With the stated goal of "erasing Israel from the internet" in protest against claimed crimes against the Palestinian people, Anonymous will launch its yearly operation against Israel. Named OpIsrael, it is a cyber-attack timed for April 7th by a number of hacktivist groups that join forces with the greater Anonymous collective. This alert from Radware's Emergency Response provides further information about this operation and how to stay protected.
Download a Copy Now
Abstract
With the stated goal of "erasing Israel from the internet" in protest against claimed crimes against the Palestinian people, Anonymous will launch its yearly operation against Israel. Named OpIsrael, it is a cyber-attack timed for April 7th by a number of hacktivist groups that join forces with the greater Anonymous collective. This year, hackers have provided new tools and technical guidance in preparation for OpIsrael. In parallel, they have published a partial list of targets and tactics that they intend to use while conducting this operation.
In past years, Israel has seen moderate attacks launched against its networks and infrastructure. Organizations should take precautions and make sure they are prepared for OpIsrael2016. Radware's Emergency Response Team has analyzed the attack vectors and techniques that will be used for OpIsrael. This alert provides further information about this operation along with information about how to stay protected.
Background
Ideological, political and religious differences are at the core of this operation. Since 2012, Anonymous has launched a yearly campaign in protest against the Israeli governments conduct in the Israeli-Palestinian conflict. Every year, OpIsrael calls for dozens of different hacktivist groups to "hack, deface, hijack, leak databases, admin takeover and DNS terminate" targets associated with Israel. Well known for its advanced technological capabilities, Israel poses a challenge for hackers. Those that attempt and overcome those challenges win prestige and recognition for their expertise inside their communities.
In previous years Israel and Israelis have seen modems hacked, credit card data breached government and personal information posted, Facebook accounts hijacked, websites defaced, emails leaked and a series of network-crippling denial of service attacks. In the last few weeks groups like Redcult and AnonGhost have targeted a number of government and corporate sites with denial of service attacks and database leaks (See Figure 1). The time leading up to the official launch in April will show a growing number of operations targeting Israel.
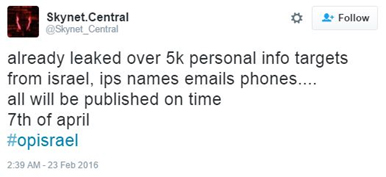
Figure 1: Attacker claims they have stolen personal information
Operational Information
Attackers
- AnonGhost
- RedCult
- Fallaga Team
- Anonymous
Hashtags
- #OpIsrael
- #OpIsrael2016
- #OpIsraHell2016
- #FreePalestine
Attacks from OpIsrael 2015
In 2015, Israel witnessed a number of different cyber-attack tools and techniques used against its networks and infrastructure. Though the 2015 attacks were modest, hackers were still able to successfully launch several denial-of-service attacks and database leaks.
Tools & Techniques
DDoS
- Anonymous External Attack – Develop by AnonGhost to generate a UDP Flood with payloads containing multiple zeros against port 80 by default. It can be mitigated by blocking UDP traffic to the targeted port.
- DoSeR 2.0 - A traffic generator with scanning capabilities using multiple threads and sockets. Its attack vectors include, TCP, UDP, and HTTP floods.
- LOIC Fallaga – a unique variation of LOIC UDP/ TCP flood tool created by Fallaga hacker group.
- Other DDoS tools – AnonGhostDDoS, Jays Booter, FireFlood, SYN-FLOOD-DoS, njRAT, Turbinas, TorsHammer, THC-SSL, PyLoris

Figure 2: Hackers also collected statistics to track successful attacks
- 3 hosting servers (hosting several small websites) were hacked
- Data dump of Israeli users information and credentials – 99% of them are old dumps
- Attackers published credit card details – confirmed as old and inactive
- Government websites confirmed that hackers launched multiple SQL injection attempts against them – all were successfully blocked and failed.
