In the dynamic landscape of cybersecurity, the ability to quickly identify, understand, and respond to threats cannot be overstated. As the volume and complexity of cyber threats continue to increase, the role of effective data visualization in cybersecurity dashboards becomes crucial. These dashboards serve as the cockpit dashboard interface, empowering users to understand the data and make informed decisions rapidly.
The Importance of Real-time Threat Visualization
Cybersecurity professionals operate in an environment where split-second decisions can mitigate or escalate potential threats. However, navigating through a multitude of security data, such as intrusion attempts, malware outbreaks, or anomalous activities, can be overwhelming without the aid of well-designed visualization tools.
Enabling Rapid Decision-Making
A well-crafted cybersecurity dashboard should not just display data but should transform it into actionable insights. It must convert complex information into easily digestible visual representations, enabling users to understand the state of their systems swiftly.
Effective Data Visualization Techniques
Clarity and Simplicity
The most important rule of effective data visualization is clarity. A cluttered or overly complex interface can confuse rather than assist decision-making. Clear and simple visuals that convey the most critical information at a glance are invaluable.
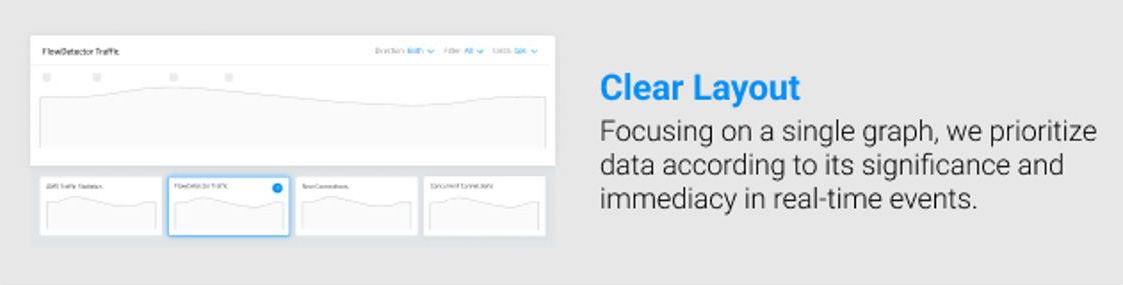
Hierarchical Information Display
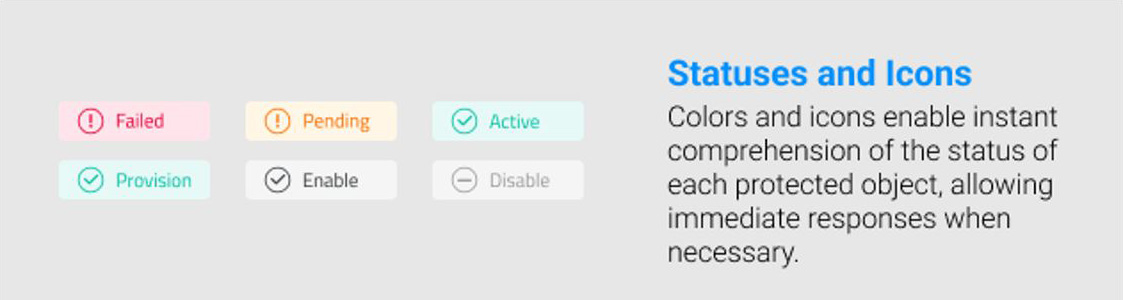
Prioritizing information based on its relevance and urgency is crucial. Using visual hierarchies, such as color-coded alerts or size-based emphasis, guides users to focus on the most critical threats first.
