Introduction
When a global bank became the target of a 1 terabit per second DDoS attack, the stakes could not have been higher. Financial institutions operate in an environment where uptime is non-negotiable. A single minute of downtime can translate into millions in losses and irreparable damage to customer trust. Yet, in this case, the attack had zero impact. Services remained available, transactions continued, and customers never noticed a thing.
This is not luck. It is the result of a well-designed hybrid DDoS protection strategy that combines on-premises defenses with the scalability of cloud-based mitigation. Let’s take a closer look at what happened and why this approach is critical for resilience in today’s threat landscape.
The Attack: Scale and Complexity
Three days before the attack, traffic to the bank’s infrastructure began to rise dramatically, signaling the start of a coordinated campaign. When the full attack hit, it peaked at 1.2 terabit per second, a level that would overwhelm most traditional defenses. This was not a short-lived spike. The average traffic remained close to 1 Tbps for several consecutive days.

Figure 1: Traffic surge during the DDoS attack, showing incoming traffic peaking at over 1 Tbps and sustained high volumes over several days, with clean traffic remaining stable during mitigation.
This was not a simple flood of traffic. It involved multiple vectors, including volumetric attacks aimed at saturating bandwidth and application layer requests designed to exhaust server resources. Attackers leveraged botnets distributed across thousands of compromised devices, making the traffic appear legitimate and far more difficult to filter.
But just when they thought it was over, they were hit again and again for several days with massive peaks of similar scale.
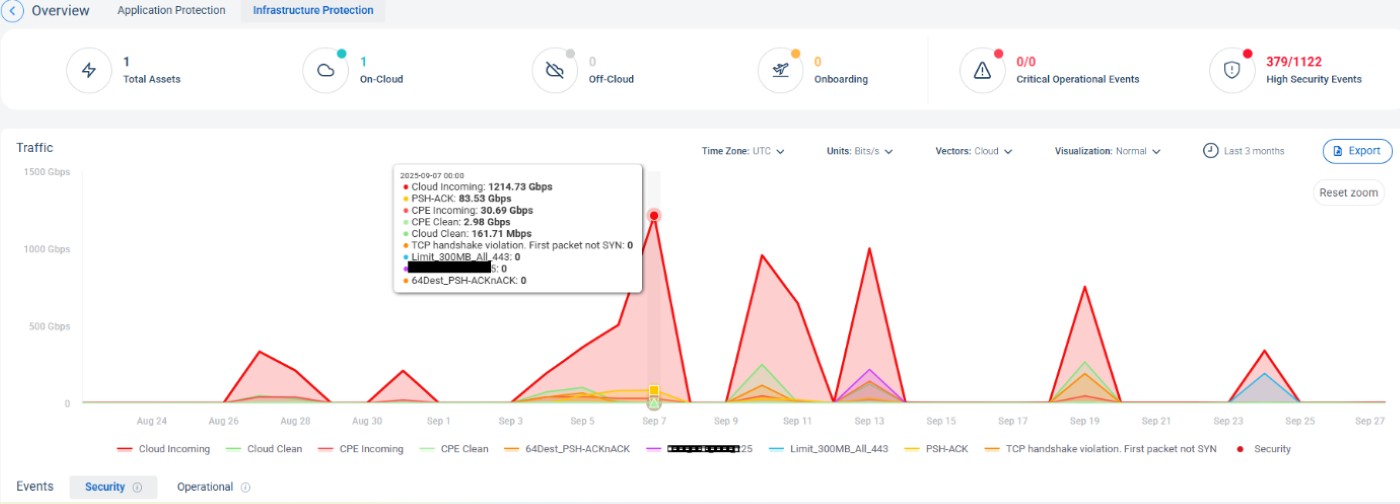
Figure 2: Detailed traffic view during the full attack, highlighting multiple spikes and protocol violations with incoming traffic exceeding 1.2 Tbps while clean traffic remained stable.
For many organizations, this type of attack would mean service disruption, delayed transactions, and frustrated customers. But this bank had prepared for exactly this scenario.
The Defense: Hybrid Protection Done Right
The bank’s strategy relied on two key components working in harmony:
1. On-Premises Mitigation
Local appliances handled the initial surge, filtering malicious traffic in the network and preventing immediate overload. This layer provided instant response and visibility.
2. Cloud-Based Scrubbing
As the attack escalated, traffic was seamlessly diverted to the always on cloud DDoS Protection service capable of absorbing massive volumes. This elastic capacity ensured that even at 1.2 Tbps, legitimate traffic flowed without interruption.
The transition between on-premises and cloud was automatic and transparent, eliminating delays that often occur when diverting traffic to the cloud.
Why Hybrid Matters
Purely on-premises solutions cannot scale to absorb attacks of this magnitude. Hybrid protection combines the best of both worlds: immediate local defense and unlimited cloud capacity.
This incident proves that resilience is not about hoping for the best. It is about planning for the worst and building systems that adapt under pressure.
The Takeaway
DDoS attacks are growing in size and sophistication. A 1.2 Tbps attack is no longer theoretical—it is happening now. Organizations that depend on availability must rethink their approach. A strong DDoS protection solution is not optional. It is the foundation for uninterrupted service and customer trust in an era where downtime is unacceptable.
Learn more today