- Israeli home routers hacked - http://pastebin.com/embed_js/84nfwx9U, http://pastebin.com/g8M1GPUJ
2016 OpIsrael Attack Vectors & Tools
HaxStroke from AnonGhost recently released a script for OpIsrael2016. SadAttack 2.0 is a python script that is nearly identical to the DoS tool, HTTP Unbearable Load King, also known as HULK. SadAttack 2.0 is a flood tool that is used to generate a mass amount of traffic that will utilize network or application resources, resulting in the degradation or loss of service for users. The attack bypasses caching engines and hits the server resources directly.
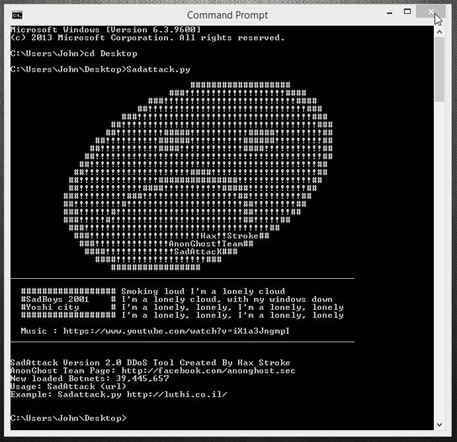
Figure 3: Tool – Sadattack 2.0
Hax Strokes of AnonGhost has also advertised the tool, An0nStr3ss. An0nStr3ss is an executable file that launches a command line based stresser. The An0nStr3ss tool offers seven different attack methods. These attack methods include UDP, RUDY, SSYN, ARME, RDoS, SlowLoris and AR-UDP. This tool is capable of generating a mass amount of traffic and provides the attacker with a number of different methods to choose from.
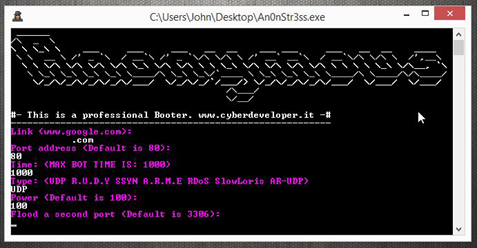
Figure 4: Tool – An0nStr3ss
Another tool referenced for use in OpIsrael is SwitchBlade v4.0. This is a Layer 7 tool that is capable of producing 3 different types of DDoS attacks. The methods available in for this tool are slow headers, slow POST, and SSL renegotiation (See Figure 5). You could also expect to see attackers using other tools such as TorsHammer, SlowLoris, PyLoris, Slow HTTP test, Mobile LOIC, and THC-SSL.
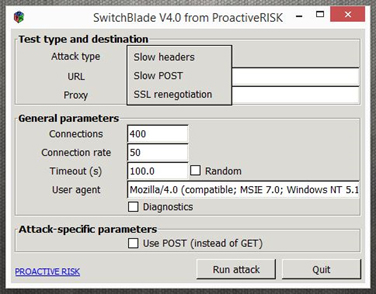
Figure 5: Tool - SwitchBlade
Current Targets
Attackers are currently organizing and preparing for the official launch of OpIsrael 2016. Radware has begun witnessing various activities from the attackers, including the publication of a number a target lists (see Appendix A).
Reasons for Concern
OpIsrael receives large amounts of attention for several reasons; one of them being the global media coverage surrounding the Israeli-Palestinian conflict. To date, Radware has witnessed several SQL injections, data dumps and service outages in the buildup to the April 7 launch. Currently, OpIsrael is planning on targeting the Israeli Government as well as the telecommunications, education and financial services industry.
How to Prepare
Political and ideological-driven attacks such as these can be difficult to avoid. Government agencies and organizations in Israel should proactively prepare their networks with DDoS mitigation service designed to detect, mitigate, and report today's most advanced threats as well as have an emergency response plan in place.
