Building Your Ultimate Defense Strategy: Mastering Security Policy for Cloud Applications
In the world of cloud security, managing configurations can feel like playing a high-stakes strategy game. Every setting, every rule, and every policy decision impacts the security posture of your applications. One misstep and vulnerabilities can open the gates to attackers.
Today’s threat landscape is evolving rapidly, with sophisticated cyberattacks targeting misconfigurations, outdated policies, and human error. Security teams need more than just reactive defenses—they need a proactive, strategic approach that simplifies security enforcement while maximizing protection.
That’s why Radware is introducing Security Policy, a centralized solution designed to take the complexity out of security configurations and empower teams to deploy protections efficiently and at scale.
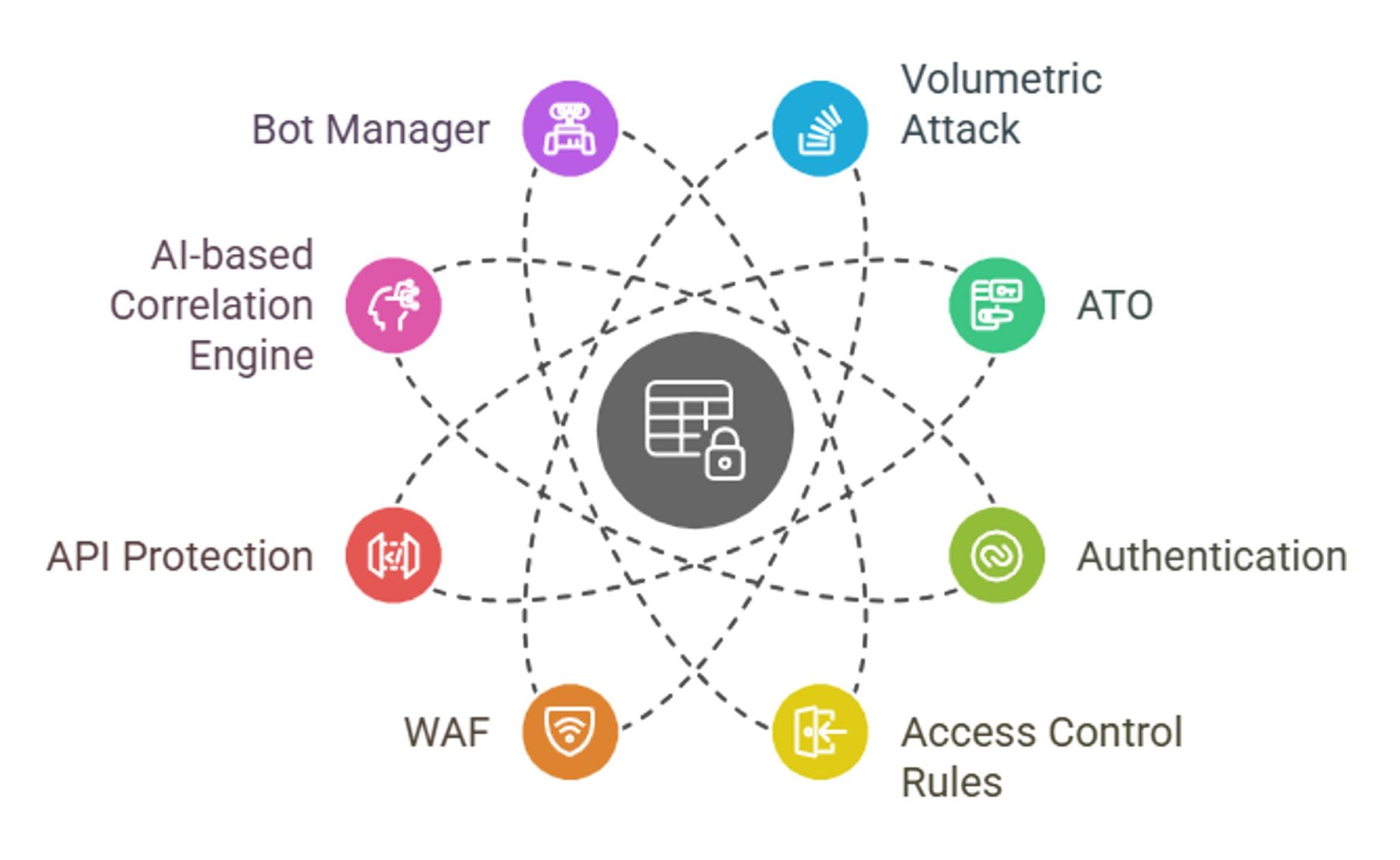
Image 1: Comprehensive Security Management Overview
Mastering the Battlefield of Application Security
Think of your applications as a vast digital kingdom. Without a well-planned defense strategy, attackers can find weak spots and breach your fortress. Relying on outdated manual security configurations is like defending a castle with wooden gates—it simply won’t hold up against modern threats.
