Although security professionals have better visibility into what is happening on their networks when computing resources are managed on-premise, the benefits of a public cloud environment are compelling. As expected, enterprises continued to transition more applications and data to public cloud environments in 2019.

Organizations look to public cloud service providers for network infrastructures that enable more agile responses to customer needs and deliver high availability and network performance while reducing operational costs.
Why Multiple Public Clouds?
The next step in this migration is the concurrent use of multiple public cloud environments for a number of reasons:
- Cost optimization — Every public cloud service provider offers different services and pricing packages. Organizations have more negotiating power when they are not tied to only one service provider.
- Service redundancy — If all digital assets reside in one public cloud environment, there is too much risk for network downtime. Using multiple public cloud environments enables strategic planning for backup protection.
- Best-of-breed functionality — Each public cloud provider has its strengths and weaknesses when it comes to certain capabilities such as computing power, automation, big data processing, etc.
- Acquisitions/mergers — When companies combine operations, it is common practice to maintain applications and services on multiple public cloud environments.
- Shadow IT teams — Development and operations (DevOps) and other teams, which cannot wait for a central IT organization to allocate network resources, often secure their own arrangements with public cloud service providers.
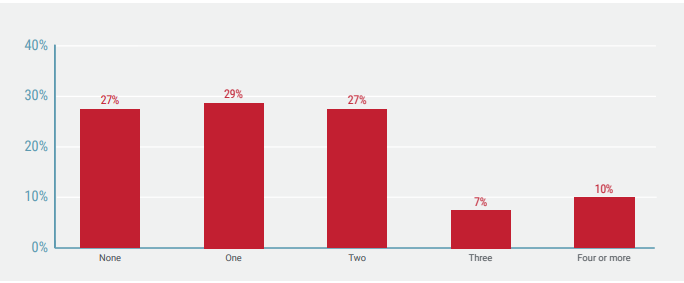 Figure 1: Use of public cloud environments
Figure 1: Use of public cloud environmentsThree-fourths of Radware survey respondents said that their organizations used at least one public cloud, and more than two of five used two or more public clouds. Large and worldwide companies were most likely to have used three or more public cloud environments. Amazon Web Services (AWS) (44%) and Microsoft Azure (43%) were the two most used public cloud vendors. Only about one-quarter of respondents said that they have not used public clouds.
Balancing Business Challenges
The strategic use of multiple public cloud environments introduces new business challenges. Although organizations are better able to respond rapidly to market opportunities, the decentralized nature of this model adds complexity to how applications and computing resources are secured.
[You may also like: Cloud Migration: Times, They Are A-Changin’]
Organizations — whether via chief information security officers (CISOs) or other security teams — need to stay abreast of the technological and environmental changes in their public clouds. There is a need for visibility across all the different platforms from one holistic solution that enables management of the security posture by utilizing one common language. The goal is to be able to:
- Prevent attacks by reducing the size of the attack surface
- Detect and identify evolving threats
- Respond with accurate and effective mitigation
Security professionals weighed the benefits of having used a public cloud against the risks. Although only 10% of respondents felt that their data was more secure in a public cloud environment, 30% felt that the benefits of the cloud, such as agility and lower costs, justified the security risks.
[You may also like: Excessive Permissions are Your #1 Cloud Threat]
But lack of visibility about which entity — the organization or the public cloud service provider — is responsible for specific elements of network security caused security breaches. In Radware’s 2019 State of Web Application Security Research report, 65% said that they aren’t clear about security boundaries, and 53% of respondents experienced data exposure as a result of misunderstandings with the public cloud provider regarding security responsibilities.
[adbutler zone_id="276005"]
The Need to Rethink Security Strategies
Often when organizations migrate from on-premise to public cloud environments, security teams want to continue to use the same approach for protecting applications and data. But use of a public cloud, especially multiple public clouds, introduces new attack vectors that require better visibility into what is happening across the entire ecosystem. Security tools offered by public cloud vendors are often a popular choice to fill the gap following migration.
[You may also like: Visibility: Do You Know What’s In Your Network?]
The majority of respondents who said that their organizations used public cloud environments indicate that they selected native security tools or a combination of native tools with third-party solutions to secure their public cloud. Possible reasons for organizations adopting a heterogeneous approach to securing public clouds might be because public cloud vendors are not cybersecurity experts and typically provide best-of-breed security tools vs. a 360-degree holistic security solution. Many organizations recognize the risks associated with relying solely on a public cloud vendor for security and opt to include a dedicated cybersecurity/DDoS vendor.
Strategies to Secure Multiple Public Cloud Environments
Applying security protocols that were successful for on-premise environments will not work as applications and data migrate to public cloud environments. Security teams need to adopt new strategies to harden security across their entire public cloud ecosystem by:
- Adopting third-party security solutions. The public cloud service providers’ core competencies are not network security. Rather, network protection is generally a proprietary add-on to their service offerings that operate in a silo. Instead, select a security solution from a vendor with proven expertise and thought leadership. Choose a holistic approach that can protect multiple public cloud environments with consistent implementation and maintenance of security protocols while automating prevention, detection and response.
- Engaging a fully managed security service. To overcome staff and skills shortages, take advantage of an outside team focused on securing your public cloud network security environments.
- Centralizing management of network security. With a security solution in place that provides visibility and control of security policies across all virtual public clouds and clouds, it is possible to achieve tighter regulation of user credentials and permissions from a centralized dashboard.

Read Radware's “2019-2020 Global Application & Network Security Report” to learn more.
Download Now