Effective Protection Considerations
Enterprises and government agencies should consider a comprehensive DDoS attack defense system to detect and mitigate multi-vector, volumetric denial of service, and Web application attacks. Small business and home users are advised to contact their service providers in advance to receive the most updated solution against these types of threats. Enterprises should monitor security alerts and examine triggers carefully. Tune existing policies and DDoS protection solutions to prevent false positives and allow identification of real threats if and when they occur.
Here are several considerations for a seamless security solution:
- A hybrid solution that includes on premise detection and mitigation with cloud-based protection for volumetric attacks. This provides quick detection, immediate mitigation and protects networks from volumetric attacks that aim to saturate the Internet pipe.
- A Web application security protection solution via a Web Application Firewall (WAF) or a cloud WAF service, that can protect against sophisticated web-based attacks and website intrusions to prevent defacement and information theft.
- An integrated, synchronized solution that can protect from multi-vector attacks combining DDoS with web-based exploits such as website scraping, Brute Force and HTTP floods.
- A cyber-security emergency response plan that includes an emergency response team and process in place. Identify areas where help is needed from a third party.
These additional considerations are important when choosing a solution to defend from web-based attacks:
- IP-anostic device fingerprinting – Having the ability to detect attacks beyond source-IP using by developing a device fingerprint that enables precise activity tracking over time
- Automatic and real time generation of policies to protect from 0-day, unknown attacks
- Shortest time from deployment to security
Need Expert Emergency Assistance?
Radware offers a full range of DDoS attack prevention solutions to help networks properly mitigate attacks similar to these. Our attack mitigation solutions provide a set of patented and integrated technologies designed to detect, mitigate and report todays most advanced DDoS attacks, web-application security attacks and other cyber threats. With dedicated hardware, fully managed services and cloud solutions that protect against attacks, Radware can help ensure service availability. To understand how Radware's attack mitigation solutions can better protect your network contact us today.
Appendix A: #Anonghost #OpIsrael2016 Target list
Ministries
- Prime Minister's Office
- Agriculture
- Communication
- Construction and Housing
- Environment
- Finance
- Health
- Industry, Trade And Labor
- Justice
- Social Affairs
- Critical National Infrastructure
- Tourism
- Culture and Sports
ISPs
- Bezeq International
- Netvision
- Smile Communication
- Internet Rimon
Education Institutes
- http://www.lander.ac.il/
- http://www.ariel.ac.il/
- http://www.bgu.ac.il/
- http://www.clb.ac.il/
- http://www.jct.ac.il/
- http://www.technion.ac.il/
- http://www.telhai.ac.il/
- http://www.weizmann.ac.il
- http://www.sapir.ac.il/
- http://www.yvc.ac.il/
- http://www.ruppin.ac.il/
- http://www.schechter.ac.il/
- http://www.mishpat.ac.il/
- http://fulbright.org.il/
- http://www.science.co.il/
- http://mfa.gov.il
- https://overseas.huji.ac.il/
- https://tau.ac.il/
- http://www.ono.ac.il/
- http://www1.biu.ac.il/
- http://www.jamd.ac.il/
- http://www.mla.ac.il/
- http://www.hadassah.ac.il/
- http://www.carmel.ac.il/
Financial and Law
- The Custom and VAT Authority
- Income Tax Commission
- Institute of Certified Public Accountants
- Israel Bar Association
- Internship and Admissions
- Treasury
- The National Court
- Secretariat
- The International Association of Jewish Lawyers
- The Pension Fund
- The Publishing House
- Jerusalem District Committee
- Tel Aviv District Committee
- Northern District Committee
- Southern District Committee
- Hadera Extension
- Ashdod Extension
Banks
- http://www.bankisrael.gov.il
- http://www.bankhapoalim.com/
- https://www.discountbank.co.il/
- http://www.leumi.co.il/
- https://new.fibi-online.co.il/wps/portal
- https://www.mizrahi-tefahot.co.il/en/Bank/pages/ default.aspx