DNS is a critical infrastructure for your online services, a DNS DDoS attack risks the availability of your services. Attackers are experts in DNS and know all the weak points to target. Understanding how a DNS DDoS looks like, and the risks it poses to your business is key to designing a robust DNS security posture.
DNS is the cornerstone of the Internet
The Domain Name System (DNS) is a critical component of the internet infrastructure. DNS is responsible for resolving hostnames into IP addresses. If DNS fails, online applications, services and third-party web APIs that many applications depend on, will become unavailable. DNS service is increasingly becoming a prime target for Distributed Denial of Service (DDoS) attacks.
DNS DDoS attacks can cause significant disruptions to internet services, resulting in service unavailability, slow response times, and even complete network outages. These attacks can also lead to significant financial losses and damage to a company's reputation.
As attackers become more sophisticated, the risks associated with DNS DDoS attacks continue to grow. In recent years, we have seen an increase in the scale and frequency of DNS DDoS attacks, and attackers are constantly innovating new techniques to evade detection and cause maximum damage.
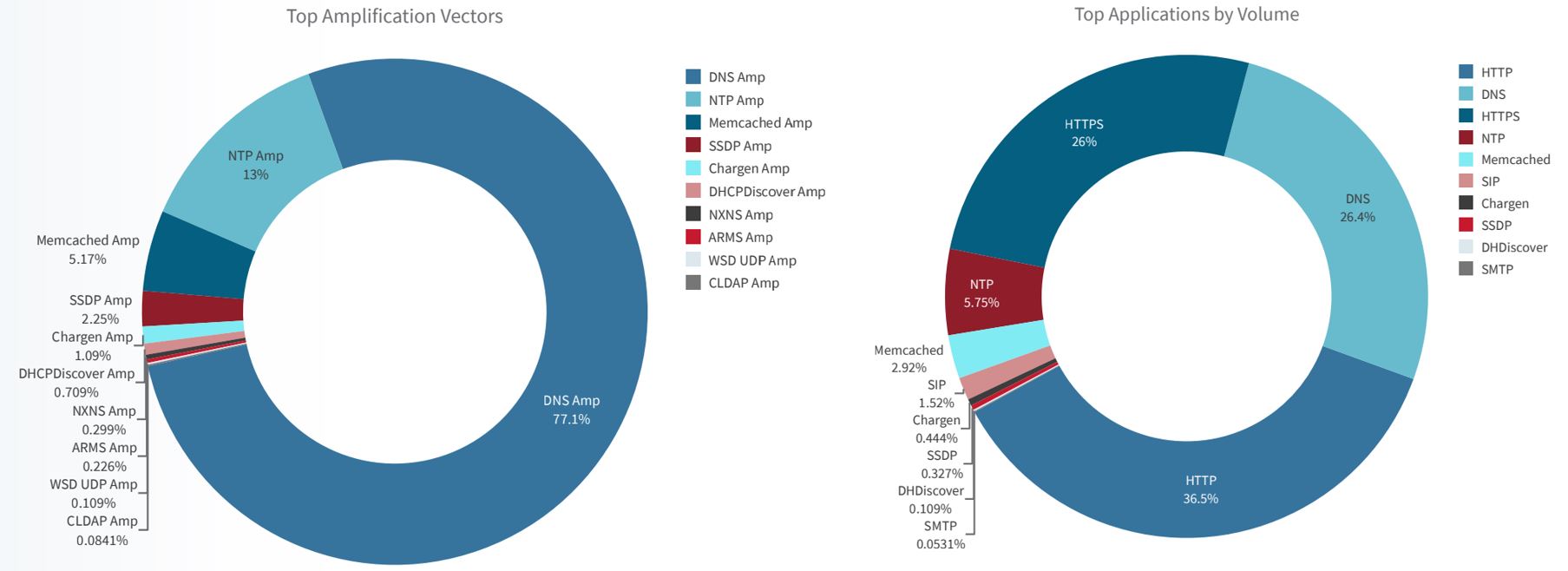
Radware’s 2022 global threat analysis reports found that the Domain Name System (DNS) represented 26.4% of the targeted applications. DNS amplification was the amplification attack vector that generated the most attack volume in 2022, representing 77.1% of the total amplification volume.
