
The OSI (Open Systems Interconnection) Model is a conceptual framework that standardizes and defines the functions of a telecommunication or networking system. It's a crucial tool in the world of networking and plays a fundamental role in understanding how data communication works across various network protocols and technologies.
The model was developed by the International Organization for Standardization (ISO) to promote interoperability and facilitate communication between different devices and systems, regardless of their manufacturers. The OSI Model is structured into seven distinct layers, each with a specific set of functions and responsibilities, as explained in the next section.
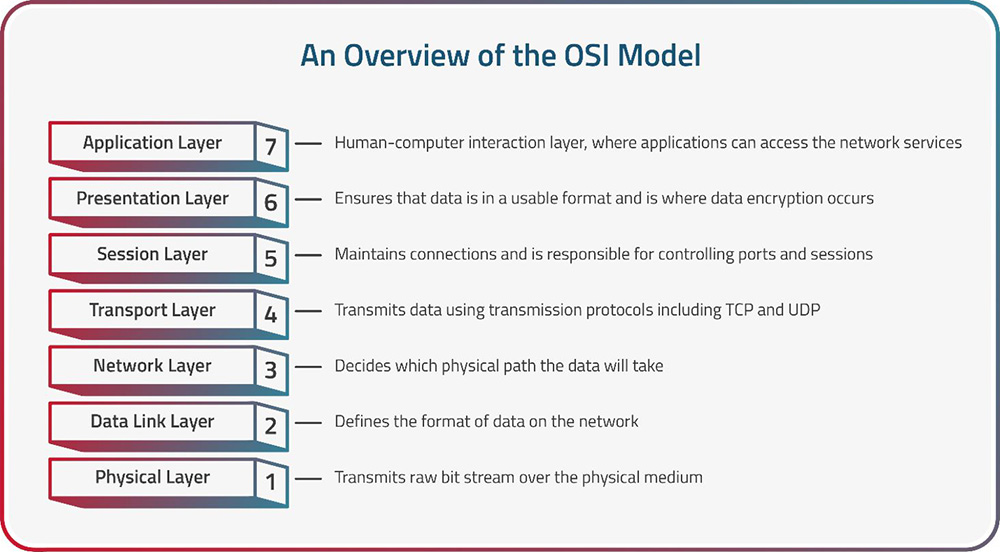
The OSI Model operates by allowing each of its seven layers to perform specific functions while relying on the services provided by the layer immediately below it. When data is transmitted from one device to another, it passes through all seven layers at the sender and then traverses all seven layers at the receiver. Here's how it works:
Data Encapsulation:
Data from the application layer is encapsulated in a format specific to that layer. As it moves down the OSI Model, each layer adds its own header and possibly trailer information to the data.
Data Transmission:
The data, now structured into frames or packets, is transmitted from the sender's physical layer over the physical medium to the receiver's physical layer.
Interoperability:
The OSI Model promotes interoperability by providing a common framework that different vendors and technologies can adhere to. As long as devices and software follow the specifications of the OSI Model, they can communicate effectively, regardless of their origins.
Data De-encapsulation:
At the receiver's end, the data goes through a process of de-encapsulation. Each layer removes its header and trailer, leaving the original data from the application layer.
Essentially, the OSI Model divides network communication into seven layers, each with specific responsibilities—as explained below—to ensure efficient data transmission and interoperability. Data passes through these layers, undergoing encapsulation and de-encapsulation, as it travels from sender to receiver, allowing for a structured and standardized approach to networking.
The OSI Model serves as a foundational framework in the field of networking, defining the fundamental functions and responsibilities necessary for successful data communication. Comprised of seven distinct layers, this model guides the way data is transmitted, received, and processed across networks. Each layer is designed with specific tasks, and collectively they work together to ensure reliable, efficient, and interoperable communication between devices and systems. In the following section, we will delve into each layer of the OSI Model, providing detailed insights into their functions, protocols, and contributions to the seamless operation of network communication.
