Over the past several months, Radware has observed a significant increase in DDoS activity across the globe and has been rapidly onboarding new customers in distress. These attacks have ranged from cases of hacktivism in Europe and the Middle East to Terabit DDoS attacks in Asia and the United States.
Read the Complete Alert
Phantom Squad & REvil, Growing Sophistication
Over the past several months, Radware has observed a significant increase in DDoS activity across the globe and has been rapidly onboarding new customers in distress. These attacks have ranged from cases of hacktivism in Europe and the Middle East to Terabit DDoS attacks in Asia and the United States.
However, one of the more concerning trends seen over the past few months has come from ransom denial-of-service (RDoS) groups claiming to be Phantom Squad and REvil. Radware researchers previously alerted about a similar RDoS campaign from a threat group claiming to be Phantom Squad in 2017 and more recently covered a campaign about an RDoS threat group claiming to be REvil, the notorious ransomware group.
Background
An RDoS campaign is a distributed denial-of-service (DDoS) attack motivated by monetary gain and leveraging extortion as its tactic. Attackers typically start by sending an email or posting on social media threatening to launch an attack on a particular day and time unless a ransom is paid, usually in Bitcoin, by the victim. In some cases, attackers launched a small demonstration attack on the victim's network as evidence that the threat is serious.
RDoS campaigns can be financially rewarding for cybercriminals who can make money for little to no investment. Consequently, several threat actors are now impersonating notorious threat groups and sending out ransom threats, some with no intention of launching an attack, hoping to make a profit.
PHANTOM SQUAD
In 2017, a group claiming to be Phantom Squad, a notable threat group known for launching largescale DDoS attacks in 2015, leveraged its name and emailed ransom letters to thousands of organizations worldwide. At the time, the group was demanding 0.2 Bitcoin (~ $840 US back in the day) under the threat of a DDoS attack. Due to the large number of organizations that received a ransom letter and the low ransom demand, it was quickly determined that the group posing as Phantom Squad could not follow through with their threats. Their objectives were more likely to spread fear and chaos, not drive monetary profit.
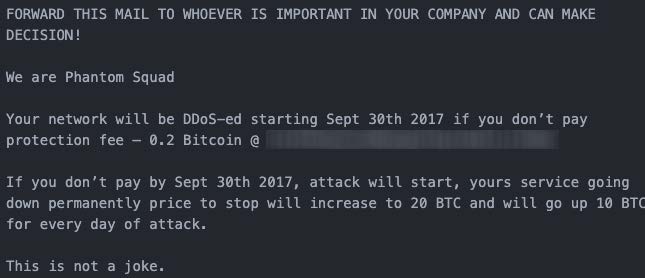 Figure 1: 2017 Phantom Squad RDoS letter
Figure 1: 2017 Phantom Squad RDoS letter
Fast forward five years and Radware is observing signs of either a reemergence of the same fake RDoS threat group or a new threat group leveraging the name and tactics, techniques, and procedures (TTPs) of the former campaign.
On May 22, 2022, a near identical ransom letter from the 2017 Phantom Squad appeared. The only difference between the 2017 letter and the current letter in circulation is the addition of a targeting section, where the threat group provides IP addresses and domain names of their intended targets.
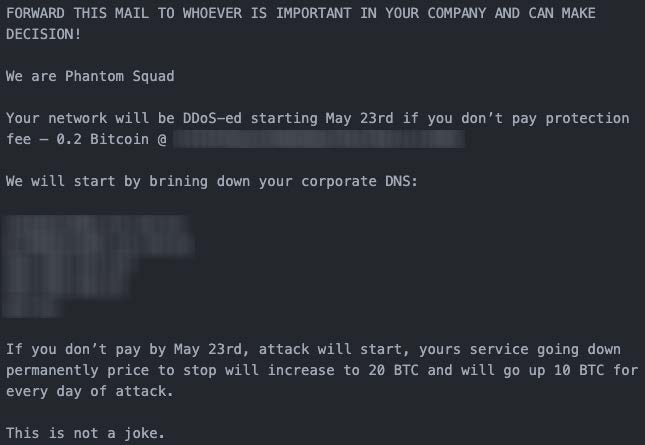 Figure 2: 2022 Phantom Squad RDoS letter
Figure 2: 2022 Phantom Squad RDoS letter
During the 2017 campaign, both the value of the ransom in combination with the total number of victims played a role in determining the threat's validity. In comparison, only one letter has surfaced at the time of writing with no reported or observed outages or demonstration attacks directed at the targeted victims. It is also important to note that the price of Bitcoin has increased significantly over the last five years, resulting in the 0.2 Bitcoin demand now being worth approximately US$6,000 (at the time of publication).
Determining a threat's validity is difficult, but several indicators can be used to determine the risk. Indicators such as how many victims are targeted, how high or low the ransom demand is, and if a demonstration attack was observed. Unfortunately, it is still unknown how many organziations have reveived the current letter in circulation at the time of writing. Radware knows that only one group of victims was targeted and no attacks have been reported. But one suspicious indicator stands out in the current ransom letter: the Bitcoin address.
