Since late 2023, a group calling itself "Keymous+" has been steadily ramping up its activity online, claiming responsibility for a wave of DDoS attacks across Europe, North Africa, the Middle East, and parts of Asia. With over 700 claimed attacks in 2025, their visibility on Telegram and X (formerly Twitter) has grown rapidly. However, a closer look raises more questions than answers about who they really are and what they want.
No Clear Agenda, No Clear Enemies
One of the most striking features of Keymous+ is the randomness of their targets. The group self-identifies as “North African hackers” and targets dozens of countries across multiple sectors. Government websites are a common target, but specific industries vary by region: telecom providers in France and India, financial platforms in Morocco and the UAE, education sites in Denmark, and manufacturing infrastructure in Israel.
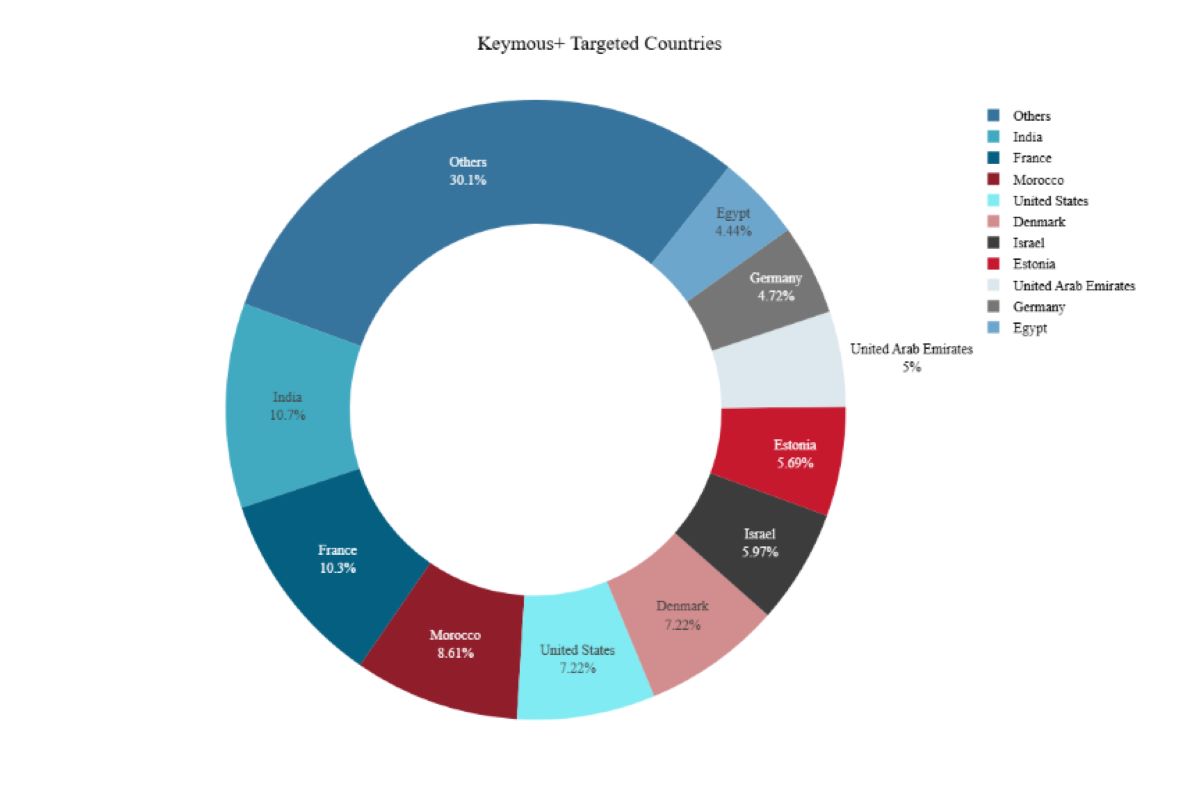
Figure 1: Top countries impacted by Keymous+ in 2025 (source: Radware)
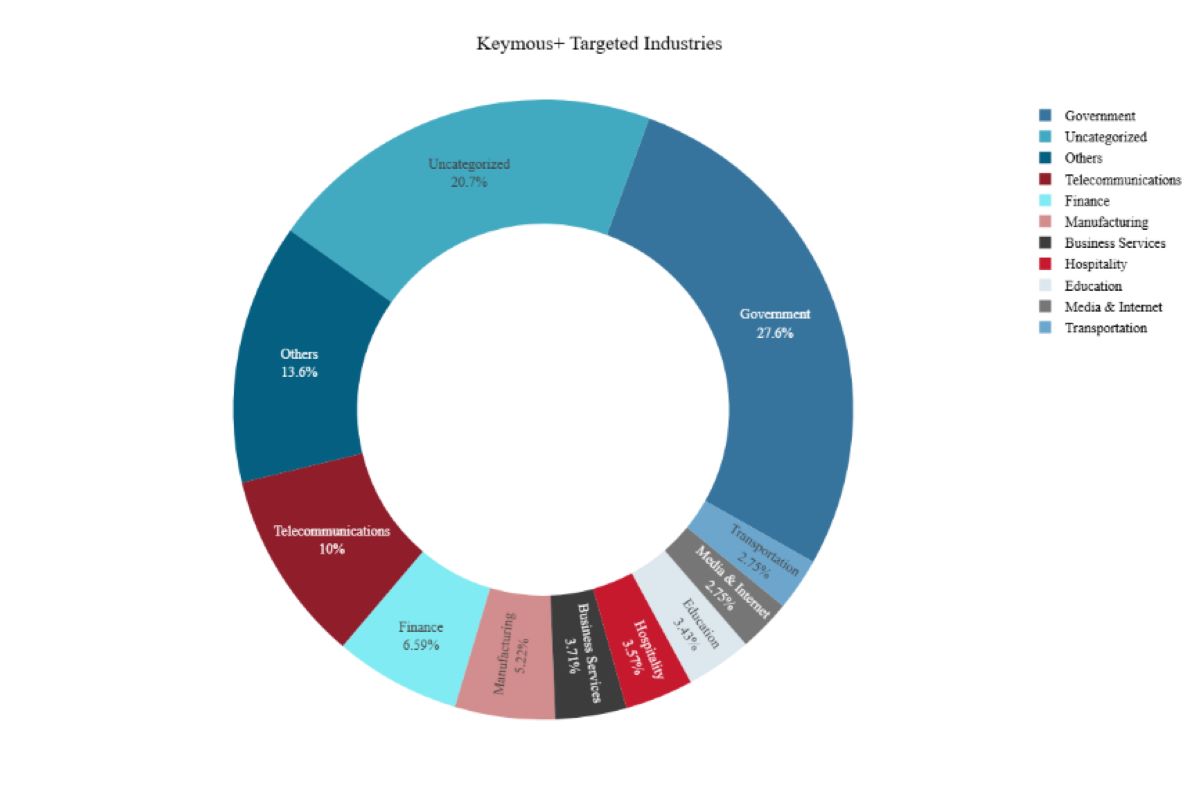
Figure 2: Top sectors targeted by Keymous+ in 2025 (source: Radware)
The group seems to strike wherever and whenever it's convenient. While they occasionally echo slogans like "Hack for Humanity" or align themselves with popular hacktivist operations like #OpIndia or #OpIsrael, there is no consistent ideological line.
