Over the past four years, communications service providers (CSPs) have taken measurable strides to migrate network functions and applications to the cloud. And while we are not there yet, it's clear that the cloud will drive the future of service innovation. However, in my view, the very definition of service innovation is also extended in the cloud environment.
A prime example in my mind is the expansion of managed services to a cloud managed services model which drives profound business and technical change. While this cloud managed services model continues to be defined in real time, it's readily apparent that cloud-based managed security services will play a prominent role.
In fact, they are already a key consideration for enterprise customers of all sizes who face increasing numbers of more advanced and sophisticated cyber threats such as Distributed Denial of Service (DDoS) attacks.
In response, progressive CSPs are positioning themselves as Managed Security Services Providers (MSSP) leveraging the cloud to deliver a suite of security services, including DDoS, to enterprises that strategically have come to the realization that the cadence of DDoS attacks requires them to partner with a CSP who has the skillset and budget reach to provide the most advanced threat mitigation services. In many respects, adopting this stance and ultimately trusting a CSP for security enforcement represents a logical extension of existing models that enterprises currently utilize with CSPs for network connectivity and specialized enterprise services.

Is the MSSP model monetizable?
Even though there is pent-up demand for MSSP services, like any cloud deployment business case, the demand must be validated and quantified based on revenue potential vs. offsetting capex and opex costs. In this respect, in theory, traditional engineering economic modeling benchmarks such as Net Present Value (NPV) continue to apply, even though the outputs differ considerably since they reflect the transition to a software-driven model.
As a result, it's vital that CSPs fully understand the business fundamentals before committing to becoming MSSP. Stated another way, potential MSSPs really must conduct due diligence to understand the service-side fundamentals in a DDoS context.
[You might also like: Enterprises are asking for help to protect their data. Here’s the answer service providers should provide.]
In order to answer this vital question, Heavy Reading recently collaborated with Radware to create an MSSP model. The model adopted a bottom-up build methodology incorporating realistic monetization assumptions related to capex and opex, including software licensing and revenue streams.
Since revenue streams can vary based on enterprise size and scope of DDoS services delivered, we created two DDoS service models to reflect different pricing attributes. The first service model, which we referred to as the On-Demand model, was targeted for small to midsized enterprises, while the Always-On model was designed for larger enterprises. The main difference between the two is that in the On-Demand model, selected data streams are monitored out of path, rather than monitoring every data flow in real time, which is the essence of the Always-On model.
Based on the modeling assumptions, including revenue streams, we calculated based on known commercial pricing models. We confirmed the MSSP model can deliver strong financial returns. For example, as shown in the tables below, after five years the On-Demand model generated a net cash position of $317.5 million, while the Always-On model generated a net cash position of $348 million. Also worth noting is that in both models, by the end of the first year, the original costs of capex necessary for initial launch had been recovered.
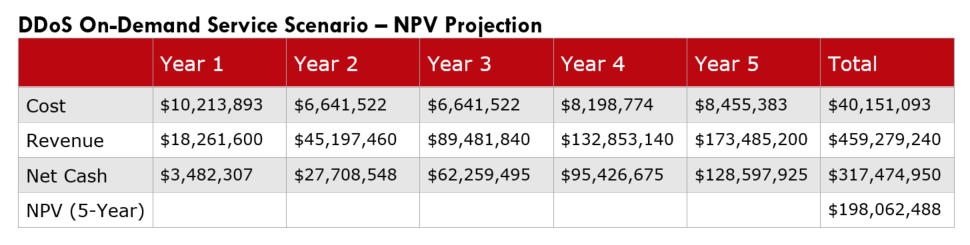
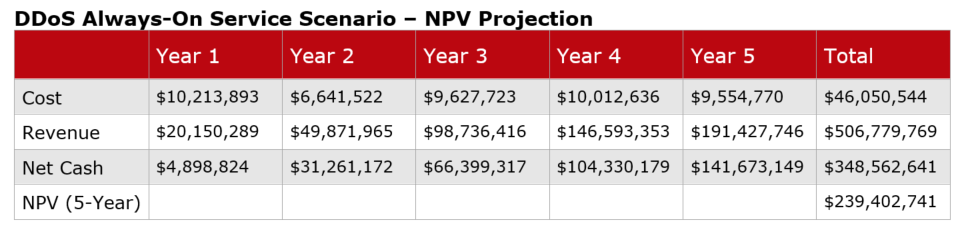
In summary, based on what we consider conservative modeling estimates, it's clear that for early MSSP adopters the service side of DDoS services already represents a strong and sustainable business opportunity. And looking forward, given the aggressive growth of threat vectors, it's very likely that MSSP will be an even greater business opportunity as the scope of threat complexities are amplified and more enterprises adopt a managed service model.

Read "Cyber Economics: Validating DDoS Managed Service Delivery Models" to learn more.
Download Now