On June 27, 2017, a global ransomware targeting computers around the world with a new variant referred to as NotPetya.
Download a Copy Now
This post discusses active research regarding the Petya threat. Radware’s ERT research team is conducting ongoing research of this evolving malware endemic.
This is a preliminary report and will be updated accordingly.
Abstract
On June 27, 2017, a global ransomware campaign targeting computers around the world with a new ransomware variant referred to as NotPetya1 2 (also in use - Nyetya, GoldenEye). This attack comes just one month after the WannaCry outbreak infected computers in over 100 countries.
This campaign has already targeted several countries around the world, including Ukraine, Russia, Denmark, Spain, India, Germany, United Kingdom, United States and France.
Those that were infected include individuals to large corporations like financial institutions, utility companies, an airport, media outlets, transportation and a hospital. Organizations that were struck include Ukrainian government institutions, Merck, Deutsche Post, Maersk, Rosneft, and others.
Despite the extortion demand, analysis of this new version of Petya appears to support the fact that it is designed to wipe out data on infected computers/networks, leaving it useless and inoperative. This threat advisory provides an overview of the threat, how it operates, how it spreads, and mitigation measures.
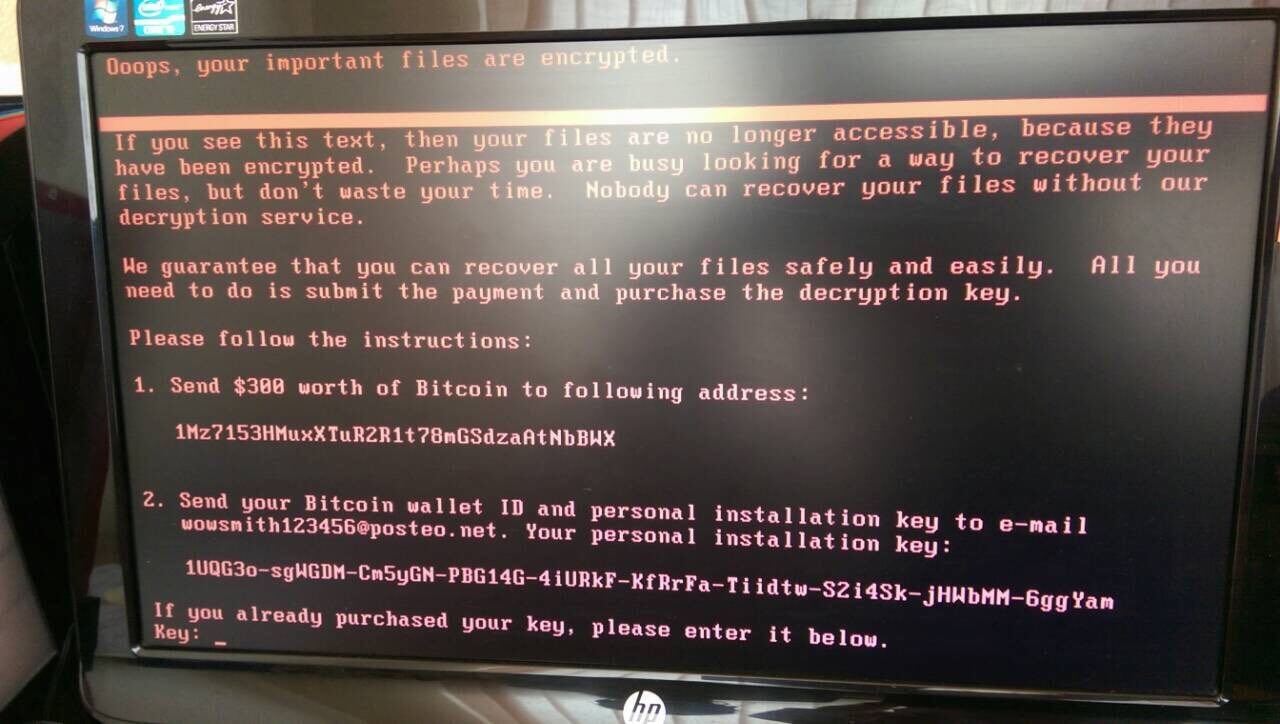
Figure 1: NotPetya infected computer – Source Hromadske.ua
The Evolution of Petya Ransomware
In 2016, the ransomware programs Petya and Mischa emerged as part of an ongoing Darknet trend: ransomware affiliate programs. Its creators – allegedly a group who go by the name “Janus Syndicate” - offered their Ransomware-as-a-Service (RWaaS) on a Tor Hidden Service. It was created for the purpose of ransom attacks.