The Bitcoin address used in the recent ransom letter from the group claiming to be Phanton Squad corresponds to a dormant wallet once used during the notorious Wannacry ransomware campaign in 2017. The threat actors behind the current Phantom Squad RDoS campaign are unlikely those who possess this known cash-in/cash-out wallet address has transacted over 200 times and received an aggregate total Bitcoin value of over $500,000. The current RDoS campaign is likely using the wallet, its transactions and the value to spread fear for yet unknown reasons.
REVIL, THE RDOS GROUP
During one of the many waves of RDoS campaigns in 2021, a group claiming to be REvil targeted several VoIP providers worldwide. At the time, REvil, a notorious ransomware group, had just returned to action after disappearing following the Kaseya VSA ransomware attack. The RDoS campaign sparked concern as critical infrastructure was impacted and resulted in an industry-wide warning from Comms Council UK stating a "coordinated extortion-focused international campaign by professional cyber criminals" targeting IP-based communication services providers during October 2021. And while RDoS attacks typically were considered lower tier threats that are easy to mitigate, Bandwidth.com went on record that the RDoS attacks caused a $700,000 dent in their Q3 revenues and would end up costing them up to $12 million in actual and reputation damages.
During the first quarter of 2022, a renewed campaign of RDoS attacks by a group claiming to be REvil emerged. This time the group is not only sending warning ransom notes before the attack starts, but also embeds the ransom note and demands in the attack payload. The attacks are high-frequency HTTPS GET request floods lasting several minutes and ranging up to several millions of requests per second, targeting online applications and hosts and embedding the ransom message as a readable string in the URL.
Embedding the ransom note in the payload of a DDoS attack is not a new technique. In March 2018, attackers embedded ransom demands in the payload of Memcached DDoS amplification attacks. Taking into account that most online applications are logging the URL of GET requests for troubleshooting, leveraging the URL is not a bad technique to get the demand noticed. Whenever a host or website is deteriorating, the first place to look for potential causes are the log files of the server which will be filled with ransom demands.
Attacks leveraging HTTPS request floods with embedded ransom notes by the actor posing as REvil were first reported in early March, 2022. During those attacks, the first wave of floods contained a message directed at the web operators of the victim (see Figure 3).
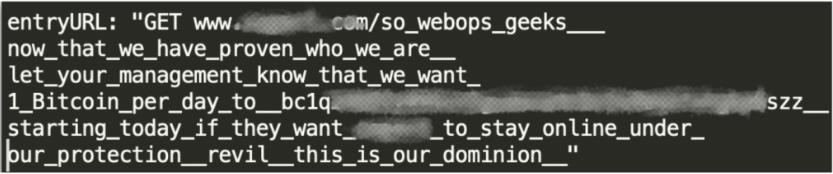 Figure 3: REvil RDoS note embedded in URL of first wave of attacks (source: Imperva)
Figure 3: REvil RDoS note embedded in URL of first wave of attacks (source: Imperva)
As the attacks progressed, the threat group was observed changing the requests' messages to intimidate their victims further. The second wave addressed the CEO of the organization under attack and claimed responsibility for the attacks on service provider Bandwidth.com (see Figure 4).
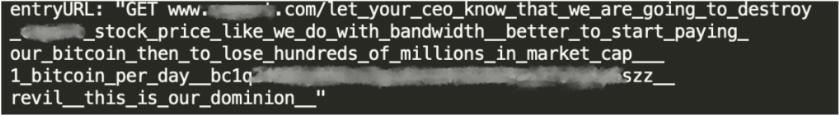 Figure 4: REvil RDoS note embedded in URL of second wave of attacks targetting the same organization (source: Imperva)
Figure 4: REvil RDoS note embedded in URL of second wave of attacks targetting the same organization (source: Imperva)
In early May, 2022, Radware was notified of an RDoS attack with a ransom message embedded in the URL, signed with “REvil, this is our dominion” (see Figure 5). The ransom note differs from earlier reported notes. The threat actors seem to be customizing their demands and messages based on the targetted victim.
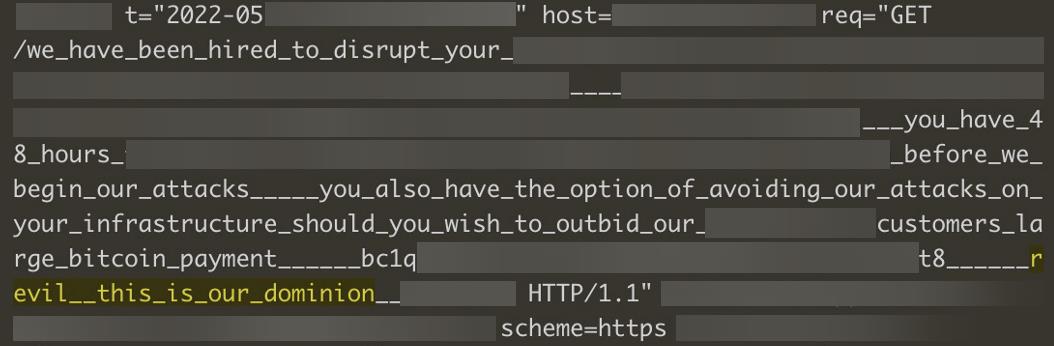 Figure 5: REvil RDoS note embedded in URL and recorded in server log files (source: Radware)
Figure 5: REvil RDoS note embedded in URL and recorded in server log files (source: Radware)
The aggressive attacks lasted several minutes and consisted of millions of HTTPS GET requests per second.