Layer 1: Physical Layer
The Physical Layer serves as the foundation of the OSI Model, focusing on the actual transmission of data in its raw bit form over a physical medium. Its essential functions encompass:
Encoding and Signaling:
Encoding bits into electrical or optical signals suitable for the chosen physical medium. For example, it decides how ‘0’ and ‘1’ bits are represented through variations in voltage levels (for copper cables) or light pulses (for optical fibers).
Bit Rate:
Determining the bit rate, which is the speed at which bits are transmitted. It defines how fast data can move over the network, commonly measured in bits per second (bps).
Transmission Media:
Managing the characteristics and properties of the physical medium used for data transmission. This medium can vary widely, including copper wires, fiber-optic cables, radio waves, or even satellite links.
Physical Connectors:
Defining the types of physical connectors and interfaces needed for devices to connect to the network. This includes specifications for cables, plugs, and sockets.
Error Detection and Correction:
Implementing basic error-detection mechanisms to ensure data integrity during transmission. While more advanced error correction is often handled by higher layers, the Physical Layer can include simple parity checks or checksums.
Transmission Modes:
Determining how data is sent between devices—whether it's simplex (one-way), half-duplex (two-way but not simultaneously), or full-duplex (two-way simultaneously).
Transmission Distance:
Setting limits on the distance data can travel over the physical medium before it needs to be boosted or regenerated. This is crucial for understanding the reach of a network.
Example Use Cases:
The Physical Layer plays a pivotal role in various networking scenarios, including high-speed data centers, telecommunications networks, wireless communication systems, and home Wi-Fi networks. It ensures that data is transmitted reliably and efficiently over diverse physical media, optimizing network performance and integrity.
Layer 2: Data Link Layer
The Data Link Layer sits just above the Physical Layer and plays a pivotal role in network communication. Its primary responsibilities include framing data for transmission and managing MAC addresses for efficient and reliable data exchange.
Framing:
One of the key functions of the Data Link Layer is to divide the stream of bits received from the Physical Layer into manageable frames. A frame is a structured unit of data, often with a header and trailer, that encapsulates the actual data along with control information. Framing helps in delineating the boundaries of data packets, allowing devices to recognize the start and end of each transmission. This process ensures that data is correctly segmented for transmission over the network.
MAC Addressing:
Another vital aspect of the Data Link Layer is the management of MAC addresses. MAC addresses are unique identifiers assigned to network interface cards (NICs) or network adapters. These addresses are used to identify devices on a local network segment. When a device wants to send data to another device within the same network, it uses the recipient's MAC address to direct the frame to the correct destination. The Data Link Layer is responsible for adding the MAC address information to the frame's header.
Network Devices:
The Data Link Layer is crucial for the operation of network devices like switches. Switches operate at this layer and use MAC addresses to determine how to forward frames. When a frame arrives at a switch, it examines the MAC address in the frame's header to make forwarding decisions. This capability enables switches to efficiently direct data only to the specific port where the destination device is connected, minimizing network congestion and enhancing overall network performance.
LLC (Logical Link Control):
The Data Link Layer is further divided into two sub-layers: the Logical Link Control (LLC) sub-layer and the MAC sub-layer. The LLC sub-layer is responsible for managing flow control, error checking, and addressing within the Data Link Layer. It ensures that data is reliably transmitted between devices, handles error detection and correction, and manages communication between devices using various data-link protocols.
Example Use Cases:
Use cases for the Data Link Layer include Ethernet communication within local networks, wireless Wi-Fi connections, point-to-point serial communication, and protocols that ensure data integrity and efficient use of the network medium. It ensures reliable and orderly data exchange, particularly within the local network segment, enhancing network performance and ensuring data integrity.
Layer 3: Network Layer
The Network Layer is the third layer in the OSI Model and serves as a critical component of network communication. Its primary role is to manage the routing of data packets from the source to the destination across multiple networks while maintaining logical addressing and path determination.
