Bots are awesome. They really are. So are APIs; both boost productivity by advancing automation, the exchange of business data and support decision making. If only everything was so perfect… Unfortunately, 81% of organizations have reported attacks against their APIs, and 75% suffered bot attacks in a 12 month period.
Modern applications and services rely heavily on API integration and communication. While on one hand, APIs provide synergy and efficiency to business operations by simplifying the architecture and delivery, on the other, it introduces a wide range of risks and vulnerabilities. One of the major threats is automated traffic – detection of bots with malicious intent.
Among our customer base, the portion of bad bot traffic has gone up by 50% in the first half of 2020 compared to 2019.
API Use Cases & the Impact of Malicious Bots
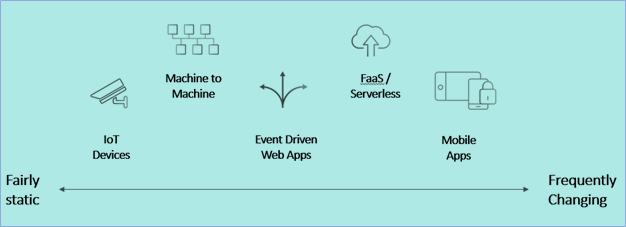 API use cases
API use casesProtecting the fairly static use cases is perceived as easier, since the API calls are anticipated and the JSON/XML schemes are predicted, so building a baseline of normal behaviors to detect anomalies is relatively easy. But does it serve the business objective?
[You may also like: Recommendations for Managing a Bad Bot Problem]
The three verticals that suffer the most are eCommerce, gaming and travel. All three monetize APIs heavily and use them for processing sensitive information. As such, they have zero tolerance to false positives (will you leave a gamer out? Will you block a paying user?), which is usually what happens when anomaly detection technology meets a new pattern, especially if this technology was built for a web or a mobile application. However, the majority (56%) of APIs out there are not standard web or mobile, and require a different approach:
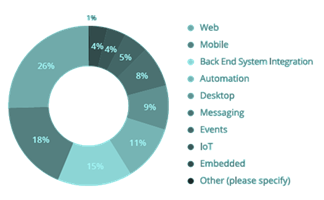 Source: The State of API 2019, SMARTBEAR (n=3,372)
Source: The State of API 2019, SMARTBEAR (n=3,372)Obviously, the rapidly dynamic scenarios require continuously adaptive protection, which is also a challenge for machine learning; the algorithms must quickly figure out whether a new pattern is legitimate or not and tune the security policy accordingly.
Securing your APIs properly requires a purpose-built business logic, otherwise you will deal with a lot of noise. In other words, NO – you can’t stretch the same heuristics from a WAF service or bot management solution tailored for web application and apply them to protect APIs (unless, of course, you enjoy angry users and tedious exception handling).
[You may also like: 4 Verticals Most Targeted by Bad Bots]
Business Impact of Malicious Bots Targeting APIs
The first one is obvious – if you eliminate bad bot traffic, you will be saving a substantial amount, especially if your services are running on public cloud infrastructure. Making less calls means your utilization costs will go down. The rest of it is more complex. You probably do rely on bots for business objectives – search engines, legitimate scrapers, fetchers, and other sorts – so the whole point is to understand the intent of the bot.
 Most common automated threats targeting APIs
Most common automated threats targeting APIsWhat? Can a bot have intent?
Well, technically the one with the intent is the human who has written or is using the bot. However, since the bots will operate similarly, you need to take into account multiple indicators to determine whether this intent is legitimate or malicious. Since sophisticated bots today can mimic user behavior, you need to cross check technical details with behavioral patterns. In this instance, behaviors that are typical to APIs.
For example, if there’s a water meter or an activity tracker making an API call every five minutes to sync, or an API that transfers data to a serverless function, or simply an attempt to login with user credentials, you need to distinguish between legitimate activity and abuse by bots.
[adbutler zone_id="276005"]
Symptoms of Bot Attacks on APIs
The following are indicators of a bot attack on APIs:
- Single HTTP request (from a unique browser, session or a device)
- An increase in the rate of errors (e.g., HTTP status code 404, data validation failures, authorization failures, etc.)
- Extremely high application usage from a single IP address or API token
- A sudden uptick in API usage from large, distributed IP addresses
- A high ratio of GET/POST to HEAD requests for a user/session/IP address/API token compared to legitimate users
Key API Vulnerabilities and Automated Attacks
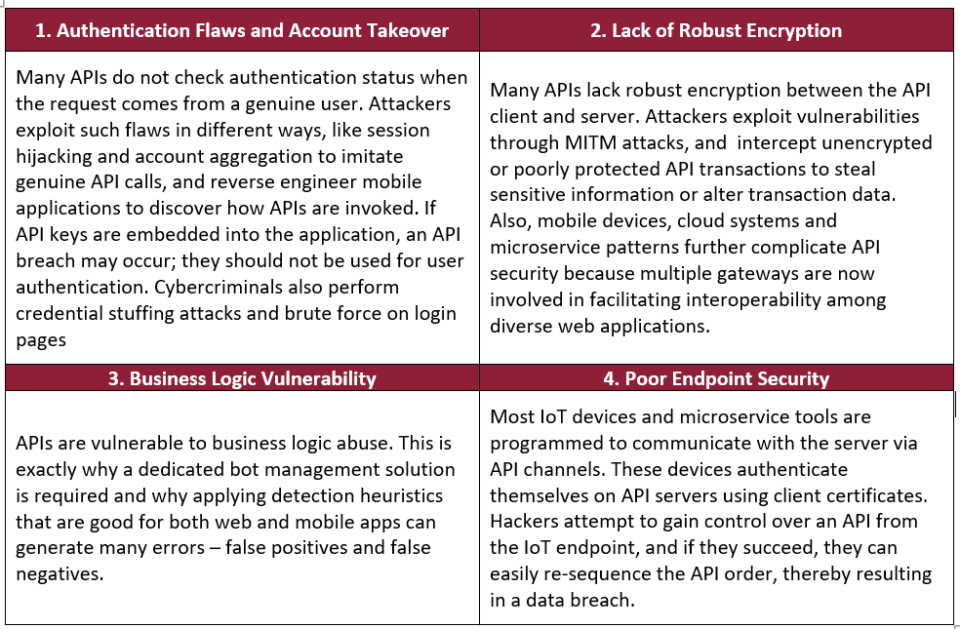
Today, Radware introduced advanced API protection from automated threats to help organizations:
- Secure sensitive data from leaking because of bot attacks such as ATO or web-scraping
- Eliminate financial impact of bot attacks on monetization APIs
- Reduce API consumption and utilization costs
- Provide visibility into violations and exploitation of bots targeting APIs with intent-based analytics

Read Radware's “The Big Bad Bot Report” to learn more.
Download Now