Over 50% of web traffic is comprised of bots, and 89% of organizations have suffered attacks against web applications. Websites and mobile apps are two of the biggest revenue drivers for businesses and help solidify a company’s reputation with tech-savvy consumers. However, these digital engagement tools are coming under increasing threats from an array of sophisticated cyberattacks, including bots.

While a percentage of bots are used to automate business processes and tasks, others are designed for mischievous purposes, including account takeover, content scraping, payment fraud and denial-of-service attacks. Often, these attacks are carried out by competitors looking to undermine a company’s competitive advantage, steal information or increase your online marketing costs.
[You may also like: 5 Things to Consider When Choosing a Bot Management Solution]
When Will You Need a Bot Detection Solution?
Sophisticated, next-generation bots can evade traditional security controls and go undetected by application owners. However, their impact can be noticed, and there are several indicators that can alert a company of malicious bot activity:
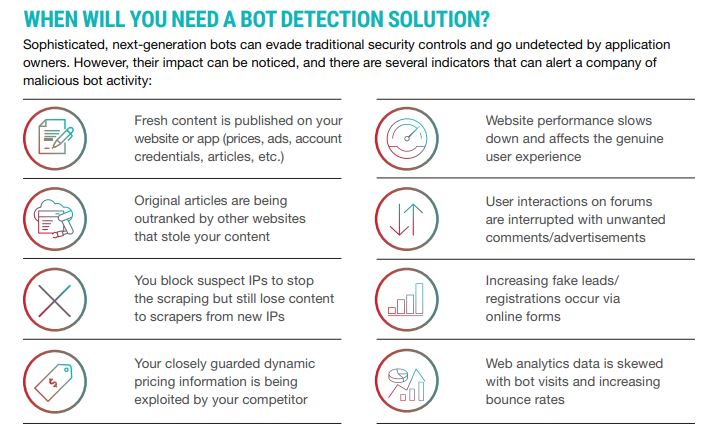
WAFs are primarily created to safeguard websites against application vulnerability exploitations like SQL Injections, cross-site scripting (XSS), cross-site request forgery, session hijacking and other web attacks. WAFs typically feature basic bot mitigation capabilities and can block bots based on IPs or device fingerprinting.
However, WAFs fall short when facing more advanced, automated threats. Moreover, next-generation bots use sophisticated techniques to remain undetected, such as mimicking human behavior, abusing open-source tools or generating multiple violations in different sessions.
[You may also like: The Big, Bad Bot Problem]
Against these sophisticated threats, WAFs won’t get the job done.
The Benefits of Synergy
As the complexity of multi-vector cyberattacks increases, security systems must work in concert to mitigate these threats. In the case of application security, a combination of behavioral analytics to detect malicious bot activity and a WAF to protect against vulnerability exploitations and guard sensitive data is critical.
| Security Capabilities | Bot Manager | Traditional WAFs | Having Both |
| Protection from simple bots | Yes | Yes | Yes |
| Fingerprinting of malicious devices | Yes | Yes | Yes |
| Mitigation of dynamic IP and headless browser attacks | Yes | Limited | Yes |
| Detection of sophisticated bot attacks | Yes | No | Yes |
| Risk of blocking genuine users (False Positives) | Very Low | High | None |
| Collective Bot Intelligence (Ips, fingerprints and behavioral patterns) | Yes | No | Yes |
| Customized actions against suspicious bot types | Yes | No | Yes |
| Protection from OWASP Top 10 vulnerabilities | No | Yes | Yes |
| Protection from OWASP Top 21 Automated Threats to Web Apps | Yes | Limited | Yes |
| Protection from API vulnerabilities | Partial | Yes | Yes |
| Protection against Layer 7 denial of service (DoS) | Partial | Yes | Yes |
| HTTP traffic inspection | No | Yes | Yes |
| Masking of sensitive data | No | Yes | Yes |
| Compliance with HIPAA, PCI, & GDPR | Yes | Yes | Yes |
| Integration with DevOps | Partial | Yes | Yes |
| Blocking of malicious sources at the network level—access control list (ACL) | No | Yes | Yes |
Moreover, many threats can be blocked at the network level before reaching the application servers. This not only reduces risk, but also reduces the processing loads on the network infrastructure by filtering malicious bot traffic.
Like this post? Subscribe now to get the latest Radware content in your inbox
weekly plus exclusive access to Radware’s Premium Content