While record-breaking volumetric DDoS attacks flash in the headlines, low profile Denial-of-Service attacks continue to hit business worldwide.
Download a Copy Now
Abstract
While record-breaking volumetric DDoS attacks flash in the headlines, low profile Denial-of-Service attacks continue to hit business worldwide. Radware’s Emergency Response Team has battled over 385,000 HTTP flood attacks launched across the world. HTTP flood is one of the hackers’ favorites when it comes to causing a business disruption, as they are much harder to block (compared to a typical Layer 3 and Layer 4 network attack) and are prevalent - dozens of HTTP flood tools are available to the community and are constantly being improved. The majority of those tools leverage botnets for rent (DDoSaaS or Stresser services) that include HTTP flood attacks as part of their offering.
Attack Methods
An HTTP flood is an attack method used by hackers to attack web servers and applications. These floods consist of seemingly legitimate session-based sets of HTTP GET or POST requests sent to a targeted web server. HTTP flood attacks do not use spoofing, reflective techniques or malformed packets. These requests are specifically designed to consume a significant amount of the server’s resources, and therefore can result in a denial-of-service. Such requests are often sent en masse by means of a botnet, increasing the attack’s overall power. HTTP and HTTPS flood attacks are one of the most advanced threats facing web servers today since it’s very hard for network security devices to distinguish between legitimate HTTP traffic and malicious HTTP traffic.
HULK
HULK stands for HTTP-Unbearable-Load-King. It’s an HTTP denial-of-service tool that has been around for several years. This tool, written in Python, is able to generate unique HTTP requests that are designed to stress test web servers against resource exhaustion (see Figure 1). HULK generates unique requests based on the user agent/referrer strings. By requesting the HTTP server for no cache, the server presents a unique page for each request. The tool bypasses caching engines and hits the server directly. Since its release, several actors have optimized and republished this code to include more user agents and referrers in an attempt to generate more randomized requests while launching an attack.
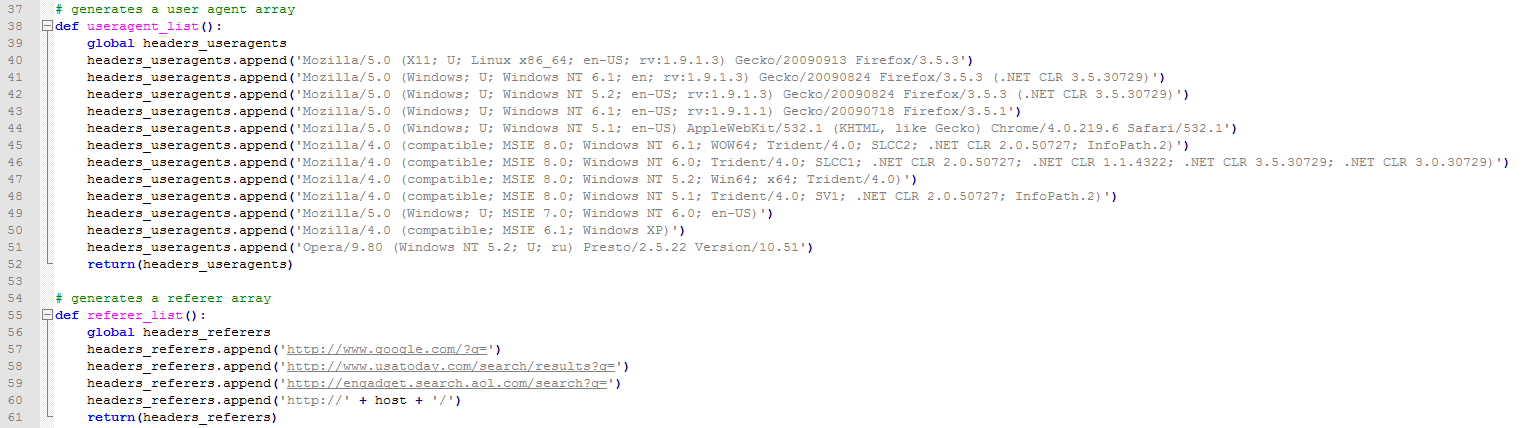
Figure 1: Original HULK code
TorHammer
Tor's Hammer is a slow-rate HTTP POST (Layer 7) DoS tool. This tool executes a DoS attack by using a classic slow POST attack where HTML POST fields are transmitted in slow rates under the same session. Similar to the former R.U.D.Y. (R-U-Dead-Yet) tool, the slow POST attack causes the web server application threads to await the end of boundless posts in order to process them. This causes the exhaustion of the web server resources and causes it to enter a denial-of-service state for any legitimate traffic.
DoS attacks via TorsHammer can be carried out via the Tor Network by using a native socks proxy integrated in Tor clients. This enables launching the attack from random source IP addresses, which makes tracking the attacker almost impossible (see Figure 2).
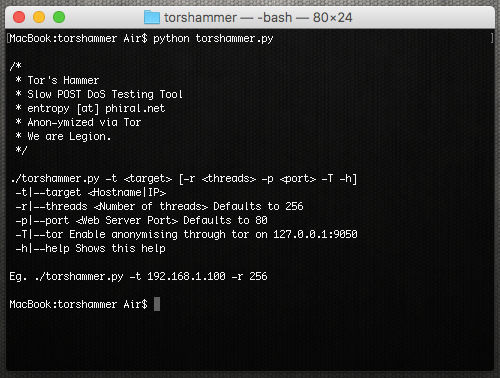
Figure 2: TorsHammer interface
Saphyra
Saphyra is a HULK variant that has been used in several Anonymous operations throughout 2016. It includes over 3200 unique user agent strings and over 300 unique referrer field strings resulting in the possibility of over one million unique requests generated during an attack (see Figure 3). This combination of user agents and referrer instances makes it very difficult for most DDoS protection solutions (in particular rate-limiting technologies) to identify patterns in the attack traffic.
