Several hacktivist collectives have announced Sunday, April 7, as the kickoff date for this year's OpIsrael operation, coinciding with the 2013 inaugural OpIsrael attacks by Anonymous 11 years prior.
Download
Several hacktivist collectives have announced Sunday, April 7, as the kickoff date for this year's OpIsrael operation, coinciding with the 2013 inaugural OpIsrael attacks by Anonymous 11 years prior. This chosen date also reflects the six-month mark since the onset of hostilities between Israel and Hamas on October 7, 2023, during which Hamas launched attacks on communities along Gaza's southern border with Israel.
Under attack? Get help now.
Background
OpIsrael was initiated by Anonymous in November 2012 as a reaction to the Israeli military operation named Pillar of Defense. This operation, which lasted for eight days starting on November 14, 2012, was the Israel Defense Force's response to the firing of 100 rockets at Israel from the Hamas-controlled Gaza Strip within a single day. Initially, OpIsrael served as an informal battle tag adopted by a collective of hacktivists from Anonymous to counteract the Israeli military action. The 2012 operations by Anonymous saw numerous Israeli websites suffer from data breaches, defacements and denial-of-service attacks, raising questions among security experts about whether this signified a new form of cyber warfare—and whether a group like Anonymous could be seen as an unconventional army.
In the subsequent year, Anonymous decided to formalize OpIsrael into an annual campaign aimed at Israel, marking its commencement on April 7, 2013, a date that coincided with Holocaust Remembrance Day. Their stated objective was to "erase Israel from the internet" by targeting Israeli networks and applications due to what Anonymous claimed were human rights abuses against Palestinians, with the broader aim of highlighting the Israeli-Palestinian conflict.
Almost a decade later, following the downfall of Anonymous and the lack of support for OpIsrael, a group of pro-Muslim hacktivists from Southeast Asia launched a new campaign called OpsBedil to fill the void. In 2021, cyberattacks were mainly reactionary in the Middle East, with minor cases of hacktivism in the region typically following physical or political confrontation. Specifically, OpsBedil was a political response by DragonForce Malaysia to the Israeli ambassador to Singapore stating that Israel was ready to work towards establishing ties with Southeast Asia’s Muslims-majority nations. As a result, the group and several affiliates launched a series of DDoS and defacement attacks against several organizations in Israel during June and July.
Building on OpsBedil's initial achievements, DragonForce Malaysia initiated OpsBedil Reloaded in 2022 amid escalating tensions in the Middle East during Ramadan. This time, their operations against Israeli targets included website defacements, denial-of-service attacks and data breaches. Although OpsBedil did not achieve the same level of notoriety as OpIsrael, it introduced a significant risk to the region. Contrary to Anonymous, which had dwindled in capacity to target Israel effectively, DragonForce Malaysia and its allies possessed the time, resources and determination to introduce a substantial, albeit moderate, threat level to Israel, surpassing any recent activities reminiscent of OpIsrael.
In anticipation of OpIsrael's 10th anniversary in 2023, amidst a resurgence of hacktivism fueled by the conflict in Ukraine and escalating geopolitical strains involving Israel, numerous well-known groups declared their participation in the campaign. Earlier in the year, Mysterious Team Bangladesh and Anonymous Sudan initiated DDoS attacks against Australia as part of the operation OpAustralia. This collaboration between Sudanese and pro-Palestinian hackers, based primarily in India, shifted focus towards Israel in April. They were joined by other collectives from Southeast Asia, including the Vietnam Cyber Army, also known as Mr. Dempsey. Together, they orchestrated a series of DDoS attacks targeting a variety of organizations throughout Israel.
