In the ever-evolving digital landscape, the importance of securing online communication cannot be overstated. SSL/TLS certificates play a crucial role in encrypting sensitive data, ensuring confidentiality and integrity. However, safeguarding the private keys associated with these certificates is often overlooked. While most of our customers are comfortable with sharing their private keys, some have unique security requirements making this impossible.
Enter CWAP NoKey – a new technology designed to address this security concern. In this blog, we will delve into the intricacies of SSL/TLS, the challenges it poses, and how NoKey emerges as a game-changer in the realm of encryption.
The Encryption Dance: SSL/TLS in Action
At the core of SSL/TLS lies encryption, a process that transforms sensitive information into an unreadable format. When you visit a secure website (indicated by 'https://'), SSL/TLS encrypts the data exchanged between your browser and the server, thwarting any attempts at interception.
The Significance of SSL/TLS Certificates
SSL/TLS certificates are the backbone of secure connections, enabling websites and applications to establish encrypted communication. These certificates not only authenticate servers but also ensure that data exchanged between clients and servers remains private and integral.
NoKey: Empowering Organizations with Control
Introducing NoKey – a tailored service for organizations leveraging a cloud vendor for SSL/TLS encryption. Traditionally, sharing private keys with cloud vendors poses security and compliance challenges. NoKey circumvents this by allowing organizations to retain control of their private keys while still benefiting from the security features of CWAP.
The SSL/TLS Handshake: Making Connections Securely
The SSL/TLS handshake acts as a digital introduction between your browser and the server. This process involves agreeing on encryption methods, ensuring a common language for the exchange of sensitive information. Certificates play a pivotal role during this handshake, acting as digital IDs for websites.
Key Exchange with NoKey: A Secure Journey
The SSL/TLS handshake process with NoKey involves a meticulous key exchange. Instead of the cloud vendor directly decrypting the premaster secret, CWAP sends it encrypted to the Key Server the customer hosts and controls. The customer's private key, securely stored in an HSM, decrypts the secret, and the parameters are exchanged over an encrypted channel. This process ensures the private key remains exclusively in the company's possession.
NoKey: How it Works
NoKey leverages the insight that the private key uses only once during the TLS handshake. It divides the TLS handshake based on location, ensuring that operations requiring the private key happen on a server maintained by the customer rather than on CWAP. This improves security and complies with regulations that forbid sharing private keys.
Here is an overview of the Diffie-Hellman SSL/TLS handshake combined with the NoKey solution:
ClientHello: The process begins with the client sending a "ClientHello" message to the server. This message includes information such as the SSL/TLS version supported by the client, a random number, and a list of cipher suites and compression methods that the client can use.
ServerHello: Upon receiving the "ClientHello" message, the server responds with a "ServerHello" message. This message includes the selected SSL/TLS version, a random number, and the chosen cipher suite and compression method from the options provided by the client.
Server Key Exchange: server picks some starting parameters and sends them to the client. The server also needs a way to prove that it has control of the private key. During this phase, NoKey extends the TLS handshake, necessitating modifications to the NGINX server and OpenSSL to enable remote private key operations.
- CWAP sends a hash to the KeyServer.
- KeyServer sends the hash to the customer's HSM.
- The customer's HSM signs the hash.
- KeyServer returns the signature to CWAP.
Server Certificate: The server then sends its digital certificate to the client. This certificate contains the server's public key and is signed by a Certificate Authority (CA), providing a means for the client to authenticate the server.
Client Key Exchange: The client verifies the server's certificate and, if successful, generates a pre-master secret. This secret is encrypted with the server's public key and sent back to the server.
Key Derivation: Both the client and server independently generate the session keys.
Finished: The client and server exchange "Finished" messages, which include a hash of all the exchanged messages so far. These messages confirm that the handshake is complete, and both parties can now begin encrypted communication using the negotiated parameters.
Secure Data Exchange:
With the session keys derived from the pre-master secret, the client and server can encrypt and decrypt data, ensuring the confidentiality and integrity of the communication. The SSL/TLS handshake establishes a secure communication channel by authenticating the server, exchanging cryptographic parameters, and generating session keys. This process ensures that the data exchanged between the client and server remains confidential and secure.
