Gate Keepers: How to use Geolocation for Security
Introduction
Distributed Denial of Service (DDoS) attacks continue to be a significant threat in the cybersecurity landscape. These attacks involve overwhelming a target system or network with a flood of traffic, rendering it unavailable to users. When it comes to DDoS trends, attackers are becoming more sophisticated, employing various techniques to amplify the impact of their attacks and evade traditional mitigation strategies.
DDoS attacks have been using botnets since the beginning of time. With the prosperity of IOT devices, creating botnets became even easier for attackers that in the past had to overcome patched PC security. These botnets attain a considerable scale, reaching up to millions of bots. These botnets await central management commands to launch attacks, and being IOT these bots typically own a real, sustainable source IP and geolocation.
Figure 1 shows the top attacking countries in H1 2023 from Radware 2023 H1 Global Threat Analysis Report.
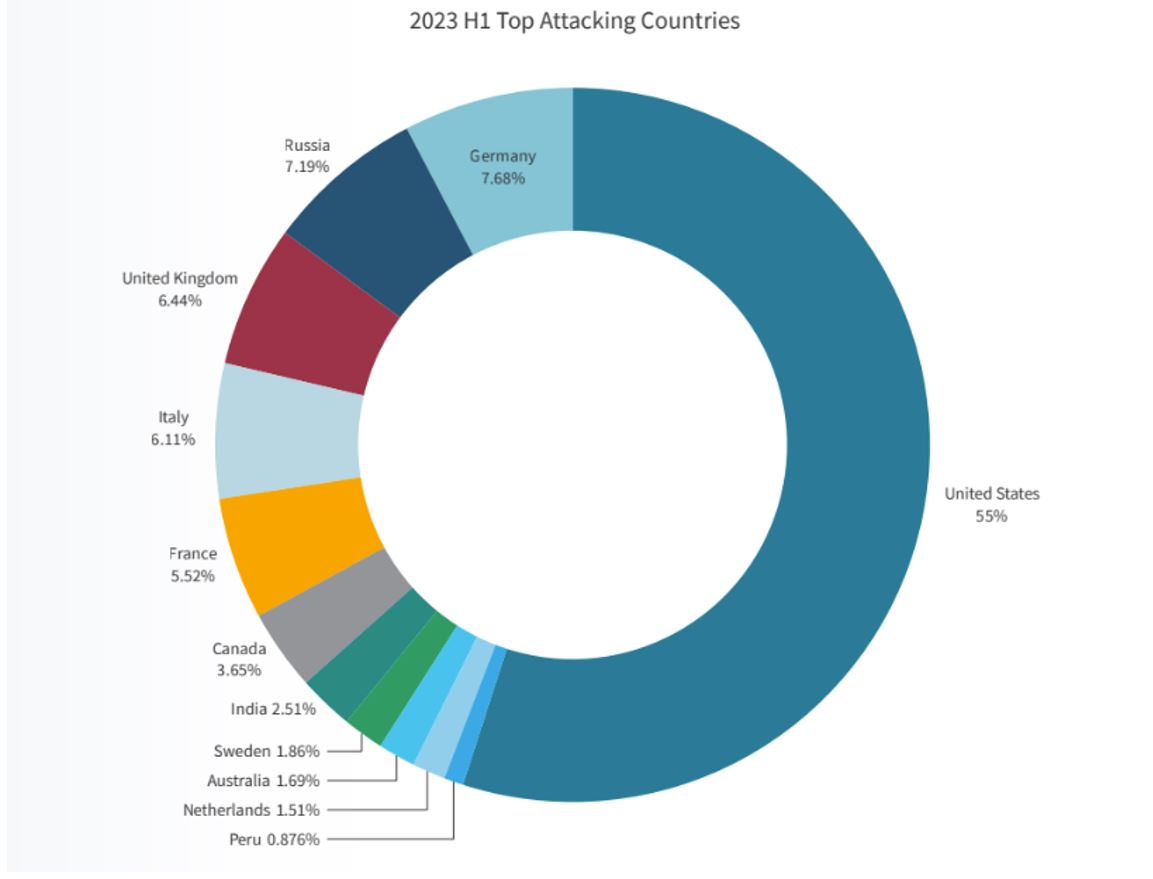
FIGURE 1: Top Attacking Countries
What is Geolocation Protection?