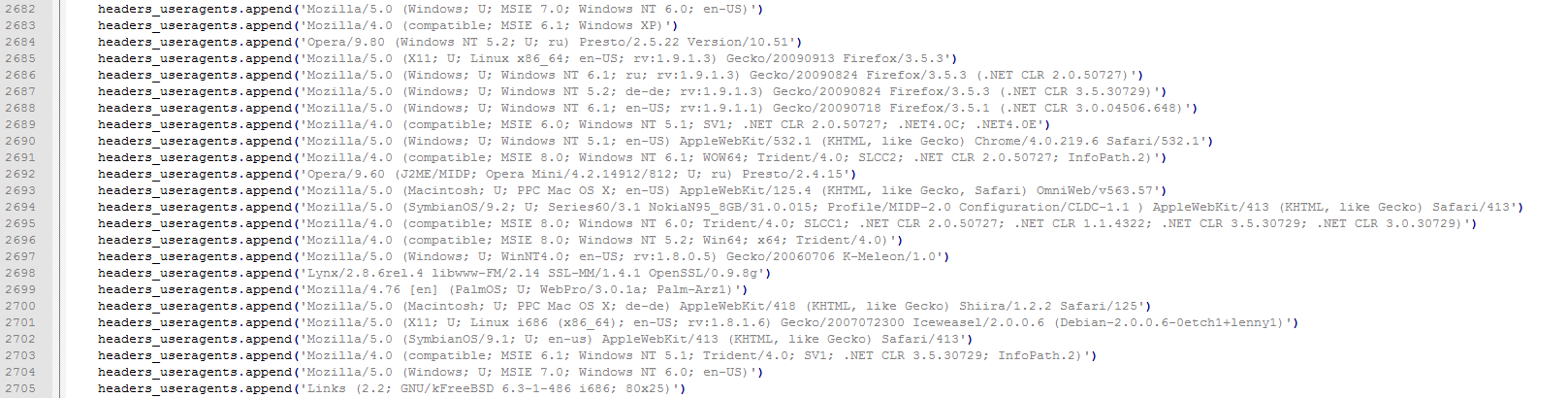
Figure 3: Saphyra – User agents strings in script
ExoFlood
ExoFlood is another HULK variant that has recently been published via Twitter. ExoFlood is very similar to Saphyra in the terms of user agents and referrer strings, and features over 4000 unique user agents and over 500 referrer stings resulting in event more unique request being generated by this tool (see Figures 4 and 5).
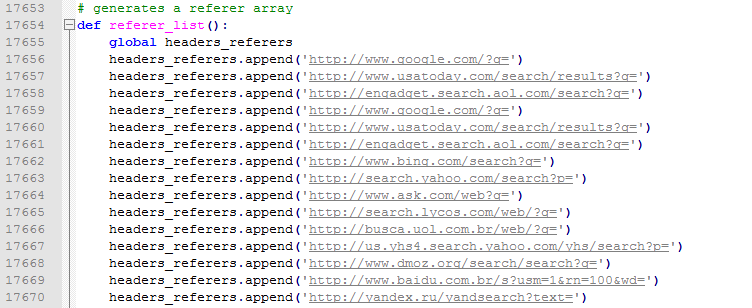
Figure 4: ExoFlood – Referer strings in the script
Figure 5: Attacker releasing ExoFlood
Reasons for Concern
Attackers are slowly moving away from easy-to-mitigate reflective attacks and starting to leverage simpler and defensively complex tools such as Layer 7 HTTP and HTTPS flood attacks. HTTP flood attacks are some of the most advanced cyber security threats to web servers. These attacks are hard to distinguish between legitimate and malicious traffic, creating a challenge to rate-based detection solutions.
Low and slow attacks use slow traffic that appears to be legitimate HTTP requests to pass traditional detection and mitigation systems undetected. In addition, these tools also keep a persistent foothold in the system by sending a standard HTTP command keep-alive to force the server to maintain the open connections.
All of this prevents servers’ protection controls from recognizing a pattern and filtering out the attack traffic. The real concern is that these tools can be used on almost any device from laptops and tablets to desktops and cloud instances controlled via a cellphone.
How to Prepare
HTTP flood attacks will continue to grow in popularity as more tools become available and those using the tools modify them in more complicated ways to defeat mitigation techniques. We are also seeing more attackers attempting to leverage HTTPS floods as the tools become more popular and widely available. There are several ways Radware can help mitigate Layer 7 attacks. By responding to the request and verifying the correct network behavior from the source, identifying repeating patterns in the traffic headers, and rate limit based on traffic parameters, we can help keep your network and application online.
DDoS Protection Considerations for Organizations Under Threat
- Hybrid DDoS Protection – on-premise and cloud-based anti DDoS protection solutions for real-time protection that also addresses high volume attacks and protects from pipe saturation.
- Behavioral-Based Detection - to quickly and accurately identify and block anomalies while allowing legitimate traffic through.
- Real-Time Signature Creation - to promptly protect from unknown threats and zero-day attacks.
- Cyber-Security Emergency Response Plan - that includes a dedicated emergency team of experts.
Radware urges companies to inspect and patch their network in order to defend against risks and threats.
Under Attack and in Need of Expert Emergency Assistance? Radware Can Help.
Radware offers a DDoS service to help respond to security emergencies, neutralize the risk and better safeguard operations before irreparable damages occur. If you’re under DDoS attack or malware outbreak and in need of emergency assistance, Contact us with the code "Red Button".