April 7, 2024
Several hacktivist groups declared Sunday, April 7, as the start date for this year's OpIsrael campaign, aligning with the date of the first OpIsrael attacks by Anonymous in 2013, 11 years earlier. This date also marks the six-month anniversary of the conflict between Israel and Hamas, which began on October 7, 2023, when Hamas attacked communities along Israel's southern border with Gaza. The Israel Defense Forces (IDF) retaliated with an operation named Operation Iron Swords. Concurrent with the ground conflict, there was a notable uptick in cyberattacks targeting Israeli entities, elevating Israel to one of the most targeted nations by hacktivists in 2023.
On the evening of April 2, 2024, Team Insane Pakistan expressed their pledge to join the OpIsrael campaign, specifically mentioning participating on Sunday, April 7. Soon after, a hacktivist collective known as Anonymous Global took to Telegram to initiate a countdown for OpIsrael, setting the stage for activities to begin on April 7. Additionally, earlier that day, AnonGhost and azzasec declared their support for OpIsrael, aligning themselves with the operation.
 Figure 1: Telegram post by Team Insane PK on April 2 at 11pm Israel Time (source: Telegram)
Figure 1: Telegram post by Team Insane PK on April 2 at 11pm Israel Time (source: Telegram)
Figure 2: Telegram post by Anonymous Global on April 2 at 00:23 pm Israel Time (source: Telegram)
Figure 3: Telegram post by AnonGhost, announcing OpIsrael alliance with azzasec (source: Telegram)
Israel: Most Targeted Country by Hacktivists in 2023
In 2023, Israel emerged as the prime target for hacktivist activities. A reported 1,480 DDoS attacks make it the most attacked nation by such groups throughout the year. The onslaught began in the first half of the year, particularly from pro-Islamic hacktivist groups. These groups were inspired by the activities of pro-Russian hacktivists in 2022 and directed their efforts towards Israel during the annual OpIsrael campaign. From March 27 (the 13th week of the year) to April 16 (the 