Organizations may implement access control policies that restrict or allow access to certain resources based on the geographic location of users or devices. For example, they might limit access to sensitive systems only to users connecting from specific geographic regions or countries. Organizations can use IP geolocation services to identify the location of users or devices connecting to their networks and enforce security policies based on this information. Geolocation-based controls enhance the overall security posture by thwarting malicious traffic before it reaches critical resources. This proactive approach not only safeguards against DDoS attacks but also contributes to the resilience and availability of online services. It forms part of a comprehensive cybersecurity strategy, emphasizing the importance of layered defenses to effectively mitigate the diverse range of threats organizations may face in the digital landscape.
We observe attacks originating from different sources and various geographical locations, showcasing a high level of distribution rather than being concentrated in a single geography each time. The IP addresses involved exhibit stability rather than volatility, indicating that attackers construct botnets using authentic IP devices, such as IoT devices. As a result, we can identify and profile the geographical locations associated with these real IPs.
Geolocation protection is a crucial component in defending against distributed denial-of-service (DDoS) attacks, which can have severe consequences for online services. By implementing geolocation filtering, organizations can strategically block or limit traffic from regions frequently associated with DDoS attacks, thus reducing the impact on their infrastructure.
Business cases for proactive geolocation policy:
- Organizations having localized traffic only, can safeguard their environment by dropping traffic from other geolocations.
- Organizations which follow regulations (primarily finance regulations) which restrict traffic from specific geolocations.
- Organizations that track and experience attacks from specific geolocations, can proactively deny traffic from those geolocations.
Geolocation can also be enforced reactively, that is under attack. When the SOC/NOC of the organization identifies an attack, they can use geolocation as part of the attack mitigation enforcement.
Although Geolocation protection seems to be the ideal solution to prevent unauthorized access or attacks from specific regions, it shall be used with caution, especially when applied reactively, under attack. In some cases, especially with DDoS attacks, source IPs may be spoofed, so before you apply geolocation into your security policy, make sure the focus on the proactive side, and apply geolocation protection reactively after verifying that the attack sources are non-spoofed.
How to use Geolocation for Security
Implementing geolocation protection as part of your cybersecurity strategy involves careful planning and consideration of best practices.
First and foremost, make sure your Geolocation service is up to date with the latest IP to Geolocation database, to ensure that your security policy will be accurate.
- In case the organization is global, and may receive traffic from all geolocations, the way to apply geolocation protection is different.
- For practice geolocation policy, you should track, and monitor traffic received to your services from different geolocations. If the top geolocations are known and expected, you can apply your security policy on other geolocations. Specifically, define rate-thresholds on non-common geolocations, to apply mitigation in case the geolocation exceeds a certain threshold.
- For reactive protection, under attack, you can temporarily deny attack geolocations that are non-common and add more rate-thresholds to control the attack traffic and combine with additional and more advanced DDoS protections.
Monitor your traffic and define Geolocation Policy:
Define Proactive Policy:
- Understand which regions or countries are allowed or denied access to your resources.
- There are organizations, as detailed in business cases above, that expect only local traffic, or have regulations, can add proactive geolocation policy in advance and benefit from a stronger security policy.
- Thanks to this proactive geolocation policy, such organizations can avoid DDoS attacks in the first place.
Combine with Other Security Measures:
Geolocation policy is most effective when used as part of a layered DDoS protection paradigm. You should combine it with other more advanced protections like behavioral protections to address sophisticated attacks and minimize risks of false positives.
Conclusions
Using Geolocation for security can be a strong proactive protection that can help eliminate risks for DDoS and other threats. There are specific cases where Geolocation can be a key protection and other more typical cases, where Geolocation protection is a layer within the DDoS layers of defense. The key is to understand your environment and needs and apply the best security policy for your organization.
To read more and see how Radware can help you with DDoS protection refer to Radware.com



