Malicious actors aren't the only ones who scan the internet. Many researchers and cyber threat intelligence organizations continuously scan the internet to discover vulnerable services to help them assess the risk associated with new vulnerabilities.
Read the Complete Alert
Overview
A micro flood is a flood of unsolicited packets with throughputs below 1Gbps. The goal of a micro flood is not always a denial-of-service attempt. In some cases, the origin of the floods is what we refer to as the grey noise of the internet: port and vulnerability scans. The number of micro floods in Radware’s Cloud DDoS Protection Service has increased significantly in 2022, while mid-sized and large-size floods increased only mildly compared to earlier years.
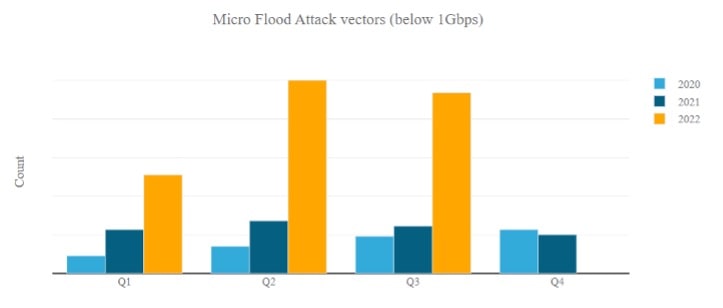 Figure 1: Number of micro floods per quarter (source: Radware DDoS & Application Threat Analysis Hub)
Figure 1: Number of micro floods per quarter (source: Radware DDoS & Application Threat Analysis Hub)
The Grey Noise Of The Internet
In March 2021, Radware issued a threat advisory about the ProxyLogon zero-day exploits in Microsoft Exchange server. In June 2021, Radware published another threat advisory about actors actively scanning for critical remote command execution (RCE) vulnerabilities in VMWare vCenter servers. In both advisories, Radware observed scanning activity to discover exposed and vulnerable servers only a few hours after a proof of concept for the vulnerability was published. The window between public disclosure and active exploitation of vulnerabilities is shrinking fast, leaving organizations with little time to update or patch their systems.
Malicious actors aren't the only ones who scan the internet. Many researchers and cyber threat intelligence organizations continuously scan the internet to discover vulnerable services to help them assess the risk associated with new vulnerabilities. Organizations such as Shodan, Censys and ZoomEye turned their scanning activities into a service that allow anyone to query specific IP addresses for open ports, services and vulnerabilities or find a list of exposed servers based on specific vulnerabilities.
While it can be useful for organizations to perform periodic assessments of their attack surface, most prefer to keep scanners at bay and block any probes for known vulnerabilities or DDoS reflection and amplification vectors. Well-intended and disclosed scanners can be identified through a DNS reverse lookup on the source IP of the scanner. If the IP has a PTR DNS record, the domain part of the hostname of the scanning server will reveal the originator of the scan and the website associated with the domain might provide more details about the intent and in some cases, an option to opt-out of any future unsolicited scanning activities.
RECYBER.NET
Recyber.net claims to be a project that assists researchers, universities and other educational institutions. The project scans the internet for open ports, and in some cases, vulnerabilities. This actor is anonymous, non-communicative and performs extensive scans. Therefore Recyber.net cannot be confirmed as benign. Several sources on the internet are complaining about the intensity of the scanning performed by Recyber.net (GreyNoise Trends, Another Legitimate Scanner Testing User Patience? Let's talk about Recyber. (threatstop.com), Many Blocks From the ReCyber Project. : firewalla (reddit.com)).
In the last few weeks, Recyber.net is generating a load of 600,000 to 800,000 packets per day, across an average of 120 sensors. The scans are evenly spread across the globe and all sensors, meaning that it is most probably, as it claims, an internet open port and vulnerability scanner. The unsolicited load reaches, on average, up to 6,667 packets per day per sensor. This average does not account for outliers and peaks reaching several billion packets per day.
On several occasions, since April 2022, the Radware DDoS Cloud Protection Service blocked over 1 billion packets per day originating from Recyber.net hosts. On Sept 24, 2022, Radware DDoS Cloud Protection Service blocked close to 3.5 billion packets. Before April, the activity was much lower, amounting to several tens of thousands of packets per day, with two outliers reaching 10 and 20 million packets per day on August 28, 2021 and March 23, 2022, respectively.
Between October 1st and November 14, 2022, Recyber.net scanning activity has been taxing internet services with an average bandwidth of 6Mbps, peaking at 36Mbps and a 95th percentile of 16Mbps while packet rates averaged at 12kPPS peaking at 70kPPS and a 95th percentile of 30k PPS.
The ERT Active Attacker Threat Intelligence Feed blocked almost 75% of all scans. About 20% of the scans were detected and blocked by DefensePro through behavioral analysis, categorized as ‘horizontal TCP scanning’ and ‘random TCP scanning’ activity. In addition, between Oct 15th and 21, 2022, a total of 531,000 HTTP scans originating from Recyber.net were blocked by a signature detecting an anomalous User-Agent.
The Recyber.net IP addresses ranging between 89.248.163.0 and 89.248.165.255 are all allocated under the IP Volume Inc autonomous system (AS202425).
IP VOLUME INC
The IP Volume Inc IP address ranges host several global internet scanners, including Shodan.io, Openportstats.com, Criminalip.com and Recyber.net. A good amount of IP addresses from IP Volume are believed to be aggressively scanning the internet. The number of scans per day kept increasing since August 2021 from several hundred packets per day to an average of about 800,000 packets per day by October 11th, and a peak of 2 million packets per day on May 18, 2022.
IMPACT AND MITIGATION
The events have the characteristics of scans, but their aggressive nature leads to potential impacts comparable to DDoS attacks attempting to constrain the resources of servers and network equipment. Radware DDoS Cloud Protection Service customers are protected by our infrastructure that detects and blocks scanning activity as either a known active attacker or leveraging network behavioral and signature-based detections. The ERT Active Attackers Feed accounted for over 83% of all blocked scanning attempts.