On December 1, FireEye announced that it was attacked by what they believe is a sophisticated threat actor, one whose discipline, operational security and techniques indicates a state-sponsored adversary.
The FireEye analysis pointed to a global intrusion campaign, a supply chain attack trojanizing SolarWinds Orion software updates performed by an advanced and sophisticated threat actor and that distributes a backdoor dubbed SUNBURST.

First, What Is A Supply Chain Attack?
A supply chain attack is a cyberattack that seeks to damage an organization by targeting less secured elements in the supply network. For example, in 2013, Target was hit by a data breach that saw 40 million customer credit and debit card information leaked when malware was introduced into their point-of-sale system in over 1,800 stores. It is believed, although not officially confirmed, that cyber criminals infiltrated into Target’s network using credentials stolen from Fazio Mechanical Services, a Pennsylvania-based provider of HVAC systems.
A Trojanized Orion
On Sunday, SolarWinds published a press release admitting to a breach by a sophisticated actor who found a way to inject malicious code in SolarWinds’ Orion IT monitoring and management software. The malicious code got distributed to many government and high-profile organizations through SolarWinds’ website as part of software update packages. The digitally signed "SolarWindows.Orion.Core.BusinessLayer.dll" plugin module contained backdoor code hiding in plain sight by using fake variable names and tying into legitimate components and gets loaded and invoked by the Orion software framework. The malicious plugin module is tracked as SUNBURST by FireEye and Solorigate by Microsoft.
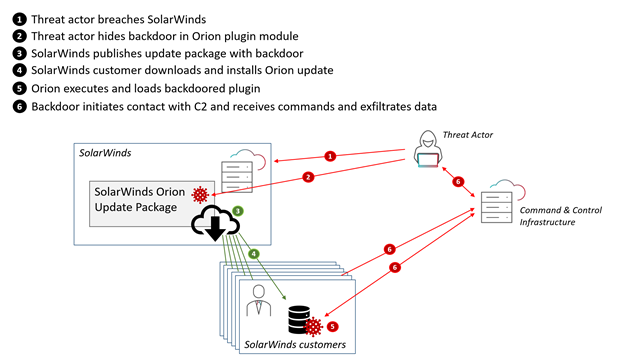 Supply Chain attack on SolarWinds Orion update package resulting in backdoor installation in Orion customers
Supply Chain attack on SolarWinds Orion update package resulting in backdoor installation in Orion customersThe malicious code was distributed part of update version 2019.4 through 2020.2.1. that were released between March and June 2020. According to the in-depth analysis by FireEye, after an initial dormant period of up to two weeks, the backdoor code retrieves and executes commands that allow it to transfer files, execute files, profile the system, reboot the machine and disable system services.
The malware masquerades network traffic as the Orion Improvement Program (OIP) protocol and stores reconnaissance results within legitimate plugin configuration files allowing it to blend in with legitimate SolarWinds activity. The backdoor uses multiple obfuscated blocklists to identify forensic and anti-virus tools running as processes, services and drivers. The backdoor determines its command-and-control server using a Domain Generation Algorithm (DGA) which allows it to randomly generate one of many C2 hostnames making it more robust against detection and blocklisting. Command-and-control traffic is concealed through stenography in what looks like benign code exchange for .NET assemblies.
[You may also like: You’re Only As Protected As Your Provider’s SOC]
Who Got Compromised by the SolarWinds Attack?
SolarWinds confirmed 18,000 Orion customers could be compromised. Reuters reported that the attackers appear to have focused on a small number of high-value targets, leaving most Orion customers unaffected. According to ZDNet, several IT administrators reported that they found signs of the malware-laced Orion update on their systems, but they did not find signs of second-stage payloads, typically used by the attackers to escalate access to other systems and internal customer networks.
An Advanced and Sophisticated Threat Actor
The use of advanced techniques to deploy a light malware to accomplish the mission and avoid detection through obfuscation and stenography points to a highly sophisticated threat actor. FireEye is tracking the threat group with a neutral codename UNC2452, although sources speaking with the Washington Post linked the intrusion to APT29, also known as Cozy Bear, and indicating a Russian hacker group believed to have working relations with the Russian Foreign Intelligence Service. Kremlin spokesman Dmitry Peskov told reporters Monday that Russia had "nothing to do with" the hacking.