Routing Data Packets:
One of the fundamental tasks of the Network Layer is to route data packets from the sender to the receiver. It accomplishes this by determining the most efficient path for data to travel through a complex network topology. Routing algorithms and protocols, such as RIP (Routing Information Protocol), OSPF (Open Shortest Path First), and BGP (Border Gateway Protocol), are implemented at this layer to make routing decisions.
Logical Addressing:
The Network Layer introduces logical addressing, where each device on a network is assigned a unique address known as an IP (Internet Protocol) address. IP addresses, both IPv4 and IPv6, are used for identifying devices and their network location. The Network Layer is responsible for managing these addresses, which are used for source and destination identification in data packets.
Packet Forwarding:
As data packets traverse the network, the Network Layer handles packet forwarding. This involves inspecting the destination IP address in each packet's header and determining the next hop (next network device) on the route to the destination. The Network Layer also manages the encapsulation and decapsulation of data packets for transmission and reception.
Inter-Network Communication:
The Network Layer is crucial for enabling communication between different networks. It acts as the boundary where data moves between local area networks (LANs) and wide area networks (WANs). Routers, which operate at this layer, play a central role in connecting disparate networks and ensuring data can traverse these boundaries.
Error Handling:
While the primary responsibility for error handling lies with higher layers, the Network Layer may perform basic error detection and reporting. If a packet is found to be corrupt or undeliverable, the Network Layer may discard it or request retransmission.
Subnetting:
The Network Layer allows for the division of large IP address spaces into smaller subnetworks or subnets. Subnetting aids in efficient IP address allocation, routing optimization, and network management.
Example Use Cases:
The OSI Network Layer finds diverse applications in networking, notably in routing data packets across the global Internet, handling IP addressing and subnetting within local networks, securing communications through Virtual Private Networks (VPNs), managing Quality of Service (QoS) to prioritize critical traffic types, automating IP address assignment via DHCP, enabling efficient one-to-many communications via multicast routing, and interconnecting private networks over public or dedicated links. It serves as the linchpin for directing data to its destination efficiently, whether within local networks or across vast interconnected infrastructures, ensuring the reliability and security of data transmission.
Layer 4: Transport Layer
The Transport Layer, positioned as the fourth layer in the OSI Model, is primarily responsible for ensuring end-to-end communication and the reliable delivery of data between devices on different hosts across a network. It accomplishes this through various mechanisms, including segmentation, flow control, error detection, and multiplexing.
End-to-End Communication:
The Transport Layer ensures that data reaches its intended destination reliably and in the correct sequence. To achieve this, it assigns a source port and a destination port to each data segment, creating what is known as a “socket.” Sockets—represented as a combination of IP address, source port, and destination port—allow multiple applications to simultaneously communicate on the same device while ensuring that data from different applications is correctly routed to its respective destination.
Segmentation:
One of the key roles of the Transport Layer is to divide large messages into smaller segments, making them easier to transmit across the network. These segments are typically referred to as “packets” or “datagrams.” Segmenting data is especially important when the message is too large to fit into a single network packet.
Flow Control:
Flow control mechanisms are implemented at the Transport Layer to manage the rate of data transmission between sender and receiver. This is crucial to prevent network congestion and ensure that the receiving device can process data at its own pace. Flow control can be achieved through techniques like windowing, where the sender adjusts its transmission rate based on acknowledgments from the receiver.
Error Detection and Correction:
The Transport Layer employs error detection and correction techniques to ensure the integrity of data during transmission. Protocols like TCP (Transmission Control Protocol), a commonly used Transport Layer protocol, include checksums to detect errors in data segments. If errors are detected, TCP requests retransmission of the affected segments to guarantee data accuracy.
Multiplexing and Demultiplexing:
Multiplexing is the process of combining multiple data streams into a single stream for transmission over the network. At the receiving end, demultiplexing separates the combined stream back into individual data streams using the destination port information in the Transport Layer header. This enables multiple applications to use the same network connection simultaneously.
