Encryption is a widely used technique to protect data from unauthorized access and tampering. However, encryption also poses a challenge to network security, as it prevents the inspection of traffic content and metadata. This means that malicious actors can use encryption to hide their attacks, and sensitive data can be leaked without detection. In the following, I will cover why visibility into encrypted traffic is vital for network security, and how an SSL Inspection solution can help you achieve it.
The Risks Of Encrypted Traffic on Network Security
Encryption helps provide data security for sensitive information that is stored on computer systems or transmitted via computer networks. Encryption is an important privacy tool when you are sending sensitive, confidential or personal information across the internet. However, encryption can also be exploited by hackers for malicious purposes. Some hackers use encryption to hide malware from antivirus software and security tools. They may use code packing and encryption utilities to process their files and make them harder to detect and analyze. Other hackers use encryption to create ransomware, a type of malware that encrypts the victim's data and demands money for the decryption key. Ransomware can cause serious damage to individuals and organizations by locking them out of their important files and systems.
Therefore, encryption is a double-edged sword that can be used for good or evil. While it can protect our privacy and security online, it can also be used by cybercriminals to launch sophisticated attacks and evade detection. To defend against these threats, network security devices are needed that can inspect the encrypted traffic and identify and block malicious content, such as malware, phishing, ransomware or data exfiltration.
SSL Inspection For Encrypted Traffic Analysis
SSL inspection is a technique that allows network administrators to monitor and analyze encrypted traffic on their networks. SSL inspection works by intercepting and decrypting SSL/TLS packets that are exchanged between clients and servers, and then re-encrypting them before sending them to their destinations. This way, network administrators can inspect the content and metadata of encrypted traffic, such as URLs, headers, cookies, certificates and payloads.
SSL inspection provides several benefits for encrypted traffic analysis, such as:
Enhancing network security: SSL inspection can help detect and block malicious traffic that uses encryption to evade traditional security tools, such as firewalls, antivirus solutions and intrusion detection systems. SSL inspection can also prevent data leakage and unauthorized access by verifying the identity and integrity of the servers to which clients connect.
Complying with regulations and policies: SSL inspection can help network administrators comply with various regulations and policies that require them to monitor all data by ensuring visibility into encrypted traffic and enforcing policies on data protection and privacy.
Gaining visibility: SSL inspection allows for visibility into employee traffic and ensures business information is not leaked, either mistakenly or on purpose.
What To Look For In An SSL Inspection Solution
If you want to protect your network from cyber threats, you need to have full visibility into the encrypted traffic that flows through it. SSL inspection is a technique that allows you to decrypt, analyze and re-encrypt SSL/TLS traffic, so you can detect and block malicious content hidden in HTTPS connections. However, not all SSL inspection solutions are created equal.
Here are some key features you need in an SSL inspection solution.
- High Volume SSL Traffic Inspection:
SSL encryption adds overhead to network performance and decrypting it can slow down your network even more. You need an SSL inspection solution that can handle high volumes of SSL traffic without compromising speed or security. Look for solutions that use hardware acceleration and load balancing to optimize SSL inspection performance.
- Decrypt Once, Inspect Many:
Some SSL inspection solutions require you to decrypt SSL traffic multiple times for different security functions, such as antivirus, web filtering and data loss prevention. This can create redundancy and inefficiency in your network. A better approach is to use a solution that can decrypt SSL traffic once and steer it through multiple security inspection tools before re-encrypting it, which reduces the processing load and improves network performance.
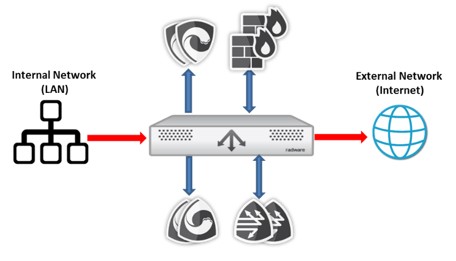
- Granular Traffic Inspection Policies:
Not all SSL traffic needs to be inspected. Some traffic can be trusted, such as internal applications or whitelisted domains. Some traffic may be sensitive, such as banking or healthcare websites. You need an SSL inspection solution that allows you to define granular policies based on various criteria, such as source, destination, application or content type. This way, you can inspect only the traffic that poses a risk to your network and avoid unnecessary decryption or privacy violations.
- Flexible Deployment Options:
SSL inspection can be deployed in different ways depending on your network architecture and security needs. You can choose between inline (Layer 2 “bump-in-the-wire" or Layer 3) or explicit proxy deployment. You might need a wide variety of security inspection tools — active, passive, ICAP. You need an SSL inspection solution that offers flexible deployment options that suit your network environment and scalability requirements.
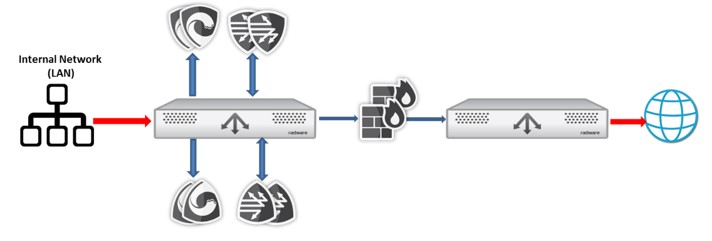
The SSL Inspection Solution That Has It All
Radware’s Alteon SSL Inspect is a solution that provides high-performance visibility into enterprise SSL/TLS traffic. It removes the blind spot introduced by the rising use of SSL/TLS and allows security tools to inspect all traffic for possible breaches and leaks.
Alteon SSL Inspect acts as a central switching point for all perimeter network security tools. Security managers can chain and provision security services with highly granular policy options per user profile. SSL Inspect supports highly available, scalable and flexible security services deployment and reduces overall security solution costs via offloading decryption and re-encryption of SSL encrypted traffic.
To speak with a Radware cybersecurity professional about how Radware’s Alteon SSL Inspect can remove blind spots from your infrastructure’s perimeter, reach out to them HERE. They would love to hear from you.