Recently a company in the DDoS protection space published an article about how hybrid mitigation models are ineffective against large HTTP POST attacks. While we respect all of our industry colleagues and support their contributions to the space as a whole, I wanted to review the case study and offer a different perspective.
The hybrid mitigation model uses an appliance at the customer premise and cloud-based solutions for volumetric attacks that exceed the local internet capacity (or capacity of the local mitigation appliance).
In the article in question, the author argued that premise-based solutions are only for application-layer attacks and that cloud-based solutions are used for volumetric network-layer attacks. The article seemed to infer that a premise-based device can’t withstand a volumetric attack, and that there was no place for premise and cloud-based solutions to work together.
The attack mentioned can be a challenging one if you’re not prepared, but Radware has had a solution to it for years.
The Attack
The attack mentioned was an HTTP POST attack that was close to 10 Gbps in throughput and a little more than 150k requests per second from nearly 3,000 IP addresses. By including large files in the POST, the attack achieved a moderate volumetric attribute in an application layer attack. There are several factors that make this attack interesting. As the author mentions, a traditional Web Application Firewall (WAF) environment might need to permit and establish the connections before taking an action. Add this with several thousand flows and source IPs, and you might easily overwhelm a single firewall or WAF. Finally, certainly not everyone has 10G or higher Internet links, so if you fill the capacity of your link, an HTTP attack like this would be nearly impossible for an upstream Internet provider to block on their routers (they, too, would need a mitigation solution like what we’re discussing).
Not All Hybrids Are the Same
An HTTP POST attack targets the web server and some surrounding infrastructure like WAF, firewall, etc. At Radware, we recommend a holistic approach to network security. We make great WAFs, but in this sort of attack, we’d recommend using a perimeter protection like our DefensePro platforms and combining that with our cloud mitigation if needed.
[You might also like: Cloud-Based or Provider-Managed DDoS Mitigation: Which is Right for Your Organization?]
DefensePro has the ability to detect the anomalous traffic and begin to challenge it for legitimacy. There are several escalations for challenge, so if an attacker can pass the first challenge and the anomaly persists, DefensePro would issue more complex challenges as needed to determine legitimacy. By inspecting and blocking at the perimeter, you can remove the load and risk from your infrastructure and WAF.
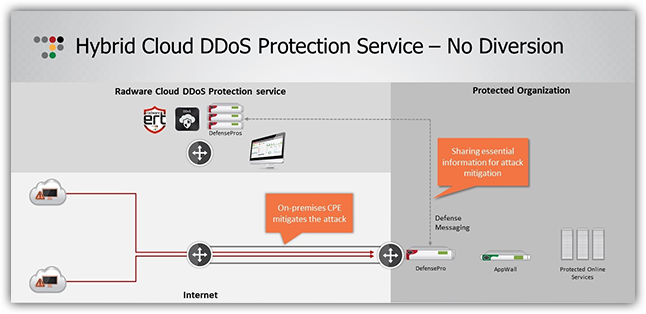
This is just one aspect of the solution, though. Radware is proud to be the only hybrid managed security provider who uses the same equipment on premise as we do in our clouds while maintaining them ourselves. We use our own DefensePro and AppWall appliances in our cloud nodes, so if customers need to divert to the cloud, the move is easy.
By owning the cloud mitigation nodes, we have full control and transference from premise to the cloud. What’s more is that we can signal attack and peacetime attributes from the premise to the cloud so that there is no learning needed in the cloud, allowing us to begin accurate mitigation instantly.
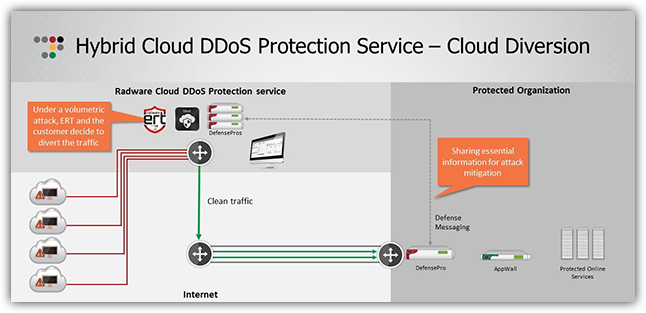
This model also enhances the end user’s experience because cloud diversion (and thus added latency) doesn’t need to happen unless there is a threat to the local network. For example, if you have 2x10G uplinks to your colocation or internet provider and a DefensePro that can support this capacity, you may not want to divert this attack because you can certainly handle it locally.
If you did have smaller internet capacity, the hybrid model is still effective. By using a smaller DefensePro at the perimeter, you still have the advantage of knowing peacetime traffic profiles and can still signal the attack footprint to the Radware cloud. By doing so, you’re saving costs on unused internet capacity, infrastructure and port costs, and the size of the necessary mitigation equipment.
What About Intelligent Headless Browsers?
Many smart bots are aware of HTTP challenge techniques like redirects and JavaScript, which is why we’ve developed an escalation method in our challenge hierarchy. To date there are no known instances where a headless browser has defeated some of our more complex HTTP challenges, but we’re constantly enhancing the toolset to stay ahead of the threat.
[You might also like: Best Practices for Hybrid Cloud/On-Premise Attack Mitigation]
The Right Hybrid Model Is Exactly What You Need
Choosing a security partner can be difficult because there’s a lot of information to consider. At Radware, we listen to our customer’s needs and help design the best possible solution for them. Some of our customers are premise-only. Some are cloud-only and some are hybrid. Our goal is to be an innovative partner and build long-lasting relationships with our customers. As we all know, there’s not one single security strategy that fits every need. When evaluating your partner, remember that some of us see things differently than others and not all solutions are the same.
For more information on Radware’s hybrid solutions, check out the following video:

Download Radware's DDoS Handbook to get expert advice, actionable tools and tips to help detect and stop DDoS attacks.
Download Now