Connection-Oriented vs. Connectionless:
The Transport Layer supports both connection-oriented and connectionless communication. TCP is a connection-oriented protocol that establishes a reliable, bidirectional communication link before data transfer. UDP (User Datagram Protocol), on the other hand, is a connectionless protocol that sends data without prior connection setup, making it faster but less reliable compared to TCP.
Example Use Cases:
Key Transport Layer use cases include the reliable and error-checked transmission of data across networks via protocols like TCP for applications such as web browsing and email. Additionally, the Transport Layer offers connectionless communication through UDP, making it ideal for real-time applications like voice and video conferencing. It manages data segmentation, reassembly, and flow control, ensuring that large files can be transmitted efficiently and without data loss. The Transport Layer also handles port-based addressing, allowing multiple services to run simultaneously on a single device, supporting various applications and facilitating secure data transfer over encrypted connections.
Layer 5: Session Layer
The Session Layer, positioned as the fifth layer in the OSI Model, is responsible for establishing, maintaining, and terminating communication sessions between devices. It plays a crucial role in ensuring that data exchange between applications is synchronized, organized, and reliable.
Session Maintenance:
During an ongoing communication session, the Session Layer oversees its continuity. It manages synchronization between devices, ensuring that data is exchanged in an orderly and predictable manner. This layer also handles error recovery and retransmission of lost or corrupted data if needed, maintaining the integrity of the session.
Session Establishment:
The Session Layer is responsible for initiating communication sessions between devices. This involves setting up parameters for communication, such as session identifiers, authentication, and synchronization points. Session establishment ensures that both sender and receiver are ready to exchange data.
Session Termination:
Once a communication session has concluded or is no longer needed, the Session Layer facilitates its graceful termination. This involves releasing any resources allocated for the session, such as buffers or connections, and ensuring that both parties agree to end the session in a coordinated manner.
Dialog Control:
The Session Layer is responsible for managing the dialog between devices, which involves determining which device can transmit and when. It helps prevent conflicts and ensures that data is exchanged in an organized and coherent manner.
Synchronization Points:
In some applications, the Session Layer establishes synchronization points within the data stream, allowing devices to resume communication from specific points in case of interruptions. This is particularly useful in scenarios where large files are being transferred, and resuming from the last synchronized point reduces data loss.
Checkpointing:
The Session Layer may implement checkpointing, where it periodically saves the current state of the communication session. This enables recovery from unexpected failures by allowing the session to resume from the last checkpointed state.
Example Use Cases:
The Session Layer is particularly relevant in scenarios such as file transfer protocols (e.g., FTP), remote desktop connections (e.g., RDP), and online gaming, where maintaining a synchronized and reliable session is critical for a seamless user experience.
Layer 6: Presentation Layer
The Presentation Layer, positioned as the sixth layer in the OSI Model, is responsible for managing data translation, encryption, compression, and ensuring that data exchanged between applications is in a format that can be understood by both sender and receiver.
Data Translation:
One of the primary functions of the Presentation Layer is to handle data translation and format conversion. This includes tasks like character encoding, where it ensures that characters from different character sets (e.g., ASCII, Unicode) are correctly represented and understood by both communicating devices. It also deals with issues like byte order, making sure that multi-byte data is arranged consistently for devices with different architectures.
Encryption and Decryption:
The Presentation Layer plays a vital role in data security by providing encryption and decryption services. It can encrypt data before transmission, ensuring that sensitive information remains confidential during its journey across the network. Upon receipt, it decrypts the data, allowing the recipient to access the original content.
Data Formatting:
The Presentation Layer also handles data formatting and representation, ensuring that data is structured in a way that can be easily interpreted by the receiving application. For example, it may convert data into a standard format for presentation on a web browser or a word processing application.
Compression:
In scenarios where bandwidth efficiency is crucial, the Presentation Layer can compress data before transmission and decompress it at the receiving end. Data compression reduces the amount of data transmitted over the network, improving transfer speeds and reducing network congestion.
