The combination of seamless user experiences and increasing consumer confidence in online transactions has enabled the digital economy to reach unprecedented heights, with millions of consumers adopting online platforms for their shopping or financial needs. Major shopping events like Black Friday and Cyber Monday alone generate billions in online transactions, making it the ultimate proving ground for online retailers, and coincidentally, also for cybercriminals. While genuine customers hunt for the best deals during these sales events, malicious actors hunt for access to user accounts loaded with cash, payment information, and sensitive personal data.
This past year, one of our major retail clients faced exactly this scenario- a sophisticated, large-scale Account Takeover (ATO) attack targeting their login workflows during the biggest shopping event of the year. Thanks to robust protection provided by the Radware Bot Manager, a major security breach was successfully averted while customers felt no impact on their shopping experience.
ATO Attacks 101
Account Takeover (ATO) attacks are one of the most damaging forms of cyberattacks targeting online businesses today. These attacks involve cybercriminals gaining unauthorized access to user accounts through various methods, including bot-driven credential stuffing/cracking, API business logic attacks, and social engineering techniques. Once successful, attackers exploit compromised accounts for fraudulent purchases, sensitive data theft, or serve as the foundation for larger attacks.
While ATO attacks are one of the biggest cyber threats faced year-round by organizations across sectors, highly anticipated events such as Black Friday, Cyber Monday, etc. represent the perfect mix of opportunity and vulnerability for attackers. The massive surge in legitimate traffic during these events, with customers actively using stored payment methods or updating sensitive information, makes successful account compromises immediately valuable and monetizable through account fraud.
Anatomy of an ATO Attack
Over the course of this past holiday shopping season, one of our client’s e-retail platforms was targeted with a sustained ATO attack campaign, with over 500,000 account takeover attempts recorded in a period of 30 days.
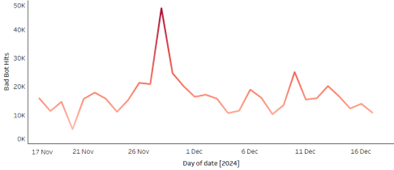
Noticeably, on the day before Black Friday and leading up to the event launch, a spike of 50,000 malicious login attempts was detected – a 200% increase in bad bot traffic volume compared to typical daily patterns.
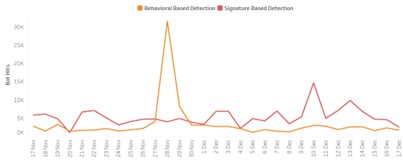
Perhaps most concerning was the extremely high share of sophisticated bad bots - 90% of malicious bots on this day were identified using advanced behavior-based detection capabilities, indicating that attackers launched their most advanced bots when they expected the highest user activity, and hence the best ROI for their efforts. The trend of sophisticated attacks detected continuously increased throughout the day, peaking around midnight at the time of the event launch. These were highly evasive bad bots mimicking human-like interaction patterns while attempting to blend in with the heightened genuine user traffic.
The attackers attempted to bypass traditional security measures through a highly distributed operation, with the spike in attacks originating from over 600 unique IPs and more than 6,000 unique user agents. The attackers also routed a share of their malicious requests through residential proxy networks, which are considerably more difficult to detect since they appear to originate from legitimate home internet connections. The attack originated from over 50 countries, including those shown below, creating a wide geographic distribution aimed at challenging traditional geo-based blocking mechanisms. These tactics enable the attackers to maintain the appearance of geographically distributed, genuine user behavior in an attempt to evade signature-based protections.
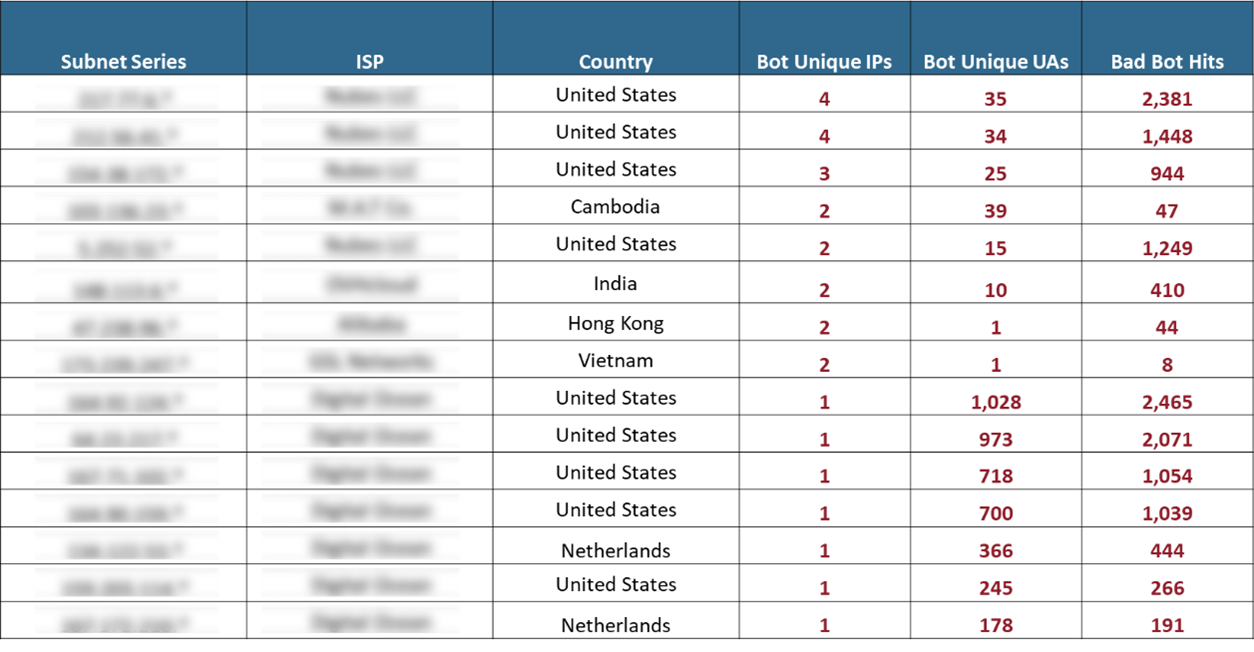
The attackers also adopted identity rotation techniques, where IP addresses were systematically rotated to prevent rate-limiting actions and user agents were continuously alternated to simulate different browsers and devices.
