What Is Cyber Threat Intelligence?
Cyber threat intelligence is based on the collection of data from multiple sources for research and analyzing threats so that organizations can be prepared to identify and mitigate cyberattacks. This means collecting and researching data associated with criminal organizations and hacktivist to create actionable insight.
One of the ways Radware’s Threat Research Center (TRC) does this is through a network of high and low interaction honeypots. These honeypots allow our TRC to monitor criminal activities, analyze their methods and learn how to defend against attacks.
The TRC researches botnet activity and the malware used by bot herders. One of the main priorities for the TRC is to provide preemptive protection against DDoS attacks. We accomplish this via threat intelligence and real-time analysis of the collected data.
Data Points
An autonomous systems number (ASN) is an identifier for a collection of networks under the control of an entity. For example, 14061 is the ASN number that identifies DigitalOcean. When analyzing attack traffic flagged as Mirai, the ASN can give us insight into the to the infrastructure leveraged by bot herders, both for the scanners used to locate vulnerable devices and their command and control servers. Below is a chart listing the top scanners by ASN for a single week in July.
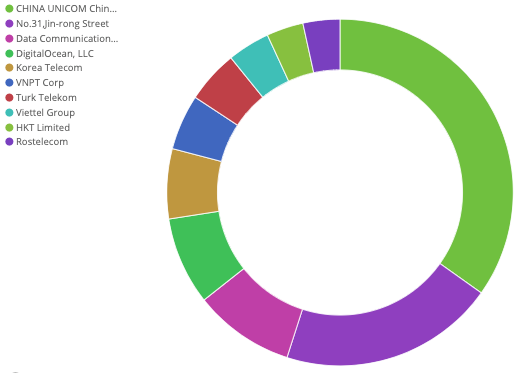
Figure 1: Top ASN - Flagged Mirai Traffic