It didn’t take long for a big name celebrity to be compromised in one of the recent data dumps due to password reuse. I never thought it would be the man that runs the biggest online social network in the world. Mark Zuckerberg had his personal accounts compromised via the LinkedIn leak that was sold on the Darknet marketplace, The Real Deal, by a vendor named Peace of Mind.
Mark Zuckerberg’s information was found in the LinkedIn leak by a group of hackers from Saudi Arabia called OurMine. To make things worse, Zuckerberg’s password was not only weak but it was also reused across a number of platforms. In the end, Mr. Zuckerberg had his Twitter and Pinterest accounts compromised. The password in question was ‘dadada’. Ouch. You would have assumed that someone like Mark Zuckerberg would have been a little more careful when it came to securing his personal accounts. But have no fear Facebook users, even Facebook doesn’t find ‘dadada’ as an acceptable password.
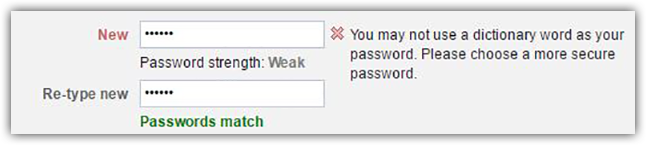
Considering the number of leaks that have occurred over the last few weeks, I figured this would be a good time to revisit password hygiene.
First, when you are creating a new account, try not to use the same username and password over and over again. This is a bad habit. If you use a separate username and password for each account, you will dramatically reduce your risk of having multiple accounts hijacked at once due to credential reuse. Another important thing to consider when creating a secure password is where you will store it. It’s difficult to remember multiple usernames and passwords, so I would suggest using a password manager like 1Password or LastPass to manage all of your accounts. I would also recommend that you change these passwords every 60-90 days.
[You might also like: Fraud on the Darknet: How to Own Over 1 Million Usernames and Passwords]
While browsing, make sure the site is encrypted and look for “HTTPS” before entering your information. Never let your browser store your information. Attackers can use tools like ChromePass and WebBroswerPassView to extract stored data and access your accounts. If your site offers two step authentication (2FA), I suggest that you enable this feature. For a list of services that offer 2FA visit: https://twofactorauth.org/
Below are a few general guidelines on how to create a secure password. When creating one, aim for a minimum password length of 14 characters.
Passwords should contain all of the following:
• lower case letters (i.e. a-z)
• upper case letters (i.e. A-Z)
• numbers (i.e. 0-9)
• special characters (e.g. )(*&^%$#@!)
Do not:
• use personal information
• use common words found in a dictionary
• use repeating characters
• use default passwords
Exercise caution when using Open Authorization, OAuth, for application logins. Some services require you to log in to their service with a Facebook account, like Tinder, but other services like Feedly give you an option. When given the option, avoid the OAuth login to prevent cross-contamination on multiple accounts.
One of the common arguments I hear from users when I recommend that they change their password habits is their accounts do not contain anything personal, like bank statements or account numbers. For the most part they are correct, but to a hacker there is more to harvest. For example, under Twitter settings you can find the IP login history under the tab “Your Twitter Data”. This information can be leveraged to discover more information about your location. If you have your cell phone number attached to the account, they can also see this and use it against you. Every data point counts for a hacker, and the idea is to prevent them from gathering information about you. You should practice secure password hygiene to prevent the attacker from pivoting to another account.

Download Radware's DDoS Handbook to get expert advice, actionable tools and tips to help detect and stop DDoS attacks.
Download Now