15th week), Israel faced a first wave of attacks reaching over 120 DDoS attacks in week 14. This heightened level of hacktivist activity persisted until the 20th week of the year, ending around May 21. For almost two months, Israel experienced a significant increase in hacktivist attacks, largely fueled by the momentum of the OpIsrael campaign.
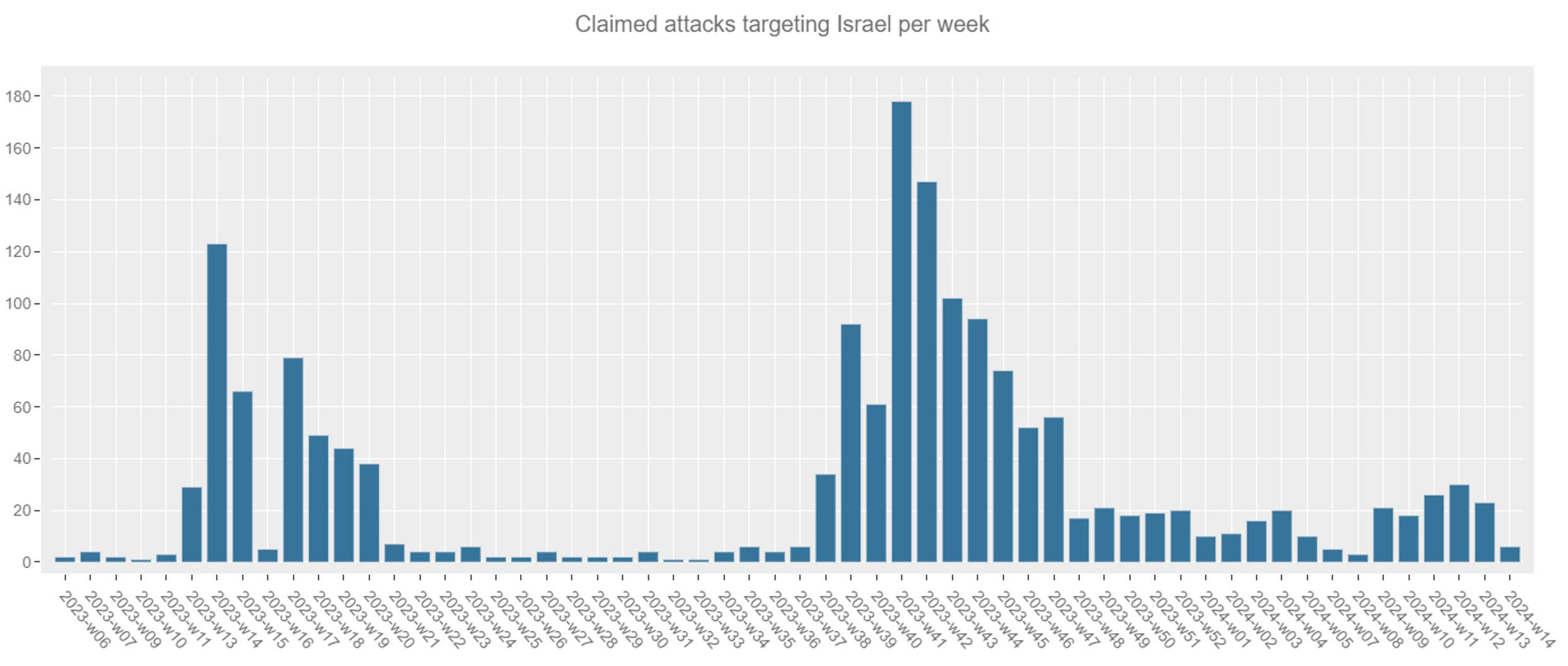 Figure 4: Number of DDoS attacks per week claimed by hacktivist groups on Telegram. Note that only two days were accounted in week 2024-14 (source: Radware)
Figure 4: Number of DDoS attacks per week claimed by hacktivist groups on Telegram. Note that only two days were accounted in week 2024-14 (source: Radware)
In the latter part of the year, following the conflict between Israel and Hamas, pro-Palestinian hacktivists intensified their cyberattacks against Israeli entities. Specifically, in the fortnight preceding October 7 (the 40th week), there was a marked escalation in the number of DDoS attacks aimed at Israeli institutions and organizations. Following the onset of the conflict, nearly 250 DDoS attacks were claimed by pro-Palestinian groups within two weeks. Although the frequency of these attacks gradually diminished over time, a significant uptick in cyberattacks against Israel was observed at the start of the Ramadan, signaling a buildup to the annual OpIsrael campaign for 2024. This resurgence of activity, as declared by various anonymous factions and pro-Palestinian hacktivists, was set to commence on April 7, 2024.
Coordination Among Hacktivist Groups
Hacktivists often use hashtags to name their operations, typically beginning with “#Op” to easily promote their attack campaigns and form temporary alliances. Consequently, it’s expected to observe a surge in hashtags related to OpIsrael in tandem with an uptick in claimed attack activities. This heightened discussion serves as a reliable indicator of global activity within the hacktivist community as they focus their efforts on specific nations or unite in campaigns aligned with shared goals.