Translation Between Data Formats:
When data is exchanged between applications running on different systems, the Presentation Layer can translate the data between different formats or representations to ensure compatibility. This is particularly important in heterogeneous environments with a variety of software and hardware platforms.
Example Use Cases:
The Presentation Layer is particularly relevant in applications like web browsers, where it translates and renders web content (HTML, images) for display. It's also essential in secure communication, where it handles encryption and decryption of data for confidentiality.
Layer 7: Application Layer
The Application Layer, positioned as the seventh and highest layer in the OSI Model, is the interface between network services and end-user applications. It is the layer closest to the end-users and encompasses a wide range of functions that facilitate communication and interaction between applications and network services.
Application Protocols:
This layer defines numerous application protocols that govern specific types of communication between applications and services. These protocols dictate how data is formatted, transmitted, and interpreted. Common application layer protocols include HTTP (for web browsing), SMTP and POP3/ IMAP (for email), and FTP (for file transfer).
User Interface:
The Application Layer provides the user interface that allows individuals or software applications to interact with network services. This includes applications like web browsers, email clients, instant messaging programs, and more. The user interface ensures that users can input commands, request data, and view responses.
Data Exchange:
The Application Layer is responsible for the exchange of data between applications running on different devices over a network. It ensures that data sent from one application can be correctly received and understood by another application, regardless of their operating systems or hardware platforms.
Data Presentation:
Building on the work of the Presentation Layer, the Application Layer may also handle data presentation and rendering. This includes tasks such as displaying web content, rendering multimedia, or formatting documents for printing.
Security and Authentication:
Security mechanisms, including user authentication and data encryption, are often implemented at the Application Layer to safeguard data and ensure that only authorized users can access certain services or resources.
Example Use Cases:
The Application Layer encompasses a wide array of applications and services, ranging from web browsers, email clients, and remote desktop software to online gaming platforms, file sharing tools, and more. Essentially, any software that relies on network communication falls within the domain of the Application Layer.
The OSI Model's relevance in networking lies in its ability to serve as a universal reference framework. Here's why it's crucial:
Layered Approach:
The model breaks down network communication into discrete layers, making it easier to design, develop, troubleshoot, and maintain network protocols and systems.
Standardization:
It offers a standardized way to discuss and understand network communication. This standardization simplifies communication between different vendors and technologies.
Interoperability:
By defining clear boundaries and responsibilities for each layer, the OSI Model promotes interoperability. Devices and software developed independently can communicate effectively if they adhere to the model's specifications.
Troubleshooting:
When network issues arise, the model helps in pinpointing the layer at which the problem exists. This aids network administrators and engineers in diagnosing and resolving issues efficiently.
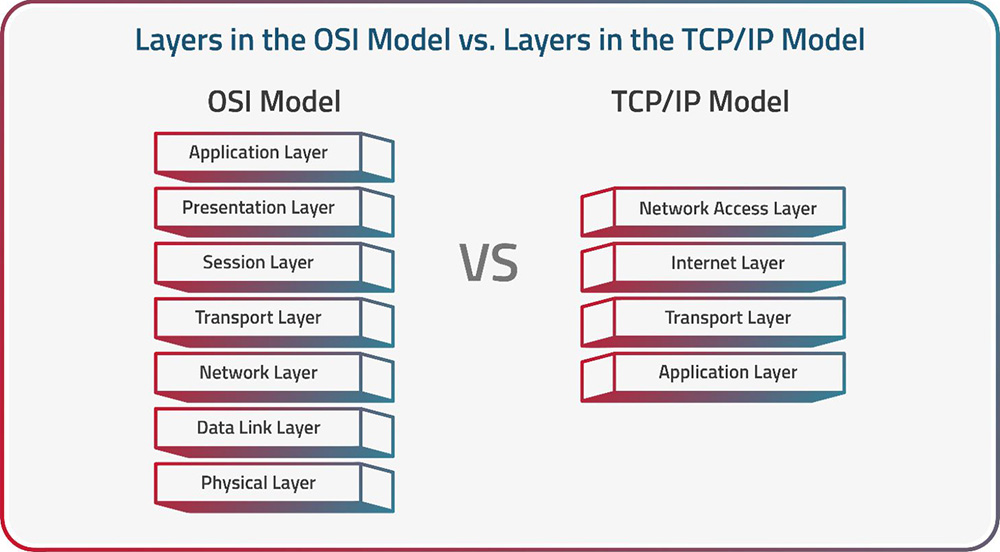
The OSI Model and the TCP/IP Model are two fundamental frameworks used to conceptualize and understand network architecture and communication. While both models serve as guides for designing and troubleshooting networks, they differ significantly in their approach.
