Radware’s Threat Research Center is monitoring and tracking a malicious agent that is leveraging a Hadoop YARN unauthenticated remote command execution to infect Hadoop clusters with an unsophisticated new bot that identifies itself as DemonBot.
Download Complete Alert
Abstract
Radware’s Threat Research Center is monitoring and tracking a malicious agent that is leveraging a Hadoop YARN unauthenticated remote command execution to infect Hadoop clusters with an unsophisticated new bot that identifies itself as DemonBot.
Background
Hadoop is an open source distributed processing framework designed to manage storage and data processing for big data applications running in clustered systems. Recently, Radware's Threat Research Center began tracking a malicious actor(s) exploiting a known Hadoop Yet-Another-Resource-Negotiator (YARN) vulnerability that allows an attacker to run unauthenticated remote command executions against Hadoop servers.
A proof of concept (POC) code for this vulnerability was first published on GitHub in March of this year. YARN is a prerequisite for Hadoop and provides cluster resource management allowing multiple data processing engines to handle data stored in a single platform. This vulnerability stems from YARN exposing a REST API that allows remote applications to submit new applications to the cluster.
DemonBot
DemonBot was recently identified after a spike in requests for /ws/v1/cluster/apps/new-application appeared in our Threat Deception Network. Our deception network recorded multiple attempts for /ws/v1/cluster/apps/new-application, slowly starting at the end of September and growing to over 1 million attempts per day throughout October.
 Figure 1: Attempts for /ws/v1/cluster/apps/new-application
Figure 1: Attempts for /ws/v1/cluster/apps/new-application
The number of unique IPs from where the requests originated from grew from a few servers to over 70 within the last week.
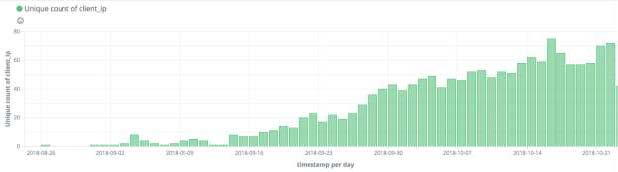 Figure 2: Unique IPs
Figure 2: Unique IPs
DemonBot spreads only via central servers and does not expose worm-like behavior exhibited by Mirai-based bots. Currently, Radware is tracking over 70 active exploit servers that are actively spreading DemonBot and are exploiting servers at an aggregated rate of over 1 million exploits per day. DemonBot is not limited to x86 Hadoop servers and is binary compatible with most known IoT devices, following the Mirai built principles. This is not the first time that cloud infrastructure servers have been targeted. Earlier this month, security researcher Ankit Anubhavi discovered a hacker leveraging the same Hadoop YARN bug in a Sora botnet variant.
*Note that though we did not find any evidence that DemonBot is actively targeting IoT devices at this time.