Organizers of a new botnet made up of infected home and small office routers are brazenly selling denial-of-service attacks of once unimaginable volumes for just $20 per target.
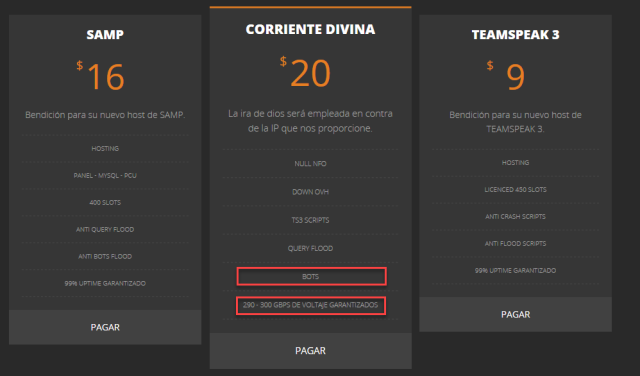
Calling itself Los Calvos de San Calvicie, the group is advertising several services on this site. Among the services are distributed denial-of-service attacks of 290 to 300 gigabits per second for $20 each. While a third the size of some of the biggest recorded attacks, 290Gbps is still enough to bring most sites down unless they seek DDoS mitigation services, which in many cases cost considerable amounts of money. Just five years ago, 300Gbps was considered enough volume to shut down the Internet's core infrastructure.
Unlike most of the IoT botnets seen so far, the one tracked by Geenens, which he's calling JenX, uses a handful on non-IoT servers to scan the Internet for vulnerable devices and, once found, to exploit them. That makes it much harder to estimate the number of infected devices that make up JenX, because the simulated vulnerable routers Geenens uses in his laboratory to track the botnet see the same limited number of attack servers.
By contrast, Mirai, Satori,
Reaper, and other IoT botnets rely on infected devices to locate and infect vulnerable devices. That allows honeypots such as Geenens' to estimate the size of the botnet based on the number of IPs doing the scanning. JenX gets its name from "Jennifer," the name the malware developers gave to the binary that infects vulnerable devices.
Devine Stream
Geenens said the main purpose of the botnet is to attack people playing the online game Grand Theft Auto on certain fee-charging servers. That in turn can increase demand for game hosting by sancalvicie.com. That's the same domain hosting the JenX command-and-control server. It advertises itself as being resistant to the types of attacks Mirai and JenX use to bring down rival game hosts. It's also the same domain advertising the DDoS-for-hire services, which appear to be a side business to the game hosting.
The Spanish-speaking group has dubbed its DDoS service Corriente Divina, which translates to "divine stream." A rough English translation of the service tag line is "God's wrath will be employed against the IP that you provide us."
The group offers source query engine floods and 32-byte floods, which are types of DDoS attacks that are particularly effective at bringing down many types of multiplayer gaming services. The DDoS service also includes a "Down OVH" option, a likely reference to the France-based hosting provider that's known for hosting servers for multi-player games, including Minecraft. OVH was a target in the 2016 attacks waged by botnets including Mirai, which pummeled the cloud provider with 1.1 terabits per second of junk traffic, a record at the time. Ironically, over the past few days, the Jennifer binary delivered to exploited routers was hosted on an IP address belonging to OVH, Geenens said.
JenX is an example of the second generation of IoT botnets. Like Mirai, it preys on the vast number of unsecured routers, cameras, and other network-enabled devices populating the Internet. That supply gives the botnets formidable amounts of distributed bandwidth that have the collective ability to cripple large swaths of the Internet. One weakness in Mirai, however, was its reliance on default passwords to take control of devices. Once the passwords are changed—either by manufacturers or device owners—Mirai becomes ineffective.
JenX, Satori, Reaper, and other second-generation IoT botnets have gotten around this limitation by exploiting firmware vulnerabilities in Internet-connected devices. The infection mechanism is potentially much more effective because most IoT devices run Linux-based firmware that's generally out of date by the time of shipping. Many devices can't be updated at all. Many others that can be updated are prohibitively difficult for most people to do. That leaves the second-generation IoT botnets with millions of devices to take over using reliable exploits that are often available online.
JenX is different from most IoT botnets, because, as mentioned earlier, it relies on centralized servers to seek out and exploit vulnerable devices. That means its rate of growth is likely to remain constant. In an email, Geenens wrote:
The potential for this botnet is comparable to Satori as it uses the exact same exploits. However, the growth rate of this bot will not be as high as Satori because Satori is using bots that each scan and exploit by themselves—so more bots, more scanners, more victims, even more bots, even more scanners, etc…. so exponential growth rate for the Mirai, Satori and Reaper botnets. The JenX botnet uses servers for the scanning and exploiting devices, so growth will be less than linear. By adding more servers they can make it grow faster, but never will be as efficient and aggressive as Mirai, Satori and Reaper.
Geenens has published a full report of his latest findings here.
At the time this post was going live, Geenens told Ars that abuse teams at Leaseweb Netherlands and Leaseweb Germany took down some of the JenX exploit servers that had been hosted in their datacenters. Geenens said that the C&C server remains operational, as do other exploit servers.
"This is only sending them the message that they need to get better at hiding from us," the researcher wrote in an email, referring to the JenX operators. "It is not that easy to take down a skilled hacker group—they are learning from their mistakes now. They might bring their operation over to the darknet, which is another benefit of using centralized exploit servers."