Operation Mode
Petya was different from other ransomware variants because the malware did not target files on a victim’s computer but instead targeted the Master File Tree tables (MFT) and the Master Boot Record (MRB) with a custom bootloader. The bootloader displayed a ransom note and prevented the system from ultimately booting.
After security researchers published a way to recover files from Petya, a new variant appeared, referred to as “GoldenEye.” This variant included an additional payload, Mischa. Mischa is a backup payload in the event Petya cannot gain administrative privileges and access the Master Boot Record. In this case, Mischa is deployed to encrypt files on the system (see Figure 2).
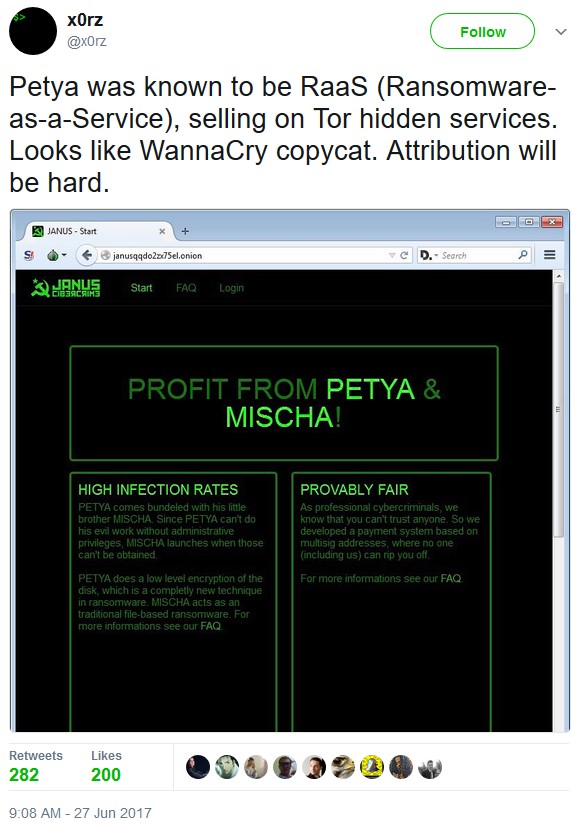
Figure 2: Petya & Mischa RWaaS on the Darknet
File types Mischa can encrypt:
.3ds .7z .accdb .ai .asp .aspx .avhd .back .bak .c .cfg .conf .cpp .cs .ctl .dbf .disk .djvu .doc .docx .dwg .eml .fdb .gz .h .hdd .kdbx .mail .mdb .msg .nrg .ora .ost .ova .ovf .pdf .php .pmf .ppt .pptx .pst .pvi .py .pyc .rar .rtf .sln .sql .tar .vbox .vbs .vcb .vdi .vfd .vmc .vmdk .vmsd .vmx .vsdx .vsv .work .xls .xlsx .xvd .zip.
In the current attack, the new Petya variant (NotPetya or Nyetya3) is being used to control the reboot and the files for ransom purposes. To propagate, NotPetya leverages a spreading mechanism which is similar to what we saw during the WannaCry outbreak.
Propagation
NotPetya has three different ways of propagating and moving laterally across networks once a machine is infected. The malware scans for vulnerable machines in the LAN and uses the EternalBlue exploit as well as Windows administration components such as Psexec and WMI to infect other devices in the network. NotPetya shares code with Mimikatz4 and features a password-harvesting tool that gathers credentials from infected machines. It then hands off the credentials to Psexec and WMI and attempts to infect other machines in the network. For efficient propagation, NotPetya also leverages EternalBlue to infect systems that have not patched Microsoft’s security update, MS17-010. Unlike WannaCry, NotPetya does not appear to have an external scanning element.