Security Policy acts as your central command center, allowing you to build, refine, and deploy robust protection strategies across multiple applications—without having to configure each one manually.
But what does this mean in practice? Let’s break it down:
Centralized Control: One Template to Rule Them All
Managing security across multiple applications can lead to inconsistencies and misconfigurations. Security Policy provides a single, centralized template that ensures uniform protections, simplifies deployment, and reduces the risk of human error. Instead of manually configuring each application, teams can apply security settings from one place, maintaining a consistent and scalable defense strategy.
A key advantage of using a template is the ability to review configurations and track changes before they impact live traffic. Security teams gain full visibility into every modification, understanding what was changed, who made the change, and how it will affect application security. This proactive approach prevents misconfigurations, ensures compliance, and minimizes disruptions.
With a centralized security policy, organizations can confidently enforce protections without the risk of unintended consequences. Security teams stay in control, applications remain secure, and operations run smoothly without last-minute surprises.
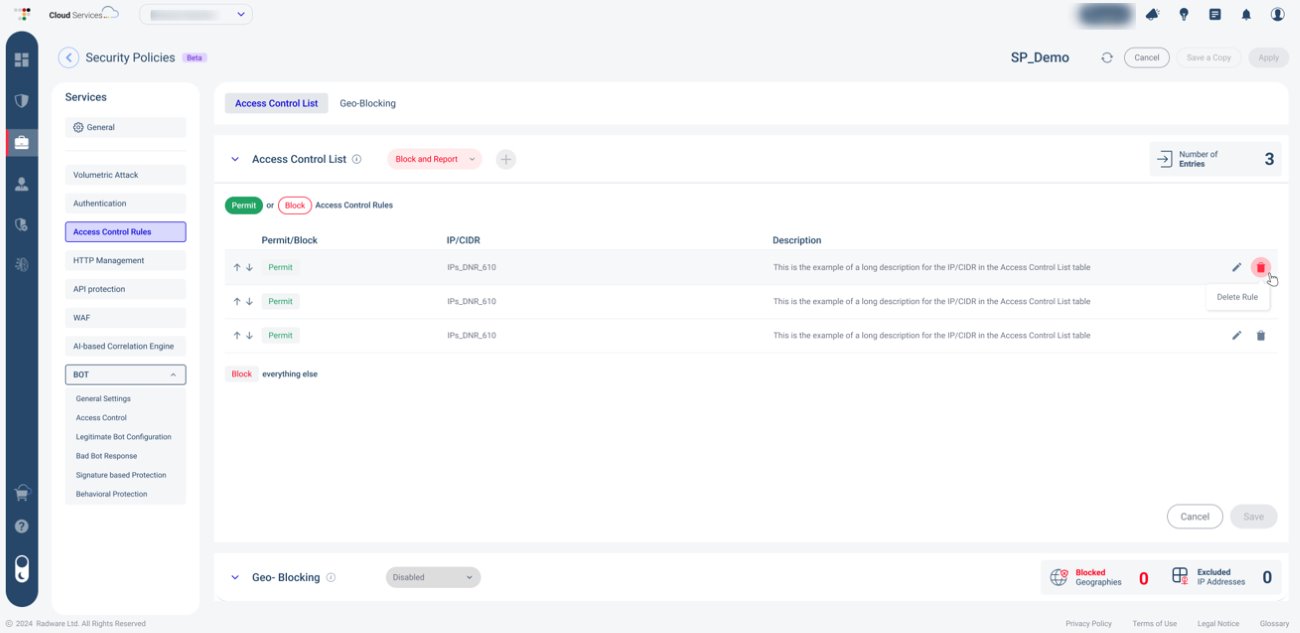
Image 2: Present Centralized Control for all protections
Version Control: Your “Checkpoint Save” for Security Policies
Mistakes happen, even with the best strategies. A misconfigured security rule can expose applications to vulnerabilities or disrupt functionality. Security Policy offers version control, allowing teams to track policy changes and revert to previous configurations if needed.