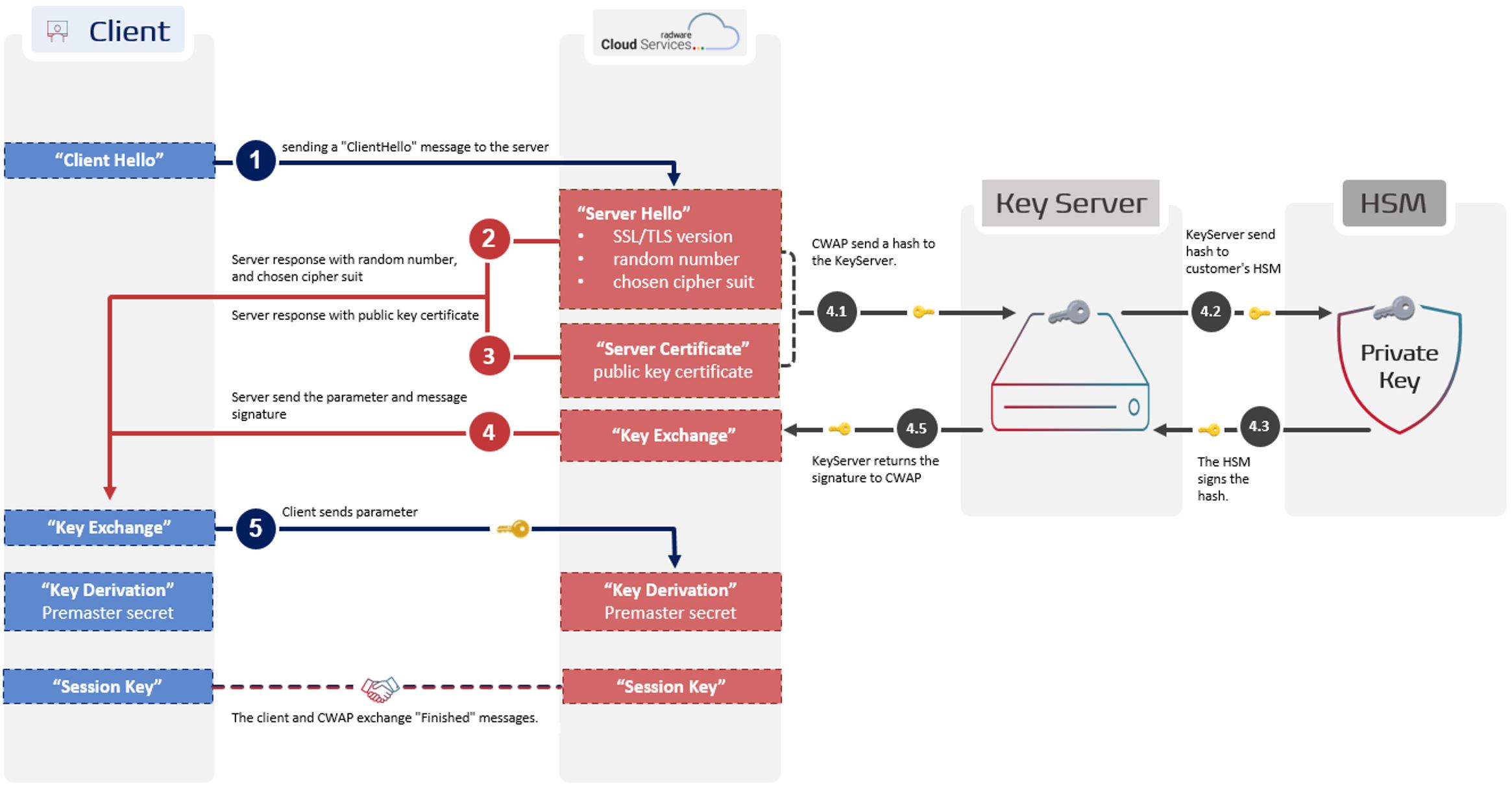
Figure1: NoKey Diffie-Hellman SSL/TLS handshake.
Navigating the Future of SSL/TLS Security
CWAP NoKey emerges as a beacon of innovation in the realm of SSL/TLS security. By empowering organizations to retain control of their private keys, NoKey not only addresses compliance concerns but also provides a streamlined and secure approach to encryption in cloud environments. As we continue to navigate the dynamic landscape of cybersecurity, embracing technologies like NoKey becomes imperative for ensuring the confidentiality and integrity of sensitive data. Stay tuned for more insights into the evolving world of encryption and security.
The NoKey solution is available to CWAP customers starting February 2024.