On May 3, 2018, Radware’s Malware Protection Service detected a zero-day malware threat at one of its customers, a global manufacturing firm, by using machine-learning algorithms.
Download the Full Alert
Abstract
On May 3, 2018, Radware’s Malware Protection Service detected a zero-day malware threat at one of its customers, a global manufacturing firm, by using machine-learning algorithms. This malware campaign is propagating via socially-engineered links on Facebook and is infecting users by abusing a Google Chrome extension (the ‘Nigelify’ application) that performs credential theft, cryptomining, click fraud and more.
Further investigation by Radware’s Threat Research group has revealed that this group has been active since at least March of 2018 and has already infected more than 100,000 users in over 100 countries. Facebook malware campaigns are not new. Examples of similar operations include facexworm and digimine, but this group appears to have been undetected until now thanks to the campaign consistently changing applications and the use of an evasive mechanism for spreading the malware.
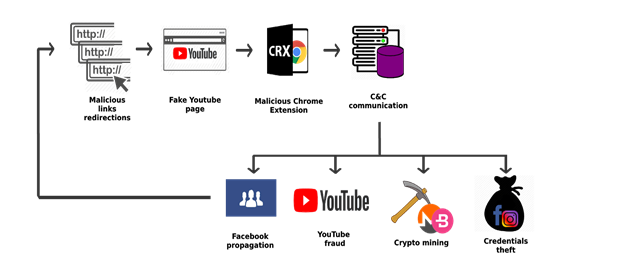 Figure 1: The malware kill chain
Figure 1: The malware kill chain
Infection Process
Radware has dubbed the malware “Nigelthorn” since the original Nigelify application replaces pictures to "Nigel Thornberry" and is responsible for a large portion of the observed infections. The malware redirects victims to a fake YouTube page and asks the user to install a Chrome extension to play the video.
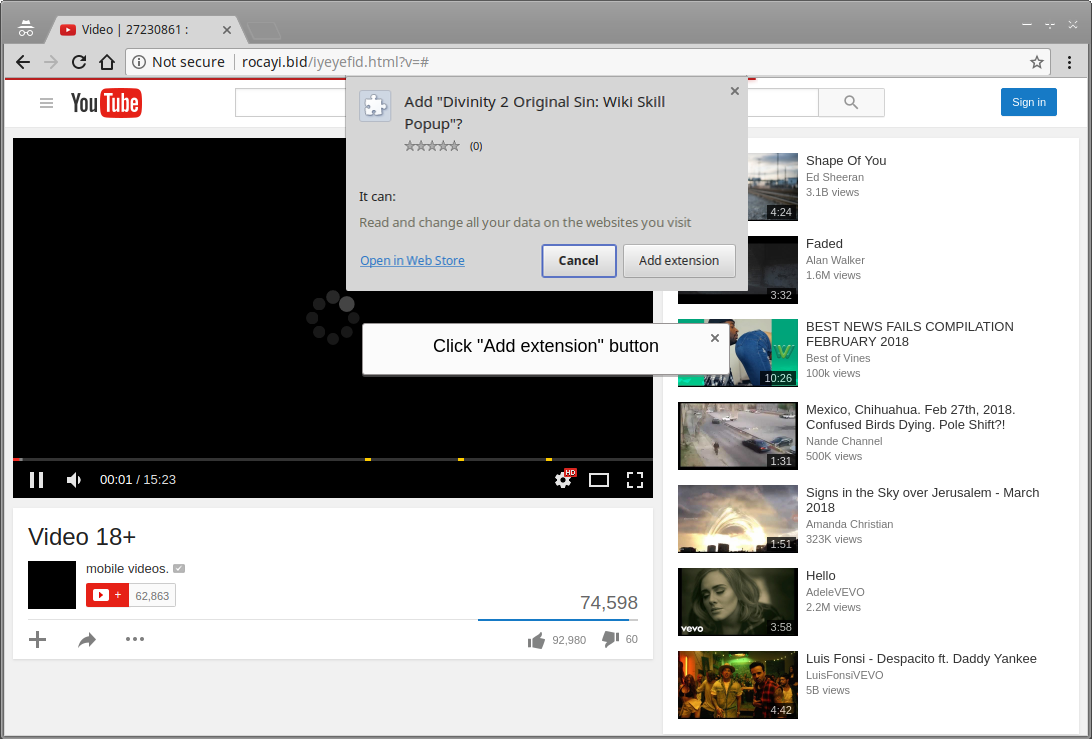 Figure 2: Fake YouTube page
Figure 2: Fake YouTube page
Once the user clicks on “Add Extension,” the malicious extension is installed and the machine is now part of the botnet. The malware depends on Chrome and runs on both Windows and Linux. It is important to emphasize that the campaign focuses on Chrome browsers and Radware believes that users that do not use Chrome are not at risk.
Botnet Statistics
Radware gathered the statistics from various sources, including the malicious extension statistics on the Chrome web store and the Bitly URL shortening service. A victim that clicks on “Add Extension” is redirected to a Bitly URL from which they will be redirected to Facebook. This is done to trick users and retrieve access to their Facebook account. Over 75% of the infections cover the Philippines, Venezuela and Ecuador. The remaining 25% are distributed over 97 other countries.
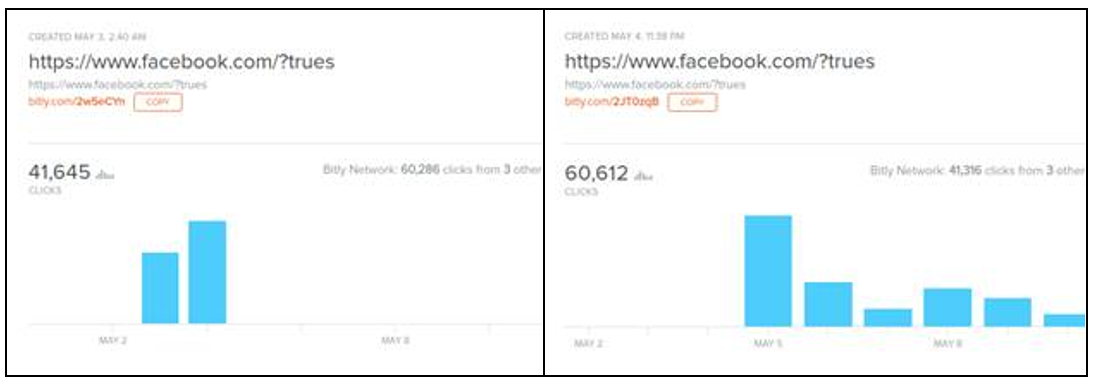 Figure 3: Bitly registration links with over 100,000 victims
Figure 3: Bitly registration links with over 100,000 victims
Bypassing Google Application Validation Tools
The campaign operators created copies of legitimate extensions and inject a short, obfuscated malicious script to start the malware operation.