By maintaining a complete history of security policy updates, teams can identify what changed and when. If an issue arises, rolling back to a stable version ensures that applications remain secure without downtime or misconfigurations. This structured approach reduces risks and ensures that security policies evolve without compromising reliability.
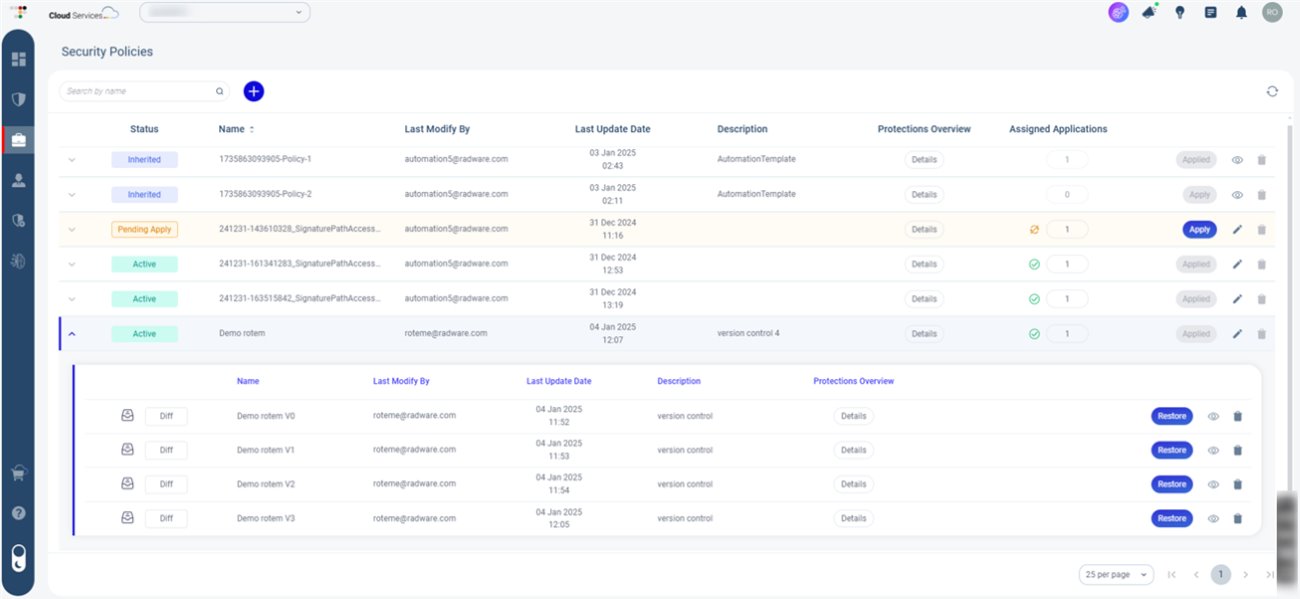
Image 3: Present Security Policy template with the last 5 versions
Staging and Seamless Deployment: Test Before You Go Live
Security settings should never be applied without proper validation. Security Policy allows teams to stage configurations in a controlled environment before enforcing them in production, ensuring that changes do not disrupt application functionality. By simulating new security policies, teams can confirm their effectiveness, address potential issues, and refine protections before they impact live traffic.
Once security policies are tested and validated, transitioning them to production is seamless. Instead of manually replicating configurations—which can introduce human error—Security Policy automates the process, preserving settings exactly as intended. This eliminates inconsistencies, reduces deployment time, and ensures a smooth, error-free transition from test to production.
With a structured staging and deployment approach, organizations can confidently roll out security updates without the risk of breaking applications or exposing vulnerabilities.
Multi-Application Deployment: Defend Your Entire Kingdom at Once
Configuring security settings for each application individually is inefficient and prone to errors. Security Policy allows organizations to apply a single security template across multiple applications, streamlining deployment while maintaining consistency.
