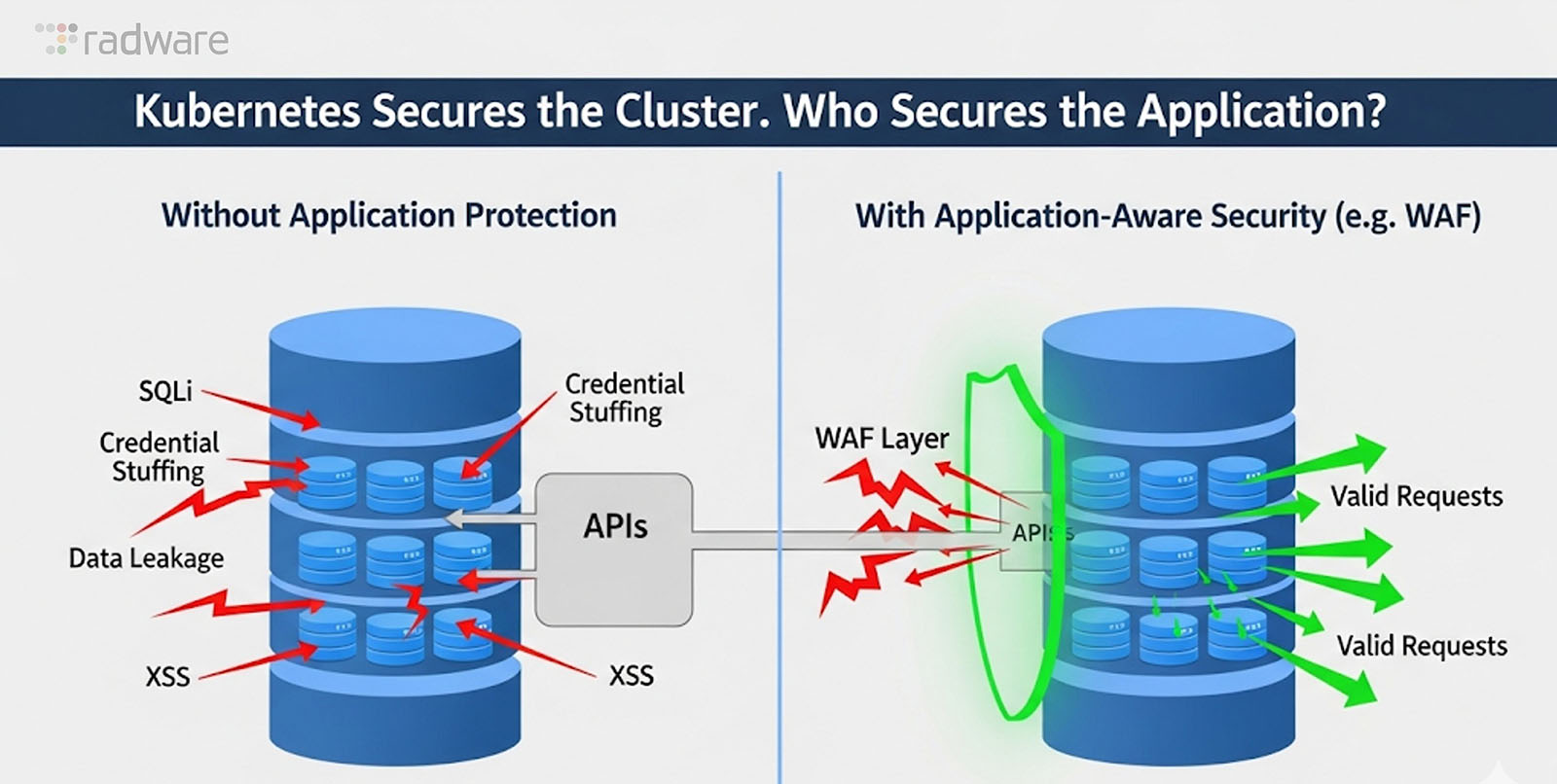
Kubernetes has become the backbone of modern IT, running millions of workloads across cloud, hybrid, and on-prem environments. It delivers scalability, agility, and resilience at a scale the traditional systems could never match. But there’s one thing Kubernetes was never designed to do: secure the application itself.
Yes, Kubernetes enforces pod isolation, RBAC, and traffic control. What it doesn’t do is inspect an API call, validate a login attempt, or detect a malicious payload. And in today’s world, where APIs power more than 80% of all web traffic, that blind spot is too big to ignore.
The Gap Kubernetes Can’t Close
Kubernetes was built to orchestrate containers, not to analyze application behavior. Its strength lies in keeping clusters resilient, not defending business logic. Once traffic reaches the workload, Kubernetes simply assumes it’s safe. That’s where attackers step in.
- APIs as the weak link
Modern applications expose dozens or even hundreds of endpoints. Each is a potential target for fuzzing, enumeration, or injection attempts. Kubernetes can route the requests, but it doesn’t validate them leaving the burden on the application itself. To know more, visit Kubernetes WAF
- Injection attacks in application code
SQL injection, NoSQL injection and OS command injection exploit flaws in the way applications process input. These are payload-level threats that Kubernetes cannot detect, because it never inspects the body of a request.
- Credential abuse and bot automation
Attackers routinely run credential stuffing or brute-force campaigns using stolen credentials. To Kubernetes, this looks no different than legitimate traffic, so account takeover attempts slide by unnoticed.
- Silent data exfiltration
Sensitive data like payment details or health records may be exposed through responses. Kubernetes has no native way to recognize or stop this leakage, which can lead to compliance failures and reputational damage.
- Encrypted traffic blindness
As TLS adoption has become universal, most malicious activity is hidden within encrypted flows. Kubernetes terminates or routes the traffic but doesn’t analyze what’s inside, giving attackers a shield to operate under.
Closing the Gap
Kubernetes secures the infrastructure, but real threats today live higher up in APIs, login flows, and data transactions. Addressing them requires defenses designed for the application layer. While Kubernetes provides the foundation, specialized protections extend it into the places attackers strike.
- API-first protection
Modern defenses validate schema compliance, enforce proper authentication flows, and inspect payloads in real time. That means abnormal calls, injection attempts, and endpoint enumeration can be blocked before they reach sensitive logic. To know more visit Radware Api Protection.
- Application-layer threat coverage
Classic risks like injection, XSS, and broken authentication remain top causes of breaches. Application-aware security tools detect these within live traffic, shutting them down early instead of leaving them for developers to catch post-incident.
- Behavior tracking, not just request inspection
Attackers rarely reveal themselves in one packet they operate in patterns. Credential stuffing, scraping, and probing all behavioral footprints. Activity tracking connects those dots, isolating suspicious sessions while keeping genuine users uninterrupted.
- Clarity instead of alert floods
Raw logs alone overwhelm teams. Modern solutions separate malicious activity from legitimate traffic, enrich events with context (attack type, target API, payload), and provide structured insights for faster response.
- Visibility and control on your terms
Real-time dashboards offer immediate awareness of threats, while CLI and automation options let DevOps teams manage protection the way they prefer. Security doesn’t have to be a roadblock; it can be integrated seamlessly into development and operations.
Final thoughts
Kubernetes secures the cluster. But the real battlefront lies deeper in the application layer, where APIs, data, and users intersect. Organizations that stop at infrastructure security leave the door open. Those that extend protection into the application stack close the gap that attackers are counting on.
To explore how application layer protections like advanced Web Application Firewalls (WAF) and advance protection features can help address these challenges, you can learn more about Kubernetes on Radware's Official site.