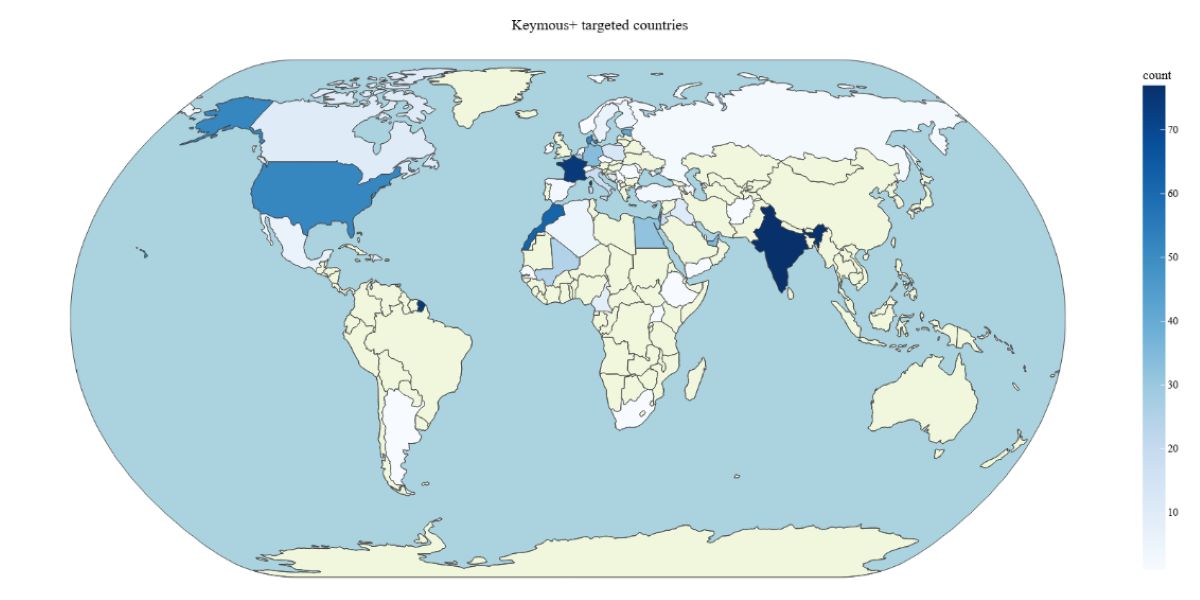
Figure 3: Map of countries targeted by Keymous+ in 2025 (source: Radware)
Growing Web of Alliances
Another element that defines Keymous+ activity is its increasing collaboration with other hacktivist entities. Some of these collaborations may also serve as marketing opportunities for shared infrastructure. The group often amplifies messages from allied actors and engages in joint operations such as "Red Eye Op," appearing alongside groups like NoName057(16), Mr Hamza, AnonSec, Rabbit Cyber Team, Hunter Killerz, Moroccan Dragons, and more.

Figure 4: Keymous+ alliances and coordinated operations demonstrating collaborations (source: X, Telegram)
These alliances serve both strategic and reputational goals: they allow Keymous+ to broaden their operational reach while reinforcing their image as a central player within the hacktivist ecosystem. This networked approach is becoming a signature trait of modern hacktivism—one where visibility and affiliation may matter as much as impact.
Organizational Claims and Activity
Keymous+ describes itself as having a dual-team structure: an "Alpha Team" responsible for breaches and leaks (currently inactive) and a "Beta Team" focused on DDoS operations.
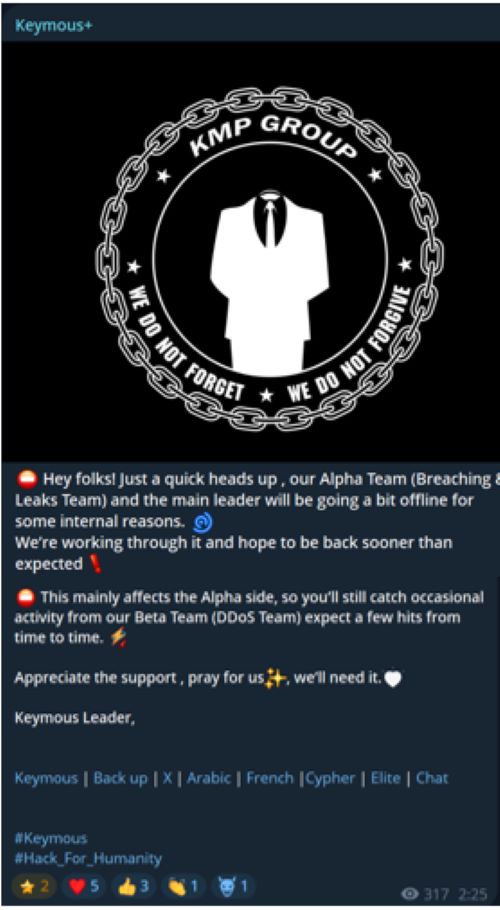
Figure 5: Alpha Team and Beta Team roles (source: keymous+ telegram channel, June 22, 2025)
While there’s limited detail beyond the basic Alpha/Beta distinction, such descriptions are consistent with how other hacktivist groups attempt to portray coordination and professionalism. Beta Team, at least, has been visibly active throughout 2025, claiming hundreds of attacks supported by Check-Host.net evidence. Though these do not always indicate the full extent or impact of disruptions, the persistent volume suggests a deliberate and ongoing intent.