Instead of securing applications one by one, security teams can enforce standardized protections across all environments in a fraction of the time. This approach ensures that every application receives the same level of security, eliminating gaps and inconsistencies that attackers could exploit.
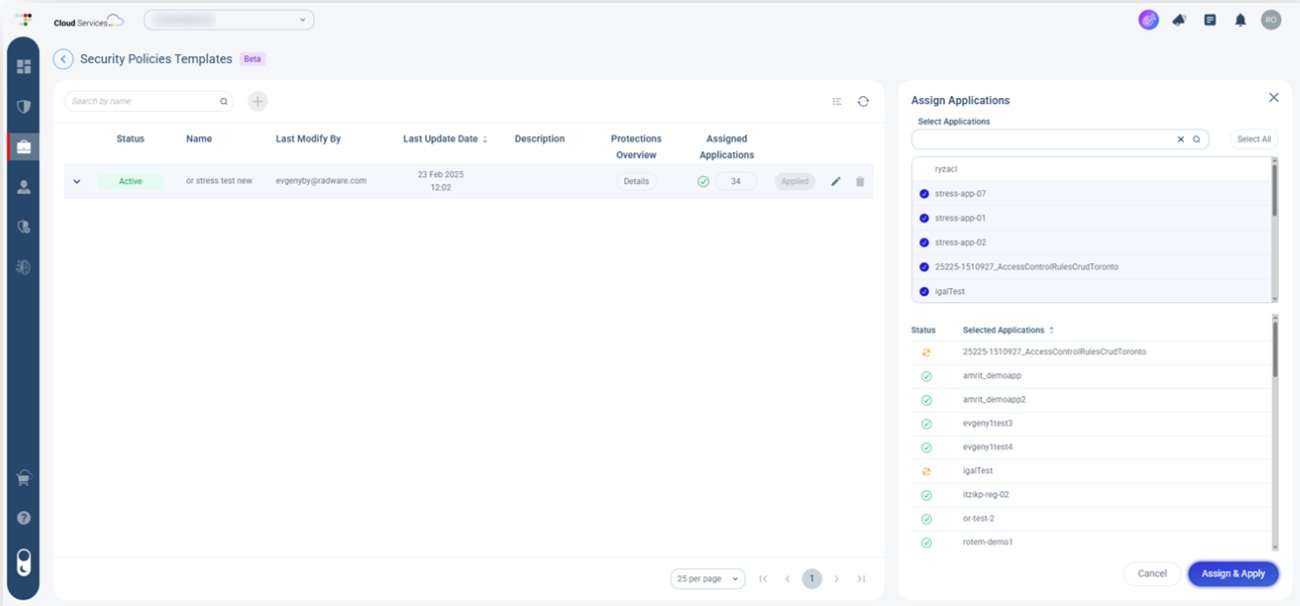
Image 4: Deploy application configuration on multi-applications
Global Policy Updates: One Change, Instant Reinforcement
Cyber threats evolve constantly, and security defenses must adapt just as quickly. Security Policy allows teams to update security templates globally, ensuring that improvements are instantly applied across all protected applications.
When an attack vector changes, security teams can refine protections in a single location, and those updates are automatically distributed across the organization. This proactive approach ensures that applications remain secure without delays or vulnerabilities caused by outdated policies.
To summarize: Security Policy is your Best Playbook Against Application Threats
Radware’s Security Policy is designed to give security teams a strategic advantage. It simplifies security management, ensures consistency, and enables organizations to respond to evolving threats with agility.
By centralizing security configurations, preventing misconfigurations, and enforcing protections at scale, Security Policy helps organizations stay ahead of cyber threats. Instead of relying on outdated, manual processes, security teams can take full control of their cloud security strategy with a solution built for efficiency and reliability.
Cyber threats are always changing. Security defenses should be just as dynamic. With Security Policy, organizations can deploy, manage, and enforce protections with confidence, ensuring that applications remain secure without unnecessary complexity.
Streamline your security management by migrating to the new Security Policy framework. Click the "Migrate To Security Policy" button in your application for a seamless upgrade.
Learn more about Radware's cloud services and Security Policy in our comprehensive User Guide.