The OSI Model, with its seven-layer structure, offers a comprehensive and highly structured view of networking concepts, promoting interoperability and clear separation of concerns. In contrast, the TCP/IP Model, with its four-layer structure, mirrors the practical implementation of the Internet, simplifying the model for real-world network communication. This simplification, however, can come at the cost of some of the comprehensive structure found in the OSI Model, making each model suitable for different networking contexts.
Pros and Cons of the OSI Model compared with the TCP/IP Model:
| |
OSI MODEL |
TCP/IP MODEL |
| PROS |
- Comprehensive framework for networking. |
- Reflects practical Internet implementation. |
| |
- Divides networking into seven layers. |
- Simplifies the model with four layers. |
| |
- Promotes interoperability. |
- Corresponds closely to the Internet structure. |
| |
- Offers clear separation of concerns between layers. |
- Streamlined framework for real-world networking. |
| CONS |
- Can be overly complex for practical use. |
- Lacks comprehensive structure in some areas. |
| |
- Not all real-world protocols align with all layers. |
- May lack clear delineation for specific functions. |
Radware's solutions seamlessly integrate with various OSI model layers to provide enhanced network and application security to protect against threats and vulnerabilities. Below are a few examples—in the context of the OSI Model—of how Radware solutions help enhance network and application security:
Transport Layer Protection:
Scenario: An e-commerce platform experiences slow performance due to a high volume of bot-generated traffic on its payment gateway.
Radware Solution: Radware Bot Manager, operating at Layer 4, employs device fingerprinting to distinguish between legitimate users and malicious bots. By identifying and blocking bot-generated requests at the transport layer, it safeguards the payment gateway from fraudulent activities.
Network Layer Protection:
Scenario: A company's network faces repeated DDoS attacks targeting the routing infrastructure, causing network disruptions.
Radware Solution: Radware's DDoS protection solutions, operating at Layer 3, use advanced traffic analysis techniques to detect and mitigate DDoS attacks in real time. By identifying and diverting malicious traffic away from critical network resources, these solutions ensure uninterrupted network availability.
Application Layer Protection:
Scenario: A healthcare provider's web application handles sensitive patient data, making it a target for cyberattacks.
Radware Solution: Radware's Application Security solutions, operating at Layer 7, provide comprehensive protection against application-layer attacks such as SQL injection and cross-site scripting (XSS). By examining application traffic patterns and using device fingerprinting, these solutions identify and block malicious activities, ensuring the security and privacy of patient data.
Secure Remote Access - Across OSI Layers:
Scenario: A financial institution needs to provide secure remote access for employees working from various locations.
Radware Solution: Radware's remote access solutions, operating across OSI layers, use device fingerprinting to ensure that only authorized and secure devices can access the institution's network. By examining device attributes and behavior, these solutions enhance security during remote access, regardless of the OSI layer.
Client Reputation - Across OSI Layers:
Scenario: An online gaming platform faces challenges with user accounts engaging in suspicious or cheating behavior.
Radware Solution: Radware's Client Reputation solution, spanning OSI layers, assesses the reputation of incoming clients based on their behavior and device characteristics. This multi-layer approach, including device fingerprinting, helps in identifying and taking action against users with a history of cheating or fraudulent activities.