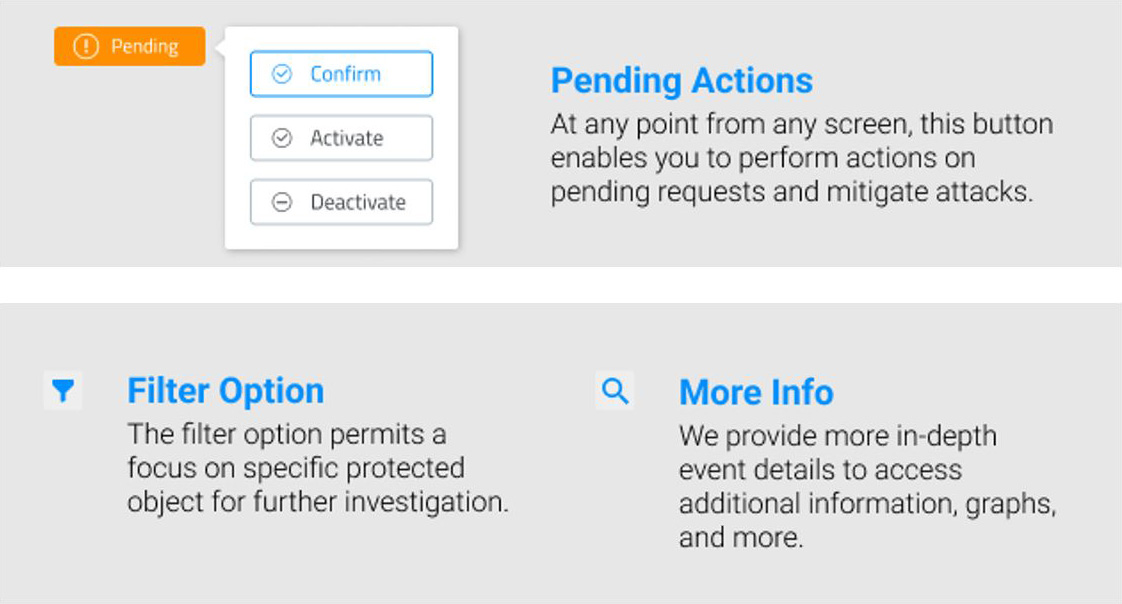
Interactive Elements for Deeper Insights
Offering interactive elements within the dashboard allows users to investigate deeper when necessary. For instance, clickable elements or drill-down features enable a more in-depth view of specific threats without overwhelming the initial dashboard view.
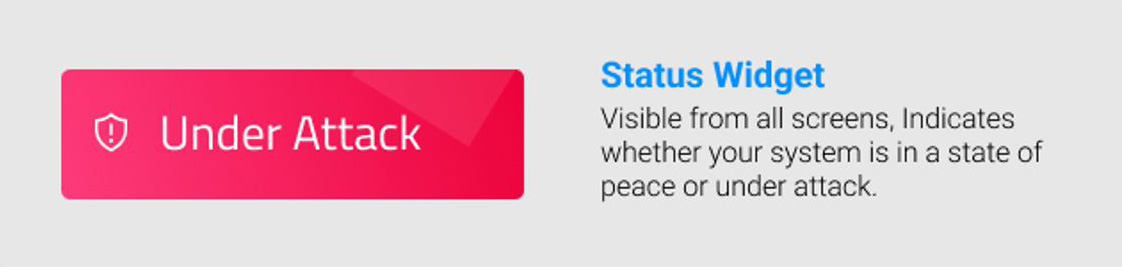
Real-time Updates and Alerts
Incorporating real-time data updates and instantaneous alerts ensures that cybersecurity professionals are equipped with the most current information, enabling proactive responses to emerging threats.
Understanding User Needs
Designing a cybersecurity dashboard begins with understanding the users' needs, their workflows, and the contexts in which they operate. A user-centric approach ensures that the dashboard aligns with their use, making it more intuitive and efficient.
Conclusion
In an era defined by persistent cyber threats, the design of cybersecurity dashboards plays an important role. Real-time threat visualization isn't just about presenting data; it's about empowering users with the tools to make split-second decisions effectively. By employing clear, intuitive, and user-centric design principles, cybersecurity dashboards become a major advantage in the ongoing battle against evolving cyber threats.
Ultimately, the success of a cybersecurity dashboard lies in its ability to seamlessly merge powerful data insights with an intuitive user experience, empowering the users to stay one step ahead.
To learn more about Radware's Cyber Controller, go to the Radware website, register and search for "Cyber Controller"