In a distributed denial-of-service (DDoS) attack, hackers flood a target website with so much traffic from multiple systems that it is rendered inaccessible to legitimate users. A DDoS attack is different than a denial-of-service (Dos) attack, which usually attacks from a single system.
Because DDoS attacks originate from multiple sources and send a larger volume of traffic into the system at once, it is difficult for network administrators to quickly detect and eliminate the threat. As such, DDoS attacks are more damaging than standard DoS attacks as they put an excessive drain on resources and sometimes completely take down an entire network or website.
In this article, we'll explore the difference between these two types of attacks and provide tips on how you can protect your systems from them.
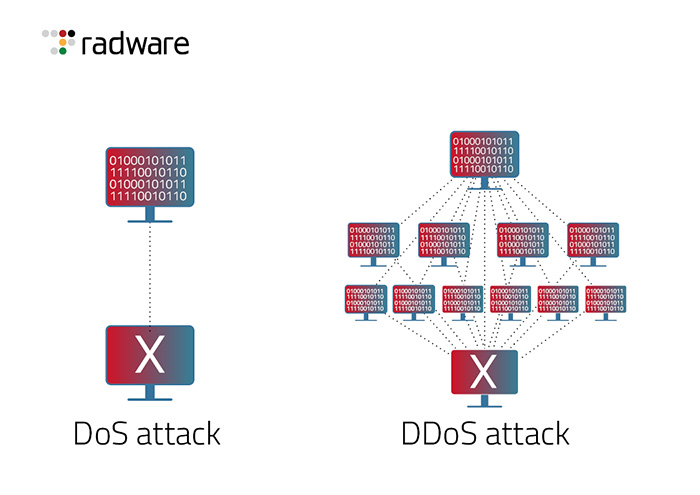
A DoS attack is a malicious attempt to degrade the performance of a server or disrupt its availability. This type of attack works by overwhelming the targeted resource with multiple requests, reducing the system resources available and eventually leading to an interruption of service. It works like this: Let's say a hacker sends a flood of fake requests to an online marketplace. The platform receives abnormal amounts of requests beyond its capacity, slows down and eventually stops working completely. DoS attacks can be used as a tool for extortion or to make political or other relevant statements, which is why it is important to protect yourself from these types of malicious activities.
A DDoS attack is a malicious attempt to disrupt the normal operations of a network or server. It is typically achieved by flooding it with superfluous requests from multiple sources, crippling the handling capacity and hindering its ability to respond to legitimate requests. This type of attack differs from DoS attacks as DDoS involves multiple machines—known as bots—to launch the attack from different locations. This masks the identity of the culprit and makes it more difficult for organizations to prevent or mitigate. In order to amplify the effect, some bots can even use thousands of machines in a single attack, making responding an arduous task. Therefore, it is important for businesses and organizations to invest both time and effort into equipping their networks with adequate security measures that can protect against possible DDoS attacks.
There are various types of DDoS attacks, the most common of which are SYN flooding, HTTP flooding, and UDP flooding.
SYN Flood
SYN flood is a type of DDoS attack that exploits the three-way handshake process in the Transmission Control Protocol (TCP), which is the underlying protocol of most internet communication. SYN floods aim to overwhelm a target system by consuming its resources and rendering it unable to respond to legitimate requests. In a SYN flood attack, the attacker sends a high volume of spoofed SYN packets to the target server without completing the final step of the three-way handshake. The server allocates resources to handle these incomplete connections and waits for the final ACK packet that never arrives. Consequently, the server's resource pool becomes exhausted, leading to legitimate requests being ignored or denied.
HTTP Flood
HTTP flood is a type of DDoS attack that targets web servers by overwhelming them with a massive volume of HTTP requests. The attack floods the target server with numerous legitimate-looking requests, exhausting its resources and rendering it unable to respond to legitimate user traffic. The attackers often use botnets, which are networks of compromised computers, to orchestrate the attack. By sending a continuous stream of HTTP requests, the attack aims to consume the server's processing power, memory, and network bandwidth. This flood of requests creates a bottleneck, causing the server to become overloaded and unresponsive, resulting in a denial of service for legitimate users trying to access the web server.
