As the 2018 Winter Olympics in PyeongChang approaches, Radware’s Emergency Response Team (ERT) and Threat Research Center turn their attention to the large crowds and target-rich environments created by high-profile events once again. With over 1.07 million tickets available for 102 events over 16 days, spread out across two clusters and containing a total of 12 venues, the crowds at the 2018 Winter Olympics will bring a large demand for connectivity. This enormous demand for connectivity and technology at the Winter Olympics will also pose a security risk for Olympic organizers, partners, sponsors, suppliers, service providers, athletes and attendees.
There are only a few sporting events in the world as large as the Olympics. With millions of attendees and global viewers the Olympics generate a lot of excitement and demand from the fans. Beyond just the games itself, the variety of multimedia technologies available for streaming content, drones, augmented reality and wearables provide viewers and attendees with a more immersive and interactive experiences than ever before.

Smart stadiums and venues today now offer network connectivity for fans via Wi-Fi, Bluetooth and a number of other digital services. But reliable Wi-Fi is normally an issue at large scale events. Users demand to experience the games in new ways and share content in real-time. Imagine the stress 50,000 attendees can put on the network of one venue while everyone simultaneously tries to tweet, post, snap and stream every moment of the games in real time. Now multiply this by 12 venues and you begin to understand the magnitude of the challenges of providing connectivity to the Olympic games in PyeongChang. This kind of demand for instant and on-demand connectivity will stretch even the best networks and often require massive upgrades ahead of the event.
Because of the large demand for connectivity expected from the games, Korea Telecom. in partnership with Intel, will be delivering the first broad-scale 5G network for the games and enable attendees to engage in a variety of experiences at the Winter Olympics. In addition to this, NBC is preparing to live-stream 1,800 hours of the Winter Olympics this month for those who are not able to attend. Four years ago at the Winter Olympics in Sochi, NBC was able to broadcast 1,000 hours of live content.
[You might also like: The Evolution of the Dark Web]
Possible Threats
Along with the demand for technology and connectivity, the games are also becoming more reliant on critical applications to help provide this experience to those onsite and around the world. Technology can provide a more immersive and rewarding experience for fans, but also create problems and security risks for those managing the event networks. Over the last decade there have been a number of cyber-security related events aimed at the Olympics. At the 2012 Summer Olympics in London, hackers launched persistent and automated attacks every day during the games. During the 2016 games at the Summer Olympics in Rio, attackers launched persistent DDoS attacks that reached peaks over 500Gbps.
Typically, attackers begin probing and launching attacks against the Olympics several months ahead of the games. This year several organizations associated with the games have already been targeted by spear phishing attacks. A phishing attack is a digital attempt to obtain sensitive information from a victim by using a malicious email or website. The attacker solicits personal information by posing as a trustworthy organization or the company itself. These attempts are either sent out to everyone in the company or designed to specifically target key associates. Once an associate falls victim to these the hacker will then have the sensitive information required to gain access to certain systems.
The potential risk steadily increases as future games become even more connected. The 2018 Winter Olympics have the potential to be one of the more vulnerable sporting events and will provide cyber criminals with numerous opportunities to profit. The Winter Olympics also creates a great platform for hacktivists and cyber criminals to spread a message, make profit or simply create disruption.
Today, it is very easy for low-level threat actors to carry out large scale and disruptive attacks. Toolkits and attack services are widely available for purchase on the clear and darknet. At the 2018 Winter Olympics most cyber criminals and hacktivists will be focused on identity theft by spreading malicious payloads in a number of ways that are designed to harvest and steal personal information. Often times it’s the technologies designed to enhance the spectators’ experience like free Wi-Fi, Bluetooth and other digital services that are ultimately abused and exploited to harvest information from the attendees, athletes, journalists and broadcasters.
One of the biggest concerns about the Olympics this year is protecting the critical applications and networks that support the event. Broadcast networks, industrial control systems, operational networks and other related systems are all at risk. Hackers could try and disrupt the games inside the venues or through the live stream. Hacktivists and criminals will launch application attacks like SQL injections, password cracking, cookie poisoning, cross-site scripting, session hijacking and more in an attempt to steal Olympic and spectator data. Information on the attendees, sponsors, or athletes can be quickly monetized or publicly used. Criminals will also use fake applications and websites to target attendees.
