Common DDoS attacks come in the form of sustained, high-volume traffic floods that ramp up gradually, reach a peak, and are then followed by either a slow or a sudden descent. In recent years, a new attack pattern has emerged. Bursts attacks, also known as hit-and-run DDoS, use repeated short bursts of high-volume attacks at random intervals. Each short burst can last only a few seconds, while a burst attack campaign can span hours or even days. These attacks unleash hundreds of gigabits per second of throughput toward its target.
According to our customer base, burst attacks have grown in popularity. Last year, a top-five U.S. carrier witnessed a tenfold increase in burst attacks, where 70% to 80% of attacks were less than a minute long. In a comprehensive survey conducted in 2017, half of the participants cited an increase in burst attacks.

The Challenge of Protecting Against Burst Attacks
The majority of on-premises DDoS protection solutions detect burst attacks, but most of them limit the rate of bad (and legitimate) traffic to a certain threshold, resulting in a high level of false positives. To minimize the level of false positives, security experts need to identify the attack traffic by analyzing traffic captures and manually creating a signature to block only the attack traffic. If the attack vector changes across bursts, the signature needs to adapt to the changing attack characteristics. The process of repeated manual signature adjustments can become a labor-intensive task, which renders the whole protection strategy infeasible.
Similarly, most hybrid DDoS protections utilize rate thresholds to trigger a diversion to a cloud DDoS-protection provider or scrubbing center. Still, they suffer from the same high level of false positives, because both the on-premise DDoS gear and scrubbing-center DDoS gear use rate-limit and manual signatures to pinpoint attack traffic and reduce false positives.
[You might also like: 2017’s 5 Most Dangerous DDoS Attacks & How to Mitigate Them (Part 2)]
Behavioral DoS Detection and Mitigation of Burst Attacks
To adequately defend against burst attacks, a different approach is required.
A Behavioral DoS (BDoS) Protection technology should effectively detect and mitigate burst attacks by utilizing machine-learning algorithms. These algorithms can learn normal traffic behaviors, detect traffic anomalies during an attack, automatically create signatures and adapt the protection to mitigate the attack.
BDoS gathers statistics on various parameters for several protocols, such as TCP, UDP, ICMP, and IGMP andbuilds a baseline of traffic in peacetime. A detection engine compares real-time statistics with the learned baseline in order to detect attacks.
Attack detection combines two parameters. The first is rate, the bandwidth of a specific traffic type. The second is rate-invariant, the portion of the specific traffic type out of the entire traffic distribution.
A fuzzy-logic inference system measures the degree-of-attack (DoA) surface. BDoS considers an attack to have started - and triggers attack handling -only when the overall DoA surface for the combined parameters is high. This guarantees accurate detection of attacks. For example, a high volume of traffic caused by a flash crowd will have a high rate anomaly, but the rate-invariant parameter remains normal. As a result, the combined DoA surface will not cause BDoS to trigger an attack handling. However, if both parameters show an anomalous score, the combined DoA surface will trigger attack handling, and BDoS will start creating a blocking signature in real-time. It takes BDoS 10 to 18 seconds to create a signature.
Burst attacks, however, which may last only a few seconds, bypass BDoS Protection because there is not enough time to automatically create a blocking signature. This is where Behavioral Burst-Attack Protection comes in.
[You might also like: Cyber and Securities – Financial Institutions Attack Landscape]
The Anatomy of Behavioral Burst-Attack Protection
Behavioral Burst Attack Protection optimizes BDoS attack detection and characterization.
For example, in the burst attack below, there are three bursts, and each one lasts a few seconds.
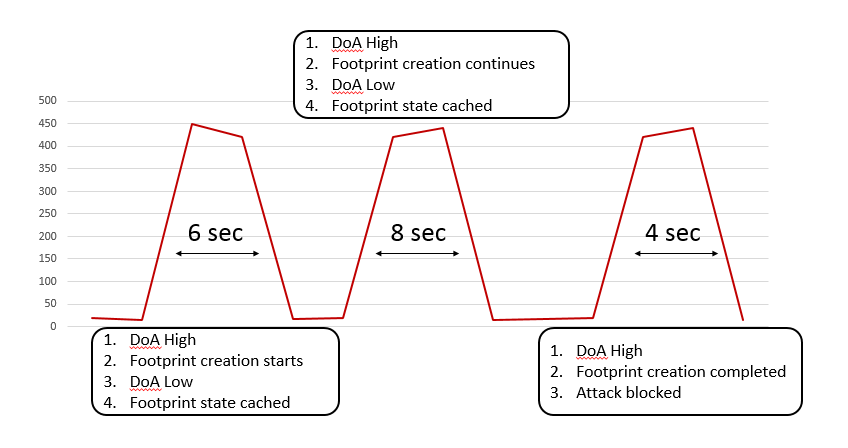
When burst 1 comes in, BDoS detects an attack due to high DoA, and proceeds to characterize the attack to create a blocking signature. Since burst 1 ends after six seconds, no signature has yet been created. During the idle time between burst 1 and burst 2, BDoS caches the state and the parameters it has gathered for the candidate signature, and keeps them for the next burst. When burst 2 comes in, BDoS continues to create the signature from the point at which it stopped, using the cached information. Since burst 2 ends after eight seconds (for a total of 14 seconds), BDoS does not yet finalize signature creation. However, when burst 3 comes in, for a total of eighteen seconds of continuous attack, BDoS finalizes signature creation, and blocks the attack.
BDoS blocks the subsequent bursts instantaneously since a valid signature is applied throughout the lifespan of the attack.
Burst attacks change vectors throughout the attack lifespan. This is a great challenge for attack-mitigation strategies, because it involves modifying the blocking signature in real-time across bursts. BDoS continuously monitors the attack traffic and measures the DoA. If the attack changes in such a way that the applied signature is no longer effective (that is, the DOA is high), BDoS fine-tunes the signature to block the mutable burst attack.
Effective Hybrid DDoS Protection of Burst Attacks
On-premise mitigation solutions guarantee in-line protection, but fail to protect against pipe saturation. Only a solution that combines on-premise and in-the-cloud protection against burst attacks ensures attack mitigation that is accurate, real-time, and fully automated.

Read the "Behavioral Burst-Attack Protection Whitepaper" to learn more.
Download Now