In the first few months of 2023, Anonymous Sudan’s primary tactic was Web DDoS attacks from public cloud servers, hiding attack sources behind and across thousands of HTTPS/SOCKS proxies. After the attacks on Denmark, Anonymous Sudan’s IBM/SoftLayer Cloud servers were flagged for abuse and taken down. Anonymous Sudan continued its attacks after its servers were taken offline, most probably migrating their operations to a bulletproof cloud provider. Attacks from Anonymous Sudan were characterized by Web DDoS attacks combined with alternating waves of UDP and SYN floods. Attacks originating from tens of thousands of unique source IP addresses and UDP traffic reaching up to 600 gigabits per second (Gbps) while HTTPS request floods reached in the several million requests per second (RPS).
In the second half of 2023, Anonymous Sudan leveraged the SKYNET/GODZILLA botnet to perform attacks against Microsoft, X and OpenAI (ChatGPT). In the posted claims on Telegram for the attacks, Anonymous Sudan added the footnote that these attacks were performed with the SKYNET botnet. The SKYNET/GODZILLA botnet rents its infrastructure for DDoS attacks and provides a combination of Web DDoS, volumetric attacks (UDP Frag and UDP Amplification), TCP SYN and SYN-ACK. Through the dstat Linux command , SKYNET/GODZILLA demonstrated 40Gbps for L4 TCP attacks and over 200Gbps for UDP attacks, while Web DDoS (HTTPS) attacks leveraging proxies had a potential of 15 million RPS.
On February 24, 2024, Crush, the leader of Anonymous Sudan, announced a new DDoS service named “InfraShutdown,” labeling it as “the pinnacle of bullet-proof cyber dominance,” offering DDoS attack campaigns tailored to the needs of its global clientele with military-grade privacy. This supposedly new DDoS-for-hire service was described as “specialized in nation-state level disruptions, targeting critical infrastructures, financial system, and telecommunication networks” in an announcement forwarded by the @InfraShutdown Telegram channel that was created on February 24, 2024, coinciding with the date of the announcement.
An Exclusive Service
New subscribers are asked to provide visual proof of their crypto balance. No proof, no admittance. Typical booter and stresser services are very lenient in their terms for users to subscribe and openly advertise their (cheap) prices on Telegram. It looks like InfraShutdown is attempting to create an exclusive offering, targeting a market with very specific needs and a requirement for more serious attack power.
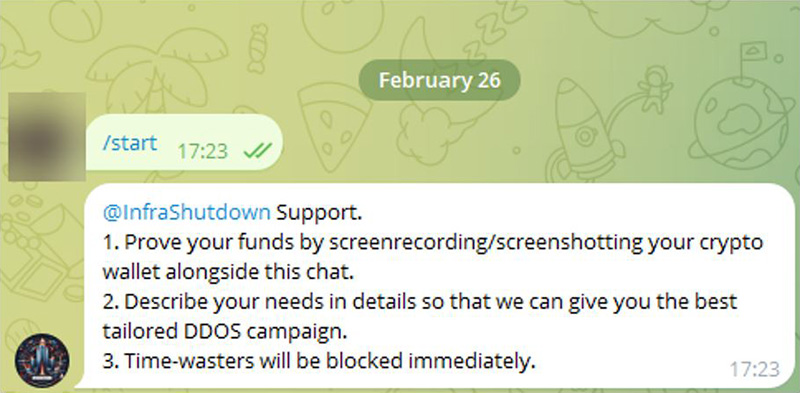 Figure 3: Requirement to provide visual proof of funds in a crypto wallet to join the service (source: Telegram)
Figure 3: Requirement to provide visual proof of funds in a crypto wallet to join the service (source: Telegram)
Promotion
Through its Telegram channel @xAnonymousSudan, which reaches over 55,000 subscribers as of February 28, 2024, Anonymous Sudan promotes the new service through advertisements and by claiming denial of service attacks against highly visible and public targets. Note that the original @AnonymousSudan channel reached over 120,000 subscribers before it got banned, forcing the group to start anew with an alternative channel named @xAnonymousSudan.
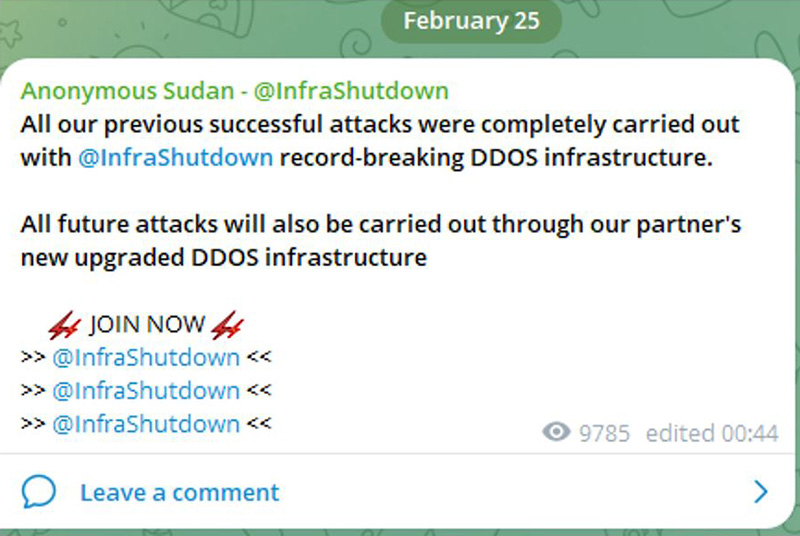 Figure 4: Advertising the services of InfraShutdown on its Telegram channel (source: Telegram)
Figure 4: Advertising the services of InfraShutdown on its Telegram channel (source: Telegram)