What Does It Mean for SolarWinds Customers?
Even if the attackers focused on a small number of high-value targets, how does one define high-value? Any organization using the SolarWinds Orion software platform and that installed updates for the platform between March and June 2020 is backdoored and potentially breached. Updating to the latest Orion software will remove the backdoor, but without forensic analysis it is not possible to exclude the possibility that other malware was loaded, or user accounts created that allow the malicious actors access to the victim’s network and systems even after cleaning and mitigating the original threat.
[You may also like: Radware Threat Researchers Live: 2021 Predictions]
What Was Stolen During the FireEye Attack?
Consistent with a nation-state cyberespionage, the attacker sought information related to government customers. While the attacker was able to access some internal systems, at the time of the announcement, there was no evidence of the attackers having exfiltrated confidential or sensitive data. FireEye did confirm that the attacker accessed and stole their red team assessment tools.
The stolen tools range from simple scripts used for automating reconnaissance to entire frameworks that are similar to publicly available technologies such as CobaltStrike and Metasploit. Many of the red team tools have already been released to the community and are already distributed in their open-source virtual machine, CommandoVM.
The red team tools stolen by the attacker did not include zero-day exploits. The tools apply known and documented methods that are used by other red teams around the globe. Some of the tools are publicly available tools modified to evade basic security detection mechanisms. Other tools and frameworks were developed in-house by the FireEye red team. FireEye has published a collection of rules that provide countermeasures against the weaponized vulnerabilities used in their red team tools.
For more details on the impact of these stolen tools, please read our threat alert.
[adbutler zone_id="276005"]
What Should You Do?
The stolen FireEye Red Team tools not only applies to SolarWinds Orion victims but impacts every organization across the globe. The stolen tools do not leverage unknown vulnerabilities or zero-day attacks, but they are still weaponized exploits that can be automated and leveraged to scale attacks. The stolen tools might have a higher degree of automation and integration compared to publicly available tools that were leveraged in the past.
Vulmon, a vulnerability search engine with vulnerability intelligence features, compiled a list of vulnerabilities based on the countermeasures published by FireEye. Below vulnerabilities should be patched and mitigated as soon as possible if not already. Customers that were holding off on patching or upgrading certain systems should do so immediately.
- CVE-2019-11510: Pulse Secure Pulse Connect Secure unauthenticated path traversal
- CVE-2020-1472: Microsoft Active Directory privilege escalation vulnerability is also known as Zerologon
- CVE-2018-13379: Fortinet Fortigate SSL VPN unauthenticated path traversal
- CVE-2018-15961: Adobe ColdFusion remote code execution vulnerability
- CVE-2019-0604: Microsoft SharePoint remote code execution vulnerability
- CVE-2019-0708: Microsoft Windows Remote Desktop Services (RDS) remote code execution vulnerability also known as BlueKeep
- CVE-2019-11580: Atlassian Crowd remote code execution vulnerability
- CVE-2019-19781: Citrix Application Delivery Controller and Citrix Gateway remote code execution vulnerability
- CVE-2020-10189: RCE for Zoho ManageEngine Desktop Central remote code execution vulnerability
- CVE-2014-1812: Microsoft Windows local privilege escalation
- CVE-2019-3398: Atlassian Confluence authenticated remote code execution
- CVE-2020-0688: Microsoft Exchange remote code execution
- CVE-2016-0167: Local privilege escalation on older versions of Microsoft Windows
- CVE-2017-11774: Remote code execution in Microsoft Outlook via specially crafted URI (phishing) also known as Microsoft Outlook Security Feature Bypass Vulnerability
- CVE-2018-8581: Microsoft Exchange Server elevation of privilege vulnerability
- CVE-2019-8394: Zoho ManageEngine ServiceDesk Plus (SDP) unauthenticated file upload
What Should SolarWinds Orion Customers Do?
SolarWinds recommends all customers immediately upgrade to Orion Platform release 2020.2.1 HF 1, which is currently available via the SolarWinds Customer Portal. In addition, SolarWinds has released additional mitigation and hardening instructions here. In addition, FireEye published IOCs and countermeasures here. More technical details regarding the actor’s tactics, techniques and procedures (TTPs) were published by FireEye.

Download Radware's “Hackers Almanac” to learn more.
Download Now