In the past several months, we have witnessed a significant rise in DNS Flood attacks. We have encountered multiple DNS attacks affecting various organizations. In April 2023, we recorded the most significant DNS Flood over the past two years, with a peak attack rate reaching 1.29 million DNS queries per second [1].
DNS Security Is Still Weak
While DNS plays a vital role on the internet, it remains alarmingly weak, vulnerable to various threats. Among these threats, DDoS attacks targeting DNS infrastructure have emerged as a significant concern. Here are the main reasons for this:
Complex and Decentralized Infrastructure
The distributed architecture of DNS, designed for redundancy and efficient resolution, inadvertently creates a multitude of potential targets for attackers. Each DNS resolver and authoritative server represents a potential weak link that can be exploited in a DDoS attack.
Insufficient Network Capacity
DNS infrastructure is built to handle a massive volume of queries daily. However, the increasing scale and frequency of DDoS attacks have revealed the vulnerability of DNS to overwhelming traffic. Attackers leverage botnets and amplification techniques to flood DNS servers with an unprecedented number of requests, overwhelming their processing capacity. As a result, legitimate users are unable to access the desired websites or services, leading to widespread disruptions.
Limited Authentication and Validation
Traditionally, DNS lacked robust authentication and validation mechanisms, making it susceptible to various attacks, including DDoS. The absence of strong measures to verify the authenticity of DNS responses enables attackers to manipulate DNS records, redirect legitimate traffic, or launch amplification attacks. While efforts like DNSSEC (Domain Name System Security Extensions) have been introduced to enhance the integrity of DNS data, its adoption remains limited, leaving a significant portion of the DNS ecosystem vulnerable to exploitation.
Incomplete Adoption of Best Practices
Despite the availability of best practices and security guidelines, the implementation of these measures across the DNS landscape remains inconsistent. Organizations responsible for managing DNS infrastructure, including ISPs, domain registrars, and administrators, often fail to prioritize security measures or lack the necessary expertise. This negligence leads to the persistence of outdated software, misconfigurations, and weak defenses, which attackers readily exploit.
DNS DDoS attack: behind the scenes
Attackers take advantage of the weak points in DNS to launch attacks using various techniques. With DNS mostly over UDP, attackers can easily hide the original source IP by spoofing, leverage botnets to achieve scale, reflect the attack queries from open resolvers or ISP resolvers, and use amplification techniques to flood the DNS servers.
Now, let's take a closer look inside the attacker's toolkit to learn about the main steps for launching a DNS DDoS attacks:
Step 1: Planning
An attack, as any project, starts with planning. The attacker first chooses his target DNS name servers. He needs to map the root domains he wants to attack. For that purpose, he can send legitimate requests in low volume to map the domain and some subdomains.
Step 2: DDoS Attack Tool
The attacker can develop a new DDoS attack tool from scratch; however, this is more complicated and can take too long. Nowadays, the attacker's life is made easy with the prosperity of ready "off-the-shelf" DDoS attack tools available on the Darknet. Mirai was one of the famous IOT botnet with a DNS attack vector that made a major impact on a well-known DNS provider back in 2016. From than to now, numerous Mirai variants were created and many IOT botnets too. Most of these DNS DDoS tools have one main vector in common – the random subdomain flood nicked by Mirai as the DNS water torture. This attack vector is highly popular among attackers and can cause significant slowdown or even outage to unprotected DNS servers.
Mirai variants, offered as packages by scale
In DNS water torture the attacker sends many DNS queries with random prefixes (or subdomains) of the target domain, to make sure they reach the target authoritative server. Using a random prefix, the attacker ensures that the cache DNS forwards the query to the authoritative name server.
