Last year's renewed hacktivist operations throughout the Middle East have returned, presenting a certain level of risk for unprotected assets as threat actors begin to target organizations and citizens across Israel.
Read the Complete Alert
OpsBedil Reloaded 2022 by DragonForce Malaysia
Last year's renewed hacktivist operations throughout the Middle East have returned, presenting a certain level of risk for unprotected assets as threat actors begin to target organizations and citizens across Israel.
 Figure 1: OpsBedil reloaded 2022 campaign flyer
Figure 1: OpsBedil reloaded 2022 campaign flyer
OpsBedil
OpsBedil is a relatively new campaign targeting Israel. It first appeared in 2021 and has since seen four official operations under its battle tag. The operations are mainly reactionary and following physical or political confrontations. Operations tend to have a more substantial presence in the months April to July.
OpsBedil is replacing the now-defunct Anonymous operations known as OpIsrael. The new operations are conducted by DragonForce Malaysia and its affiliates throughout Southeast Asia, specifically Malaysia and Indonesia. The current operation, OpsBedilReloaded, is a political response to events that occurred in Israel on April 11, 2022.
DragonForce Malaysia
The driving force behind #OpsBedilReloaded is DragonForce Malaysia, a pro-Palestinian hacktivist group located in Malaysia. DragonForce Malaysia has also been observed working with several other hacktivist groups, including the T3 Dimension Team and RileksCrews. DragonForce Malaysia has a website and a forum where threat actors conduct most of their announcements and discussions. The group also has a Telegram channel, but most content is replicated throughout the forum and other social media platforms.
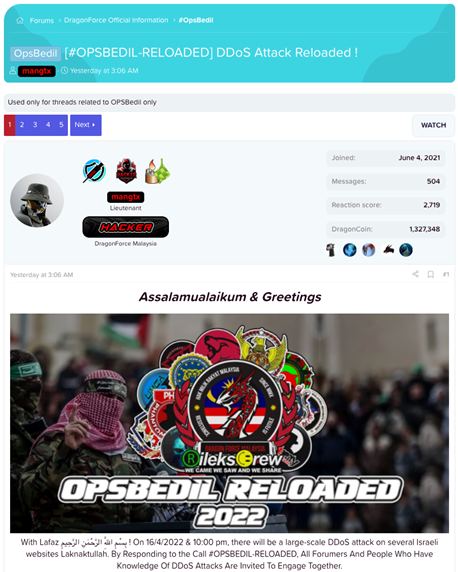 Figure 2: OpsBedil Reloaded 2022 forum post
Figure 2: OpsBedil Reloaded 2022 forum post
The threat actors behind DragonForce Malaysia created the domain DragonForce.io in 2021 during their original campaign. The forum today has grown to 13,000 members and 11,000 discussion threads. Since its creation, this forum has been the central communication hub for the group. Discussions in the forum include OpsBedil, but also threads about anonymity, hacking, general technology and education.
Recent Attacks
The hacktivists of DragonForce Malaysia, along with other threat actors, began targeting several organizations in Israel with defacements, denial-of-service attacks and data leaks on April 11, 2022 as part of the OpsBedilReloaded campaign. Recent OpsBedilReloaded attacks are illustrated below, but the operation is still ongoing at the time of publication.
DEFACEMENT
Radware has observed and confirmed several defacements by DragonForce Malaysia and members of T3 Dimension Team since the start of OpsBedilReloaded on April 11. The defacements cite the escalating tension in the Middle East during Ramadan as their justification for cyberattacks and call hackers and activists to unite and campaign against Israel. The defacements in the current campaign are very similar to the campaign of last year, only updated with new content.
 Figure 3: OpsBedil Reloaded defacement message
Figure 3: OpsBedil Reloaded defacement message
SCANNING & EXPLOITING
Since the beginning of the operation, Radware has seen and confirmed several scanning and exploitation attempts by members of DragonForce Malaysia. Threat actors have been exchanging information about compromised and leaked sensitive information through a Google Dork query '=inurl:objDoc.asp?PID הרשמה'. Forum post to members joining the OpsBedilReloaded campaign provide several tools from scanner used to discover vulnerable servers that can be exploited for defacement to scripts for performing denial-of-service attacks.
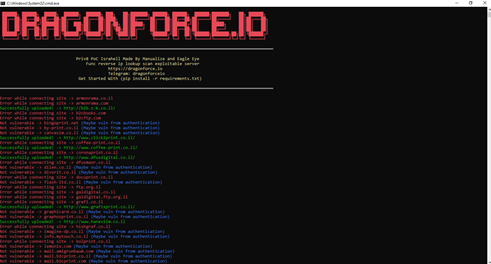 Figure 4: DragonForce.io tool to scan for vulnerable servers
Figure 4: DragonForce.io tool to scan for vulnerable servers