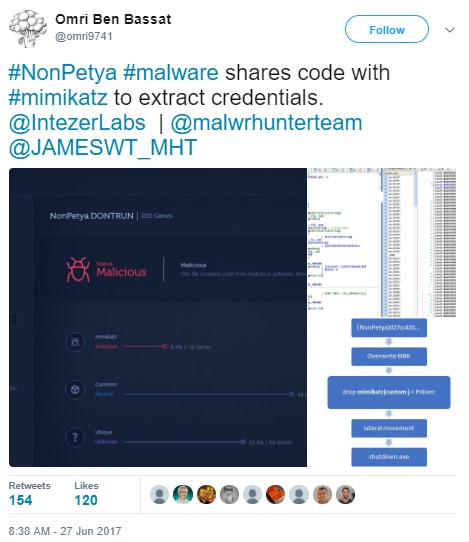
Figure 3: NotPetya appears to be sharing code with mimikatz
Origin
Some reports suggest that the ransomware campaign may have originated from a malicious software update from MeDoc5. MeDoc is a popular accounting & workflow software from the Ukraine. MeDoc denies that they were the cause of the attack6.
Figures 4 & 5: Ukrainian police statements regarding MeDoc
This hypothesis, however, does not explain how Petya got into the networks of corporations in Western Europe and the United States. Others believe the Janus group may be behind this campaign and driven by financial gain. On the contrary, some speculate that the Petya attack was not financially motivated, pointing at the relatively poor payment process, only one hardcoded BTC wallet, no command and control server, and a single point of contact via a public email that was eventually blocked by the host. These facts, combined with analysis of the campaign, underscores the belief that this campaign was not financially motivated, but was intended to cause as much damage as possible by corrupting data and preventing access to information.
Results
In this campaign, victims who are infected are instructed to make a payment of $300 to a hardcoded BTC wallet found in the ransom note. The victim is expected to email the attacker with the transaction ID of the payment to receive their decryption key. The service provider Posteo7 ultimately shut down the email address displayed in the ransom note, wowsmith123456@posteo.net. Shutting down this email address makes it impossible to communicate with the authors or attempt to make a payment in exchange for the decryption keys if possible. There was only one Bitcoin address associated with this campaign, 1Mz7153HMuxXTuR2R1t78mGSdzaAtNbBWX8. At the time of writing there have been thirty payments received totaling $7,705.
What's Expected Next
Extortion is not new to humanity, and the cyber space is fertile grounds for it to prosper. The frequency of ransom attacks doubled the past year, but 2016 was the year where it became the primary motivation of cyber-attacks, particularly in Europe. In 2016, 49% of organizations reported having suffered either a ransomware infection or a DDoS threat for ransom.
It is likely that as this trend continues, hackers will continue to customize new delivery methods for ransomware and more permutations will appear. It was just over a month ago when the WannaCry outbreak began leveraging the EternalBlue exploit.
Recommended Precautions
- Do not pay ransom!
- Use backups for quick restoration
- Patch Microsoft CVE’s MS-17-010
- Update AV and IPS malware signatures
- Block port 445 for external communication
- Implement private vLANs in your network switch so internal traffic only goes from endpoints to the servers (and back), and not between endpoints.
Under Attack and in Need of Expert Emergency Assistance? Radware Can Help.
Radware offers a DDoS service to help respond to security emergencies, neutralize the risk and better safeguard operations before irreparable damages occur. If you’re under DDoS attacks or malware outbreak and in need of emergency assistance, Contact us with the code "Red Button".
1 https://virustotal.com/
2 https://www.hybrid-analysis.com/
3 http://blog.talosintelligence.com/
4 https://twitter.com/
5 https://www.bleepingcomputer.com/
6 https://www.facebook.com/medoc.ua/
7 https://posteo.de/blog/
8 https://blockchain.info/