The risk of your mobile device being hacked in an environment like this grows exponentially with more people that connect to the same network. It becomes ever more attractive for criminals due to the larger number of users. There is also a high risk for targeted attacks against high profile visitors and athletes at the 2018 Winter Olympics. Visitor devices could be easily targeted by cyber criminals at the games. Fake charging stations or compromised access points can quickly allow an attacker to gain access to a device. Once infected, devices can perform tasks like record audio and video, take photos, send text messages, open webpages, steal user data, delete files, launch denial-of-service attacks via HTTP floods, and perform web injections. In the event of targeting an athlete, competitive information such as their routine or their social media account could be hijacked.
[You might also like: Bad Packets 2017 – A Year in Review]
Providing spectators and athletes with connectivity is a double-edge sword. Connected venues can become a Bring Your Own Device (BYOD) nightmare for event management and wireless network operators. Open Wi-Fi networks also present one of the biggest attack vectors for network and malware-based attacks. Criminals know that visitors at the 2018 Winter Olympics will be reliant on such Wi-Fi access points, turning them into an easy target.
[caption id="attachment_7790" align="aligncenter" width="533"]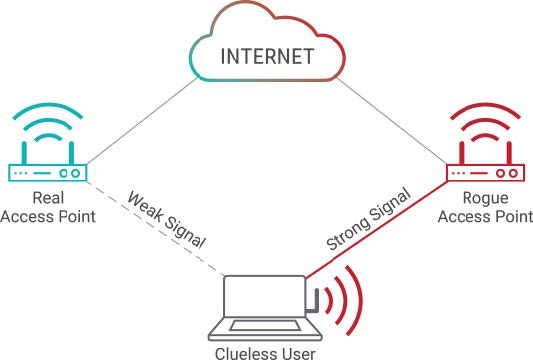 Source: Radware[/caption]
Source: Radware[/caption]
As part of their preparations, hacktivists and cyber criminals have likely already identified access points and their vulnerabilities across the Olympic venues. They will set up fake access points to intercept and manipulate their victims’ browsing and to steal passwords, credit cards, PII and other sensitive information. A common Man-in-the-Middle (MITM) tactic using malicious access points is to name a fake access point as the same name of a legitimate access point. Once a user is connected, malware can be injected onto their device or its traffic can be inspected. This year at the Winter Olympics I expect to see a number of compromised, insecure and vulnerable access points.
I also expect to see a number of criminals leveraging social media and email to spread their malicious domains designed to harvest personal information. Users are normally directed to these sites after falling victim to fake giveaways for tickets or promotional material on social media or via email. Criminals behind bad domains look to hijack the names of the cities, venues or event names to trick users via typo squatting into entering their credentials by spoofing the content of the original websites.
Attendees at the 2018 Winter Olympics should also be aware of other data mining attacks delivered via fake pop-ups or text messages. They should also be aware of physical attacks such as juice jacking, and ATM/ Point-of-Sale (PoS) skimmers. Criminals will be deploying skimmers on ATMs and PoS systems at the 2018 Winter Olympics. It allows hackers to record the ATM user information and later sell it for profit on the Darknet. The larger the crowd, the higher the number of potential victims, making the Olympic crowds a prime target for profit-motivated criminals.
Attendees at the 2018 Winter Olympics in PyeongChang should take these steps to keep their devices and information secure:
- Ensure your phone is updated with the latest operating system
- Disable Bluetooth when not in use
- Disable Wi-Fi when not in use
- Use the official event Wi-Fi when device is in use
- Always use a VPN when using Wi-Fi
- Have RFID shields to protect RFID cards
- Be careful when using ATMs and Point of Sale systems – Understand how to spot and avoid card skimmers gathering data
- Exercise caution when presented with pop-ups while browsing
- Avoid Olympic-related scams delivered via email
- Avoid promotional USBs
- Avoid public charging stations

Read "2017-2018 Global Application & Network Security Report" to learn more.
Download Now