Tracking the traversal of one specific IP address during the peak day of the attack gives a deeper insight into the evasion tactics adopted by the attacker. Multiple user agent variations were involved during the attack that originated from this single IP address. For each login attempt that was blocked, the next login re-attempt used a different user agent, as shown in the table below.
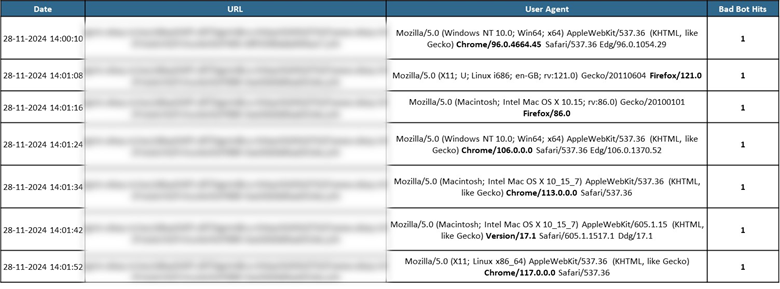
This specific IP was active for only two hours during the attack, but during this time, it rotated among 1028 unique user agents in a low and slow approach, with a maximum of 8 attempts per user agent.
AI-powered Real-Time Detection & Mitigation: Radware Bot Manager in Action
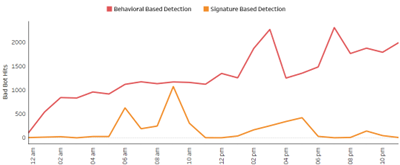
- Over the course of the attack campaign, the Radware Bot Manager’s AI-powered behavior-based detection engine flagged the sophisticated bot activity in real-time, accurately identifying anomalies in login behavior by the automated ATO attempts that deviated from established baselines. Key behavioral signals identified by our advanced detection modules include the distributed nature of the attack, abnormal IP and user agent rotations, and the low and slow attack patterns, among various other behavioral anomalies.
- Highly accurate and granular signatures were generated in real-time to mitigate the attack as new sophisticated attack patterns emerged, ensuring that the defense adapted as quickly as the threat evolved. Advanced mitigation challenges were deployed to effectively block the attack.
- Most importantly, throughout the attack campaign and the holiday shopping season, genuine customers had a seamless user experience, being able to log in and securely access their accounts without friction, while malicious actors were effectively blocked.
Business Impact Averted
With 500,000+ malicious ATO attempts blocked in just 1 month and many more over the course of the holiday shopping season, the Radware Bot Manager helped the client avoid potentially devastating consequences that follow such attacks, including:
- Fraudulent account transactions
- Additional operational overheads
- Regulatory non-compliance, and
- Long-term reputational damage associated with data breaches
Successfully thwarting the attack and ensuring the integrity of the shopping experience during one of the most critical sales periods directly translated to preserved revenue and brand reputation for the business, earning the loyalty and trust of customers.
Final Takeaway
This attack and its successful mitigation by the Radware Bot Manager highlight the significance of real-time, proactive measures for protection from modern, sophisticated ATO campaigns. Organizations cannot rely on static defenses or reactive approaches when facing attackers who are constantly evolving their tactics. With attackers using sophisticated evasion techniques and relying on residential proxies, the combination of AI-powered behavioral analysis, real-time mitigation, and use of advanced mitigation techniques is far more effective than traditional signature-based protection.
For organizations that handle large-scale online transactions, the question isn’t whether you’ll face similar attacks, but whether you’ll be ready when you do. Contact us to learn more about how the Bot Manager with Radware’s Cloud Application Protection Services provides proactive, AI-powered ATO protection.