UDP Flood
UDP flood is a type of DDoS attack that targets network infrastructure by overwhelming it with a flood of User Datagram Protocol (UDP) packets. Unlike TCP, UDP is connectionless and does not require a handshake process, making it easier for attackers to generate high volumes of traffic with minimal overhead. In a UDP flood attack, the attacker sends a massive number of UDP packets to the target server or network, often using spoofed source IP addresses to make tracing difficult. Since UDP does not have built-in mechanisms to ensure packet delivery or verify the recipient, the target infrastructure has to process and respond to each incoming packet. As a result, the network becomes inundated with an overwhelming number of UDP packets, consuming its available bandwidth, processing power, and other resources. This flood of UDP packets causes congestion, network slowdowns, and can even lead to service disruptions for legitimate users trying to communicate with the targeted infrastructure.
In addition to being able to perform SYN floods and UDP floods like a DDoS attack as described above, DoS attacks also include:
ICMP/ Ping Flood
ICMP floods, also known as Ping floods, are a type of DDoS attack that targets network devices by overwhelming them with an excessive number of Internet Control Message Protocol (ICMP) Echo Request (Ping) packets. ICMP is used for network diagnostics and troubleshooting, including the well-known "ping" command. In an ICMP flood attack, the attacker sends a massive volume of ICMP Echo Request packets to the target device or network, often using botnets or multiple compromised computers to amplify the attack. Each Echo Request packet prompts the target device to reply with an Echo Reply packet, but in a flood attack, the sheer volume of requests quickly saturates the target's bandwidth and processing capabilities. This flood of ICMP traffic can lead to network congestion, increased response times, and even complete unresponsiveness of the target device, disrupting legitimate network communication.
Low Orbit Ion Canon (LOIC) attacks
Low Orbit Ion Canon (LOIC) is a network stress testing tool that gained notoriety for being used in distributed denial-of-service (DDoS) attacks. LOIC attacks typically involve multiple individuals coordinating to simultaneously flood a target server or website with a massive volume of traffic. These attackers may be part of a hacker group or anonymous online communities aiming to disrupt or protest a particular website or organization. When activated, LOIC allows each attacker to send a constant stream of HTTP, UDP, or TCP packets to the target, overwhelming its network resources and causing a denial of service. Due to its straightforward nature, LOIC attacks are relatively easy to execute, but they lack sophistication and often reveal the attackers' identities through IP addresses. As a result, LOIC attacks are not widely used by sophisticated threat actors but have been associated with low-level hacktivism or individuals seeking to cause temporary disruption without strong concealment measures.
| Criteria |
DoS Attack |
DDoS Attack |
| Definition |
A DoS attack is an attempt to make an online service unavailable by overwhelming it with traffic from a single source |
A DDoS attack is an attempt to make an online service unavailable by overwhelming it with traffic from multiple sources |
| Source of Attack |
Single source, usually one machine or IP |
Multiple sources, coordinated botnets, or compromised IPs |
| Complexity |
Relatively simple and easy to execute |
More complex, requires coordination and larger resources |
| Volume of Traffic |
Lower volume of traffic |
Significantly higher volume of traffic |
| Detection and Mitigation |
Easier to detect and mitigate as traffic comes from a single source |
Harder to detect and mitigate due to traffic coming from many different sources |
| Impact |
Limited impact on the target |
Severe impact, capable of overwhelming the target |
Conclusion
Both DoS and DDoS attacks are illegal and unethical, as they cause harm to targeted systems and disrupt legitimate users' access to services. Organizations should employ appropriate security measures to protect against such attacks, including DDoS protection services and network security configurations.