Several vulnerabilities relating to the Spring Framework, an open-source framework for building enterprise Java applications, were disclosed in March of 2022.
Read the Complete Alert
CVE-2022-22965 (Spring4Shell), CVE-2022-22963, CVE-2022-22950 and CVE-2022-22947
Several vulnerabilities relating to the Spring Framework, an open-source framework for building enterprise Java applications, were disclosed in March of 2022.
On March 29, 2022, a remote code execution (RCE) in Spring Cloud Function was disclosed by Spring, a VMWare subsidiary. The vulnerability, tracked as CVE-2022-22963, was fixed at disclosure with the release of Spring Cloud Function 3.1.7 and 3.2.3. The disclosure came closely after another remote code execution vulnerability (CVE-2022-22947) in Spring Cloud Gateway that was patched earlier in March in versions 3.1.1 and 3.0.7 and higher of Spring Cloud Gateway.
In addition, Spring reported a denial-of-service vulnerability in Spring Expressions. The DoS condition could be triggered by a specially crafted Spring Expression Language (SpEL) expression, is tracked as CVE-2022-22950 and was fixed in Spring Framework version 5.3.17 and higher.
On March 31, 2022, an unauthenticated remote code execution vulnerability in Spring Core was disclosed (CVE-2022-22965) and fixed in Spring releases 5.3.18 and 5.2.20 and higher. The vulnerability was dubbed SpringShell or Spring4Shell in analogy to the Log4Shell vulnerability that took the security community by storm in December.
Spring Cloud Gateway Code Injection (CVE-2022-22947)
Spring Cloud Gateway provides a library for building API gateways on top of Spring and Java. It provides a flexible way of routing requests based on a number of criteria, as well as focuses on cross-cutting concerns such as security, resiliency and monitoring. On March 1, 2022, VMWare disclosed a code injection vulnerability in the Spring Cloud Gateway tracked as CVE-2022-22947. Applications using Spring Cloud Gateway are vulnerable to a code injection attack when the Gateway Actuator endpoint is enabled, exposed and unsecured. A remote attacker could make a maliciously crafted request that could allow arbitrary remote execution on the remote host.
Proof of concept exploit code was published on March 3, here. The exploit works by appending ‘/actuator/gateway/routes/{id}’ to a vulnerable location and posting a payload with a runtime execution command in the ‘filters.args.value’ field as json data in the body:
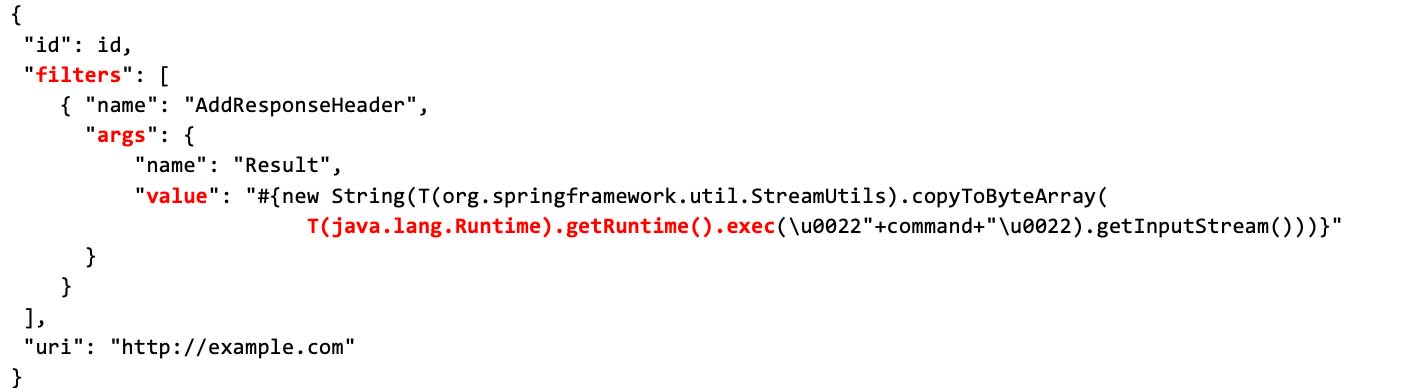
The Radware Cloud WAF Service detected and blocked a handful of attempts on January 15 and 16 and recorded increased exploit activity with between one and four thousand attempts per day since March 10.
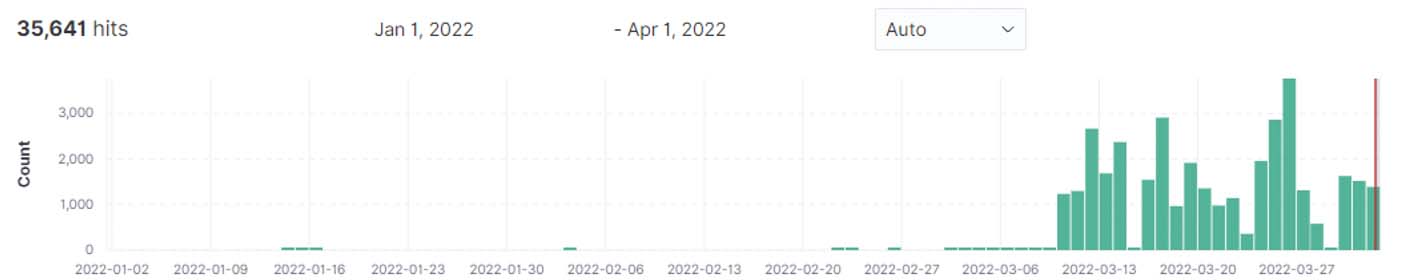 Figure 1: Invalid resource location attempts for URL '*/actuator/gateway/routes/'
Figure 1: Invalid resource location attempts for URL '*/actuator/gateway/routes/'
Spring Cloud Function RCE (CVE-2022-22963)
Spring Cloud is part of the Spring ecosystem and provides a set of components that can hook Spring code straight into well-known cloud services from Alibaba, Amazon, Azure, Netflix and many more. Spring Cloud Function is a subcomponent of Spring Cloud that provides serverless deployment of Java functions.
CVE-2022-22963 refers to a Spring Expression Language (SpEL) Resource Access Vulnerability in the Spring Cloud Function component by using an unsafe evaluation context with user-provided queries. A malicious actor can leverage the vulnerability to gain remote code execution on a vulnerable system by crafting a request to the application and setting the ‘spring.cloud.function.routing-expression’ header.