Switzerland has been the target of a wide-range of DDoS and Ransom Denial of Service (RDoS) attacks over the past week, resulting in network outages and the website for Swiss Federal Railway (SBB) going offline. Additionally, two of the country's largest retailers, Coop and Migros, had their websites taken down, preventing customers from accessing their sites.
Download a Copy Now
Abstract
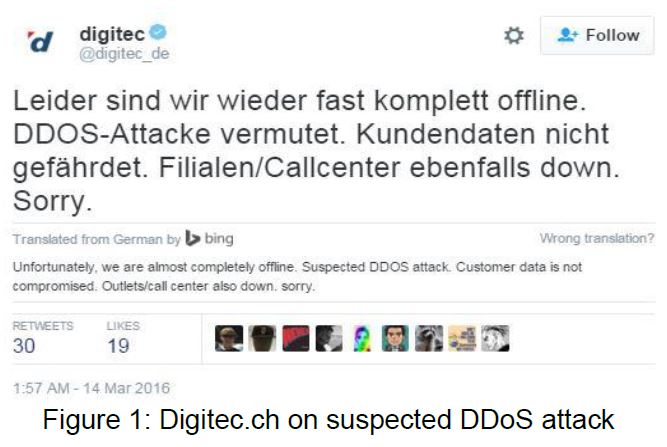
Switzerland has been the target of a wide-range of DDoS and Ransom Denial of Service (RDoS) attacks over the past week, resulting in network outages and the website for Swiss Federal Railway (SBB) going offline. Additionally, two of the country's largest retailers, Coop and Migros, had their websites taken down, preventing customers from accessing their sites (see figure 1). Swiss financial service companies were also blackmailed and threatened via a DDoS attack unless a ransom was paid, according to local news websites. To date, one victim has paid the ransom.i
Background
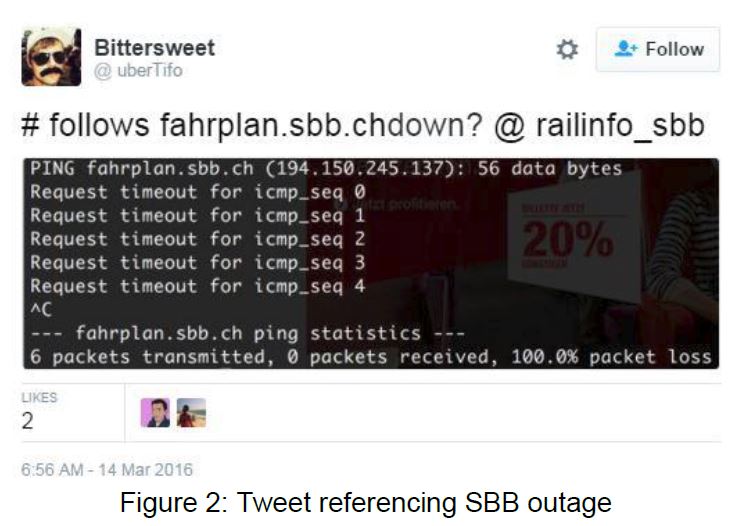
A number of Swiss online retailers and the Swiss Federal Railway (SBB) experienced a series of network outages since Saturday, March 12, due to attacks. These attacks persisted throughout the week for several companies, including InterDiscount and Microspot. On March 17, both InterDiscount and Microspot came back online after prolonged outages.
InterDiscount, Microspot and SSB have acknowledged that they had experienced a denial of service attack.
"It is correct that our Webshop did not work for a short time. We currently believe that it was a DDoS attack. We can confirm that the customer data is safe and not affected. The shop is now again," said Nadine, Media Spokesperson at Interdiscount.
