A
multi-cloud approach enables organizations to move application services to
various public cloud providers depending on the desired service level and price
points. Most organizations will use multiple cloud providers; some in addition
to their private cloud and on premise deployments.

Multi-cloud subsumes and is an evolution of hybrid cloud. According to IDC, enterprise adoption of multi-cloud services has moved into the mainstream; 85% of organizations are using services from multiple cloud providers while 93% of organizations will use services from multiple cloud providers within the next 12 months.
C-level executives are pushing a “cloud first” policy for their IT service capabilities.
Multi vs. Hybrid Cloud Deployment
Multi-cloud may include any combination of public cloud (eg. Microsoft Azure, AWS), SaaS applications (eg. Office 365, Salesforce), and private clouds (eg. OpenStack, VMware, KVM).
[You may also like: Transforming Into a Multicloud Environment]
Hybrid cloud deployments might be permanent, to serve a business need, such as to maintain proprietary data or intellectual property information within an organizations control, while public clouds may be maintained to initiate an eventual transition to cloud – whether public or private.
Sometimes organizations adopt multi-cloud deployments in order to enable DevOps to test their services and reduce shadow IT or to enhance disaster recovery or scalability in times of need.
Security Considerations
As organizations transition to the cloud, availability, management AND security should be top-of-mind concerns in the move to adopt containers. This concern is evident in the survey conducted by IDC in April 2017.
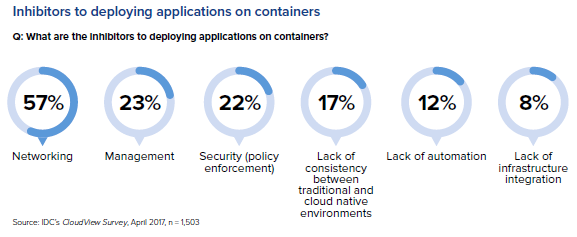
In addition to using built-in tools for container security, traditional approaches to security still apply to services delivered through the cloud.
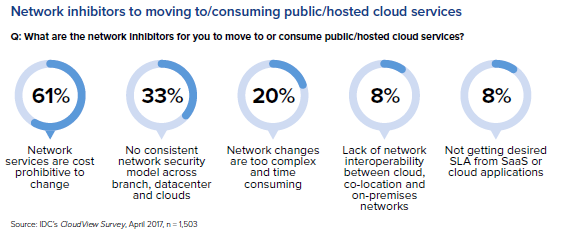
Many container applications services composed using Application Programming Interfaces (APIs) are accessible over the web, and they are open to malicious attacks. Such deployments also increase the attack surface, some of which may be beyond an organization's direct control.
[You may also like: How to Prevent Real-Time API Abuse]
Multi-Pronged Prevention
As hackers probe network and application vulnerability in multiple ways to gain access to sensitive data, the prevention strategy for unauthorized access needs to be multi-pronged as well:
- Routinely applying security patches
- Preventing denial of service attacks
- Preventing rogue application ports/applications from running in the enterprise or on their hosted container applications in the cloud
- Routine vulnerability assessment scans on container applications
- Preventing bots from targeting applications and systems while being able to differentiate between good bots and bad bots
- Scanning application source code for vulnerabilities and fixing them or using preventive measure such as deploying application firewalls
- Encrypting the data at rest and in motion
- Preventing malicious access by validating users before they can access an application
[You may also like: Application Delivery Use Cases for Cloud and On-Premise Applications]
It is important to protect business-critical assets by enhancing your security posture to varying threat landscapes. You can do that by gaining visibility into multiple threat vectors using SIEM tools and analytics, and adopting security solutions such as SSL inspection, intrusion detection and prevention, network firewalls, DDoS prevention, Identity and Access Management (IAM), data leak prevention (DLP), SSL threat mitigation, application firewalls, and identity management.

Read “2019 C-Suite Perspectives: From Defense to Offense, Executives Turn Information Security into a Competitive Advantage” to learn more.
Download Now