professionals who can effectively expedite IT along with the government’s mission and business functions.
- Design, implement and maintain effective cybersecurity performance measures for the federal government and lead the effort to maximize the value and effectiveness of security performance measures associated with the Federal Information Security Management Act, the law that governs federal IT security.
- Offer suggestions to the annual president’s budget that reflect cybersecurity priorities across federal agencies and ensure coordination and integration with the overall federal IT budget process.
[You might also like: New Threat Landscape Gives Birth to New Way of Handling Cyber Security]
Five Suggestions for Future CISO Success
Have a vision and sell it! No one before this position has yet to articulate what the future of cybersecurity means to the United States and / or has been able to sell it. You must be able to be an evangelist for what needs to be done!
Patience: This is not a race, but a marathon. The federal government needs someone who can balance the idea of a future vision, with the realities of how our government works and the ‘sausage factory’ it is in pursuit of the overall vision. This patience mustn’t be confused with a lack of energy or providing constant pressure, but rather a cool understanding and appropriate setting of the overall ‘challenge bar.’
Investment Balance: The issue that many have declared that the government is underfunded and lacks proper resources is a farce. Don’t be fooled in calling for even yet larger investments as there has been decades of GAO reports and unheralded failures of immense investments. The CISO will benefit greatly by trying to maximize the investment dollars of what is being spent already.
Establish a new framework: With accountability we need responsibility. Let’s face it, today these C-level positions within a government are mostly figureheads with no real operational responsibilities. For a high-performing CISO role to properly work, strategy and operations must be accountable to the role. This also means that compensation and a set of rewards and punishments must also be appropriately set. If a CISO accomplishes nothing more than setting in place a workable future structure whereby a security professional can be adequately compensated vis-à-vis an private industry peer and doesn’t need to take personal financial tradeoffs in order to employ their talents with the U.S. government, then they would have moved a mountain.
Lastly, you must execute. Doing nothing is not an option – – not for our country, not for the position, not for freedom-loving people throughout the world.