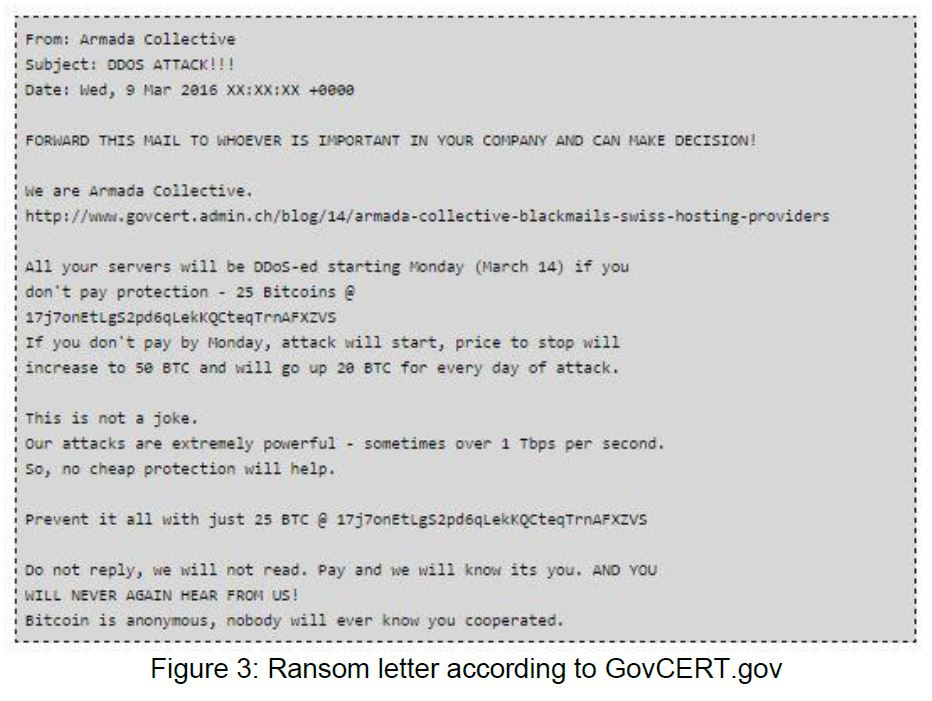
On Friday, March 11, the Swiss Governmental Computer Emergency Response Team issued an alert suspecting the Armada Collectiveii was responsible for the outages. This alert was issued after ten financial institutions received a DDoS for ransom notes from the Armada Collective (see figure 3). Armada known in Switzerland following a similar ransom campaign they launched in November against ProtonMailiii.
These attacks display a similar pattern to those seen during the email service outage that plagued ProtonMail, HushMail and other encrypted email services in November 2015. During this campaign, attacks exceeded 100Gbps, targeting not only the datacenter, but also routers in Zurich, Frankfurt and other locations where ProtonMail had nodes. The first wave of attacks included huge volumetric attacks. During the second wave, more complex and sophisticated attacks targeting additional weak points in the infrastructure were executed. The coordinated assault on key infrastructures successfully brought down both the datacenter and the ISP, affecting not only ProtonMail, but hundreds of other companies.
Targets
- Digitec.ch
- Fust.ch
- Microspot.ch
- Interdiscount.ch
- Denner.ch
- Leshop.ch
- Coop.ch
- Galaxus.com
- SBB.ch
- Brack.ch
Possible attack vectors
- SSDP
- NTP
- DNS
- TCP RST
- TCP SYN
- SYN Flood
- SYN ACK
- ICMP
How to Prepare
While it is impossible to predict the next target of a ransom attack, organizations need to proactively prepare networks and have an emergency plan in place for such an incident. If faced with a threat from a blackmail group, it is important to take the proper steps to mitigate the attack. We recommend reviewing network security policies, and patching the system accordingly. Maintaining and inspecting your network often is necessary to defend against these types of risks and threats.
Organizations under Threat Should Consider
A hybrid solution that includes on premise detection and mitigation with cloud-based protection for volumetric attacks. This provides quick detection, immediate mitigation and protects networks from volumetric attacks that aim to saturate the Internet pipe.
- A solution that provides protection against sophisticated web-based attacks and web site intrusions to prevent defacement and information theft.
- A cyber-security emergency response plan that includes an emergency response team and process in place. Identify areas where help is needed from a third party.
- Monitor security alerts and examine triggers carefully. Tune existing policies and protections to prevent false positives and allow identification of real threats if and when they occur.
Radware's hybrid attack mitigation solution provides a set of patented and integrated technologies designed to detect, mitigate and report todays most advanced threats. Dedicated hardware and cloud solutions protect against attacks in real time and help ensure service availability.
Under Attack and in Need of Expert Emergency Assistance?
Radware offers a full range of solutions to help networks properly mitigate attacks similar to these. Our attack mitigation solutions provide a set of patented and integrated technologies designed to detect, mitigate and report todays most advanced DDoS attacks and cyber threats. With dedicated hardware, fully managed services and cloud solutions that protect against attacks, Radware can help ensure service availability. To understand how Radware's attack mitigation solutions can better protect your network contact us today.