Recent evidence also suggests that Keymous+ may operate—or be closely affiliated with—a commercial DDoS-for-hire service known as EliteStress. While the group does not publicly admit to ownership, a tweet shows a Keymous+ representative boasting about their role in a stressor platform, implying insider access or operational control.
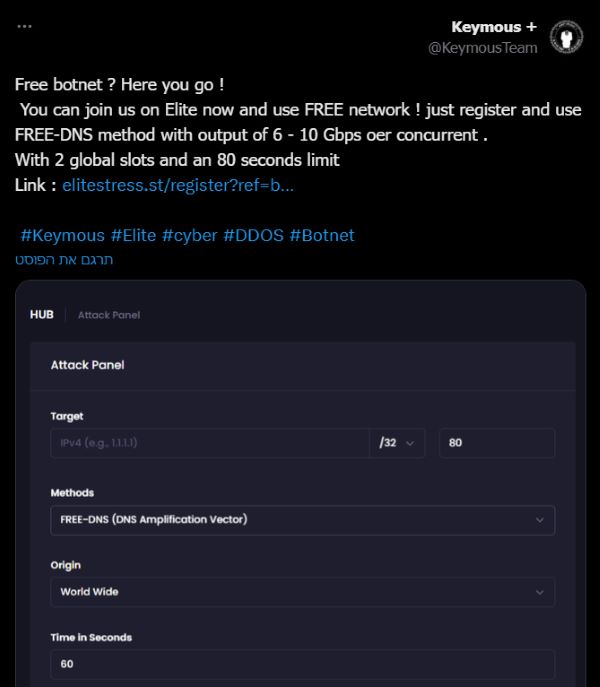
Figure 6: Keymous+ tweet inviting users to “join us” on EliteStress (source: X, formally Twitter)
This raises the possibility that the Beta Team functions not only as an attack unit but as a semi-commercial infrastructure provider offering DDoS capabilities for sale.
Marketing Under the Hood
What makes Keymous+ stand out is not just the volume of claimed attacks, but also the tone. Many of their posts emphasize concepts like "power", "uptime", and "stable performance", frequently referencing bots, tools, and links to external platforms. Telegram handles like "Join_Elite" appear regularly, and announcements about discounted services, active users, and support bots give the impression of a semi-professional operation. For a time, these clues only hinted at possible commercialization. However, the tweet in Figure 6 suggests that the group may be the owner of a DDoS-for-hire service: EliteStress.
EliteStress and the Commercial DDoS Model
EliteStress is a dedicated stressor website that offers DDoS attacks as a service, with pricing tiers ranging from €5 per day to €600 per month.
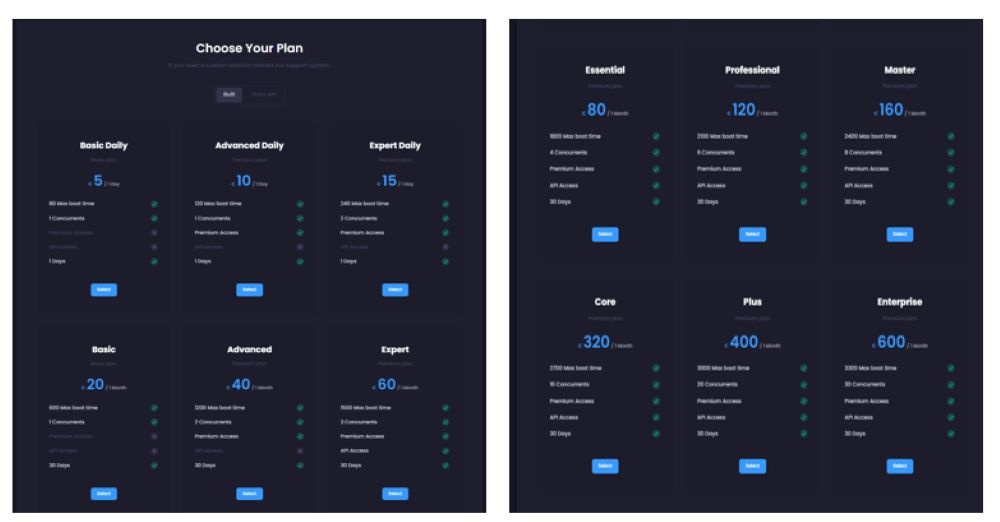
Figure 7: Pricing for DDoS subscriptions (source: EliteStress)
The platform includes a wide selection of vectors such as DNS amplification, UDP floods, HTTP/2 attacks, and spoofed SSH or ICMP traffic. Users can launch attacks by selecting a target IP, choosing a vector, and setting the attack duration.