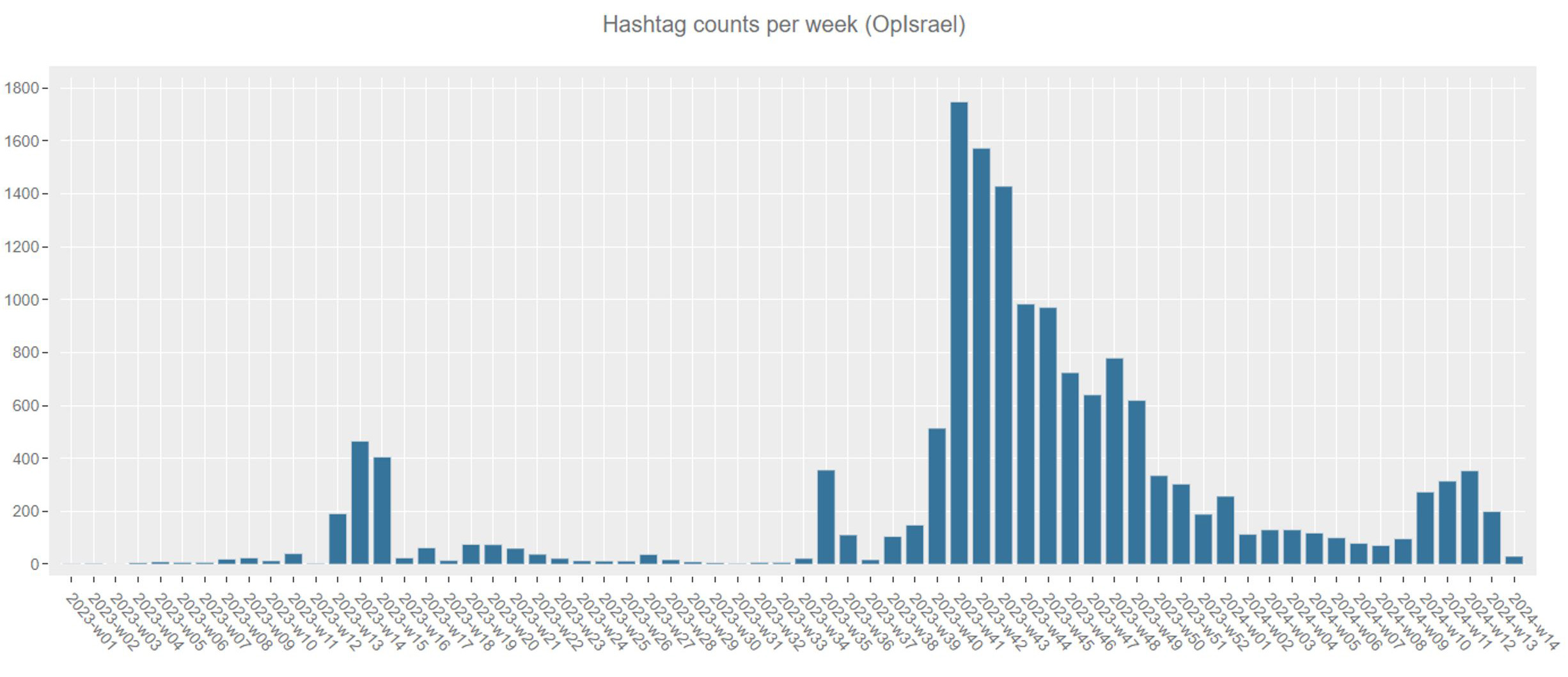 Figure 5: Weekly OpIsrael hashtag counts on Telegram. Note that only two days were accounted in week 2024-14 (source: Radware)
Figure 5: Weekly OpIsrael hashtag counts on Telegram. Note that only two days were accounted in week 2024-14 (source: Radware)
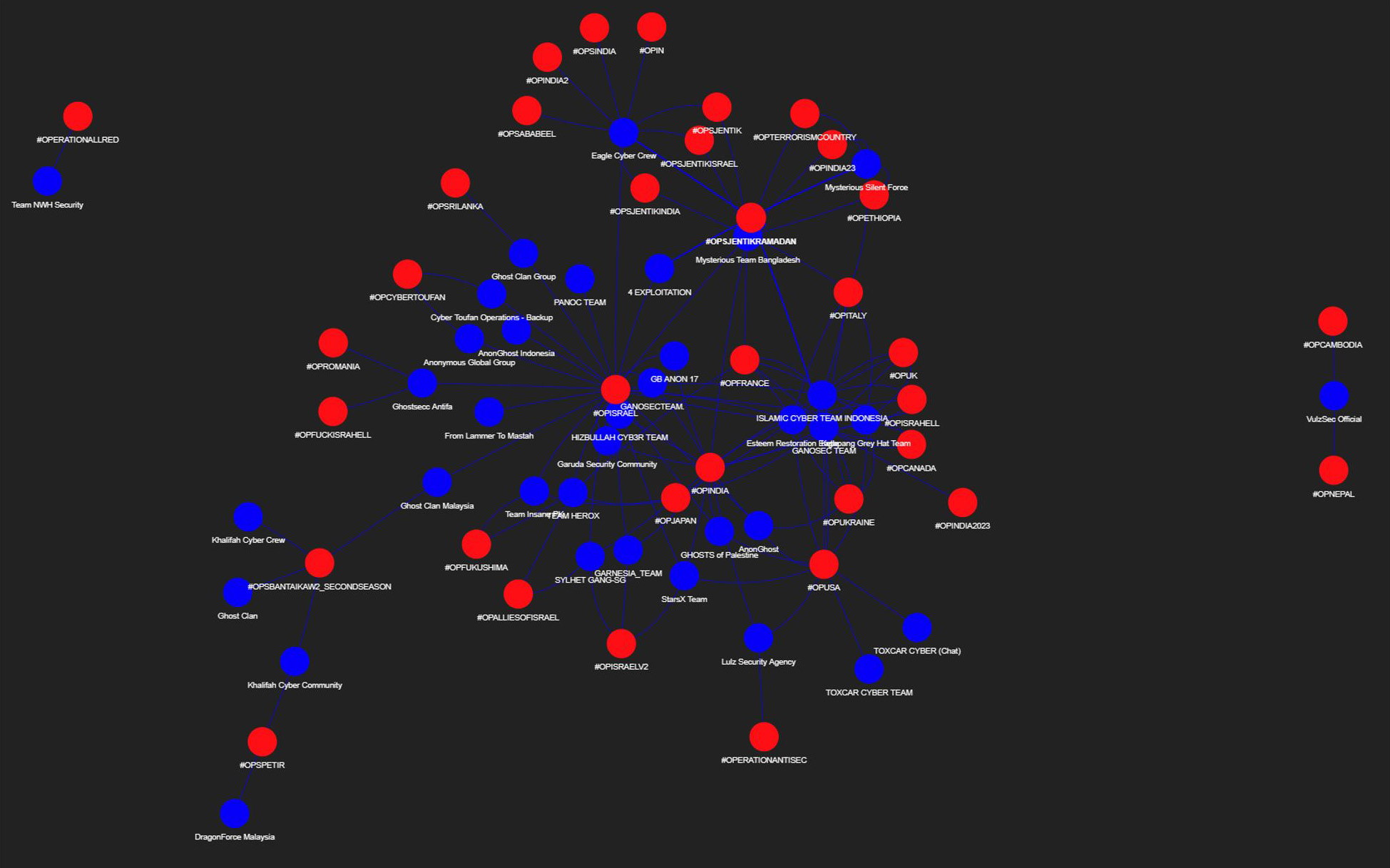 Figure 6: Graph linking Telegram channels (blue) and hashtags (red) over the period 2023/2024 (source: Radware)
Figure 6: Graph linking Telegram channels (blue) and hashtags (red) over the period 2023/2024 (source: Radware)
Figure 6 displays a network graph highlighting connections between Telegram channels (depicted in blue) and hashtags (shown in red). A significant number of hacktivist groups linked to the OpIsrael hashtag have also been involved in cyber campaigns targeting countries such as India, the UK, Italy, Ethiopia, Romania and France, among others. The onset of the conflict between Israel and Hamas served as a pivotal moment, influencing the involvement of various groups in cyberattacks aimed at Israel.
LEARN MORE AT RADWARE’S SECURITY RESEARCH CENTER
To know more about today’s attack vector landscape, understand the business impact of cyberattacks, or learn more about emerging attack types and tools, visit Radware’s Security Research Center. Additionally, visit Radware’s Quarterly DDoS & Application Threat Analysis Center for quarter-over-quarter analysis of DDoS and application attack activity based on data from Radware’s cloud security services and threat intelligence.