Researchers from the Tsinghua University in Beijing, China, disclosed a new method for launching pulse wave denial-of-service (DoS) attacks.
Download a Copy Now
Researchers from the Tsinghua University in Beijing, China, disclosed a new method for launching pulse wave denial-of-service (DoS) attacks. The new DoS attack vector, dubbed DNSBomb, abuses multiple widely deployed mechanisms to enhance the reliability and availability of the Domain Name System (DNS) to accumulate DNS queries sent at a low rate and concentrate them into short, high-intensity bursts of volumetric traffic. This overwhelms and disturbs TCP traffic flows on target systems and services. By combining both DNS queries and responses with multiple operational DNS resolution mechanisms, the Pulsing DoS attack technique obtains a bandwidth amplification factor (BAF) of over 20,000.
Pulsing DoS Attacks
Pulse Wave or Pulsing DoS attacks use repeated, short bursts of high-volume traffic to impact a target system or service. Pulses or bursts can last up to a few hundreds of milliseconds with a periodicity of a couple of seconds while the attack campaign can span hours or even days. The high-volume pulses in Pulsing DoS attacks only last milliseconds, unlike the more common
Burst Attacks, which typically last several minutes. Due to their low average traffic bandwidth, Pulsing DoS attacks are harder to detect than traditional flooding attacks.
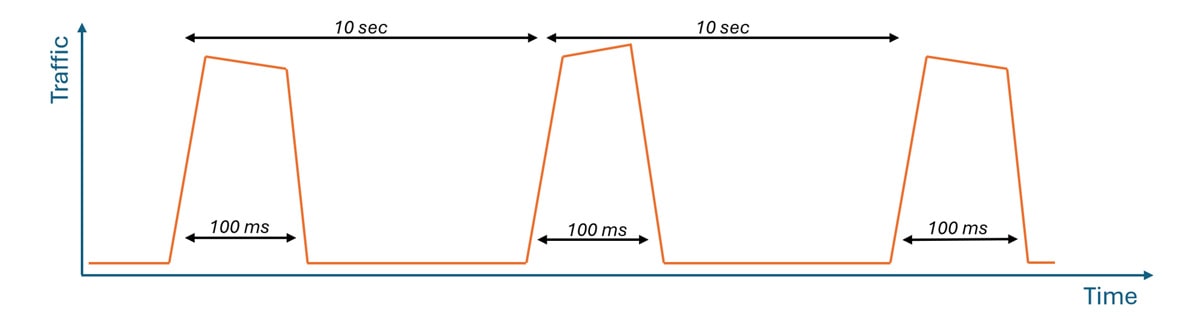 Figure 1: DNSBomb Pulsing DoS attack traffic pattern
Figure 1: DNSBomb Pulsing DoS attack traffic pattern
Pulsing DoS attacks cause intermittent packet loss and degrade TCP connections by exploiting weaknesses in the TCP congestion control mechanisms that operate on timescales such as Round-Trip Time (RTT) and Retransmission Timeout (RTO). RTT is used to estimate the optimal amount of data that can be in flight in the network and adjust the sending rate (the congestion window) under normal conditions. If packet loss occurs, TCP will wait for a period of RTO after a packet is resent until receiving a valid packet. Upon further loss, TCP dynamically adjusts RTO based on RTT and its variation and continues the retransmission strategy. If the total DoS traffic during an RTT-length pulse is sufficient to induce packet loss, the TCP flow will enter a timeout and resend a packet RTO seconds later. Moreover, if the DoS pulse period approximates the RTO, the TCP flow will continually incur a loss as it tries to exit the transmission state and eventually fail to exit resulting in a near-zero throughput.