If we consider mydomain.com as the target domain, then the attack queries can look like – rThnBzl.mydomain.com, tngkoK8nbdms.mydomain.com, or human-readable prefixes that do not exist on authoritative name server. [2]
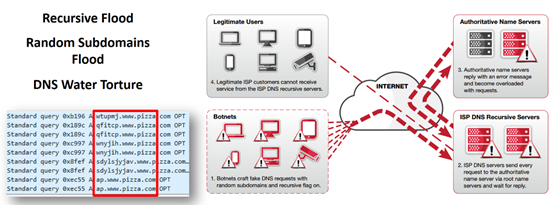
Graphical example for DNS water torture attack
Step 3: Scale
To make an impact, the attacker needs scale. So, his next step would be to take over a botnet or rent one. Nowadays, attackers, with the proper funding, can hire or purchase botnets in the darknet and achieve scale easily.
Thanks to the prosperity of IOT devices, botnets are made available on the darknet and keep growing daily. The IOT devices have real source IP and are easy to take over due to basic security and default passwords. In addition, IOT devices support various protocols allowing attackers to launch advanced attack vectors including DNS.
We witness DNS attacks originating from real source IPs, meaning attackers are most likely using IOT botnets, without the need for IP spoofing. IP spoofing can be dropped by ISPs, so by using real IP botnets attackers can bypass this security control at ISP level and successfully launch the DNS attack.
Step 4: Anonymization
Attackers typically hide their identity using anonymizers and TOR, for communicating and operating their botnet. Once the attack is launched, traffic originates from the botnet, without any link to the original identity of the attacker. The attacker can use IP spoofing to communicate with the botnet or query the target DNS server directly. Another option is to leverage the DNS hierarchy to hide the origin of attack queries. The botnet sends the attack queries through open DNS resolvers that forward them to the target authoritative server. Every query appears legitimate, coming from a legitimate DNS resolver and the challenge is to distinguish between good and bad queries to protect the DNS service.
Step 5: Launch!
Once the attacker controls a botnet, and has the DNS vector ready to run, the last part is to hit START and issue a command to the botnet. This step will be triggered according to the attacker's agenda – it can be hacktivism, financial, or political. With DDoS, attackers often combine ransom threat along with the DDoS attack.
How To Protect Your DNS Infrastructure
Now that you have a better understanding of how a DNS DDoS attack looks like, you can optimize our DNS protection. Here are important guidelines:
Perimeter DNS protection: A strong DNS server is important but insufficient to protect from DNS DDoS due to its network location. A DNS DDoS can risk your entire infrastructure prior to reaching the DNS server.
Complete Protection: Attackers can use one DNS vector or multiple, you should prefer a security solution that is comprehensive, covering various types of DNS vectors, including zero-day DNS water torture attacks.
Adaptive Mitigation: Attackers can use spoofing, real IP botnets, or open DNS resolvers. You need to make sure your protection is adaptive and agnostic to attack sources.
Zero impact on legitimate traffic: Attackers try to craft queries that appear legitimate. You should prefer a security solution that can automatically and accurately distinguish between attack and legitimate queries under attack to avoid impact to legitimate traffic.
Early Protection: DNS DDoS can cause degradation to the DNS service and even outage. You should prefer solutions that protect the DNS service without the need to inspect the DNS server's responses. Waiting for the server's responses for security might be too late, putting at risk the DNS service availability and operation.
Click HERE to get more information about Radware’s DDoS Protection solutions and how we keep organizations secure and safe from cyberattacks. If you’d like to speak with a Radware cybersecurity professional and better understand how to protect your applications and infrastructure, reach out to us HERE. We’d love to hear from you.
References
[1] Escalating Trends in DNS Flood Attacks
[2] What is DNS Flood Attack (DNS Flooding)