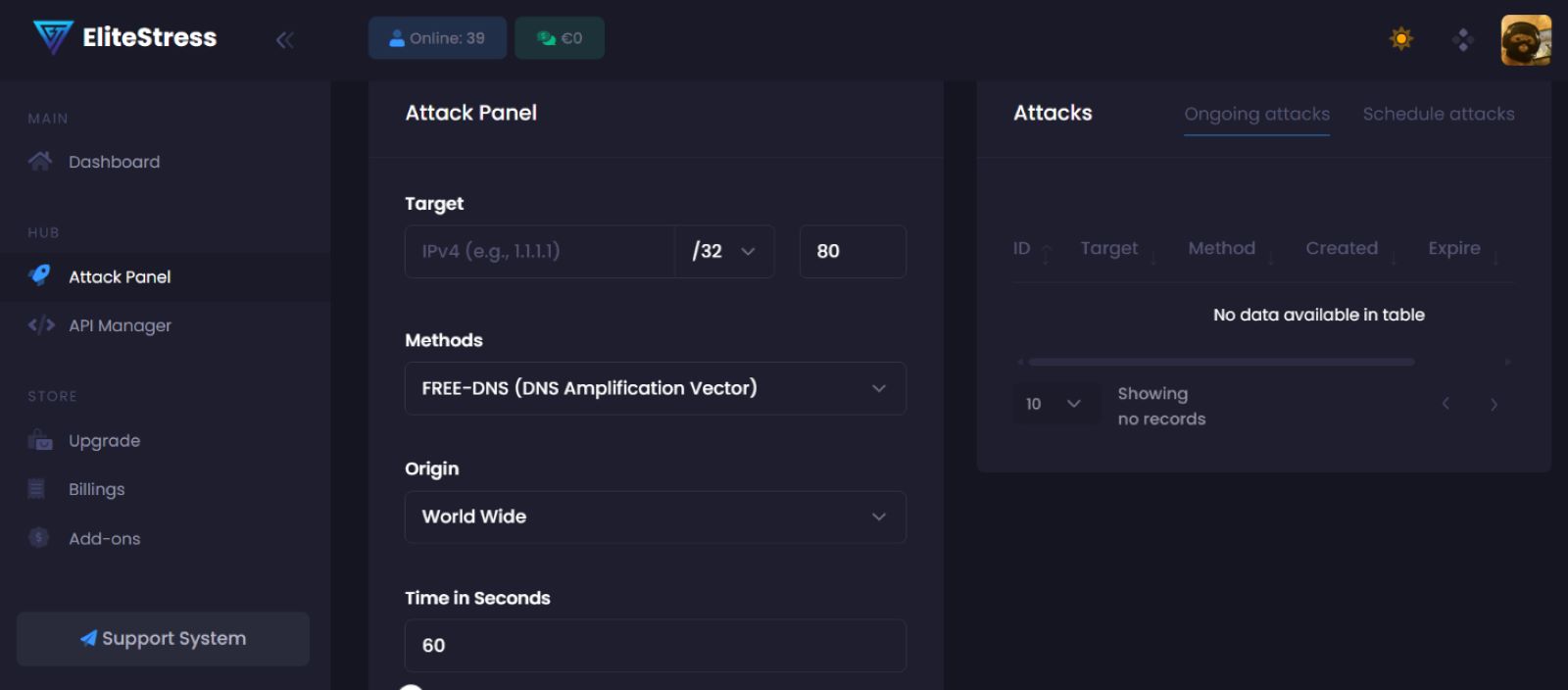
Figure 8: EliteStress' attack panel (source: EliteStress)
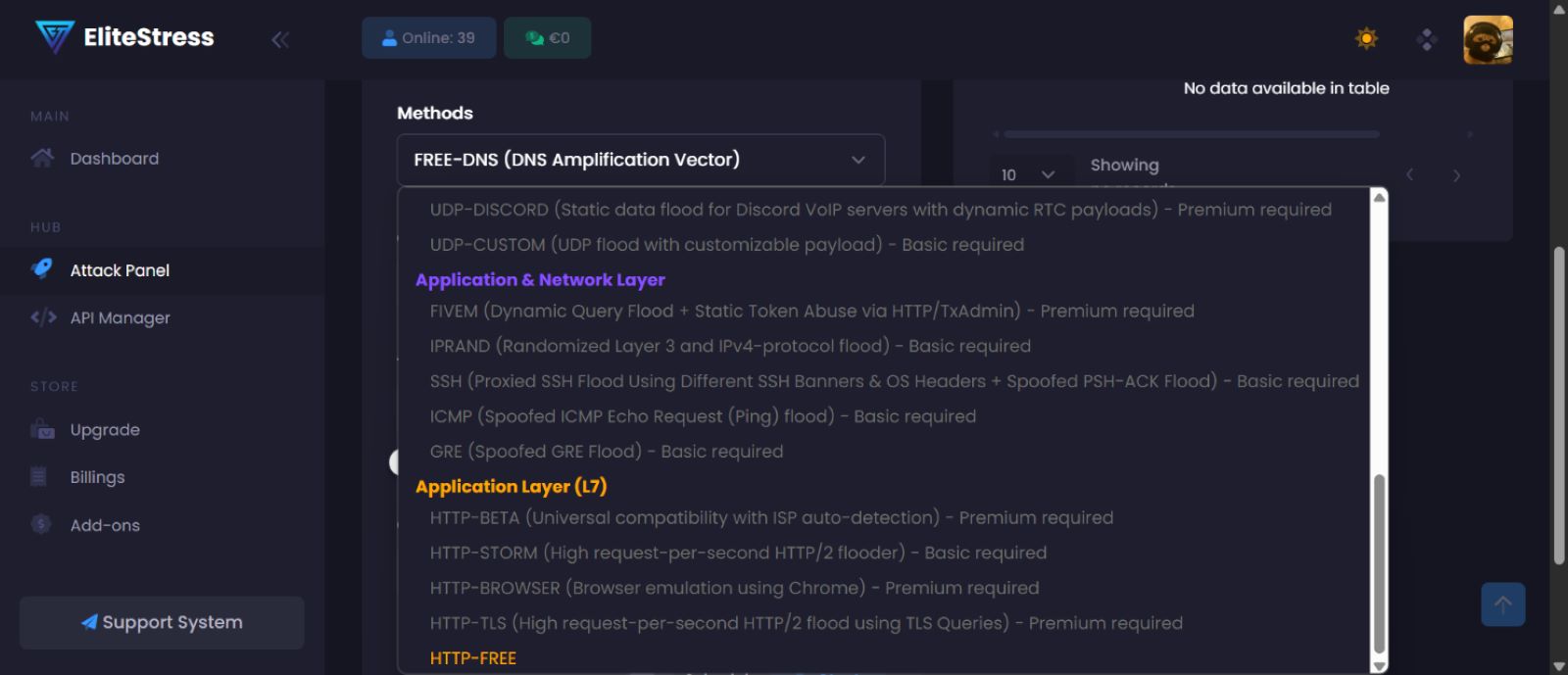
Figure 9: EliteStress' attack methods (source: EliteStress)
While many such services exist on the darknet, EliteStress is noteworthy for its sleek interface and integration with Telegram bots—a feature often promoted in Keymous+ announcements.
Conclusion
Keymous+ presents itself as a politically motivated hacktivist collective, but recent indicators suggest it could be operating as—or closely tied to—a commercial DDoS-for-hire service. Their branding, collaborations, and tone shifted from ideological motives toward a more calculated strategy to build visibility, credibility, and possibly revenue. While their true structure remains opaque, the line between hacktivism and profit-driven operations appears increasingly blurred. Whether Keymous+ matures into a more structured threat actor or dissolves like many of its predecessors, its current trajectory reflects the evolving face of modern cyber-activists: noisy, performative, and possibly for sale.