By Shai Levi and Namik Binyaminov
The Radware Vulnerability Research Team (VRT) has been tracking and investigating web service exploits used by malicious actors over the course of 2019. The exploits are typically performed through automated scanning and attack programs and leveraged to either compromise or discover vulnerable servers and devices.

Radware’s Global Deception Network
Radware’s Global Deception Network is a network of globally distributed sensors – honeypots – running services that attract bots that are attempting to compromise, abuse and hack into computers, create new botnets and launch DDoS attacks. The deception network attracts hundreds of thousands of malicious IPs, generating millions of events on a daily basis. The automatic analysis algorithms provide insights and categorization of various types of malicious activity from reconnaissance through password brute force attempts to injections and RCE.
Radware proprietary and patented algorithms running on the deception network are used to catalog and identify new and emerging threat actors, including web application attackers, botnets, IoT bots and DNS attackers, as well as to analyze malicious behavior designed to hide the attacker such as spoofing and anonymizing.
Below are the top ten most prevalent exploits leveraged in large scale attack or reconnaissance campaigns targeting web services.
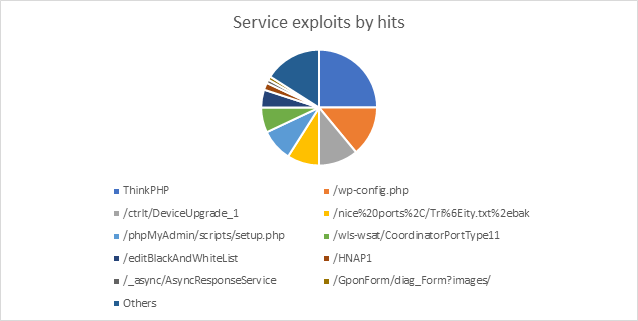 Figure 1: web attacks distribution
Figure 1: web attacks distribution /TP/public/index.php
25% of all web services hits.
Remote code execution vulnerability in NoneCMS ThinkPHP framework.
More Uniform Resource Identifiers (URI) related to the same vulnerability:
• /TP/index.php
• /thinkphp/html/public/index.php
• /thinkphp/public/index.php
• /TP/html/public/index.php
• /html/public/index.php
ThinkPHP is a web application development framework based on PHP. It focuses on development of web applications, mainly used in enterprise projects. The framework is very popular in China. The vulnerability was discovered in December 2018 by Github user twosmi1e and affected NoneCMS ThinkPHP 5.x with maintenance releases before v5.0.23 and v5.1.31.
The vulnerability, CVE-2018-20062 allows a remote attacker to execute arbitrary code on an affected NoneCMS ThinkPHP 5 server. A remote unauthenticated attacker is able to craft a malicious request to run code on the victim’s machine leading to complete takeover of NoneCMS ThinkPHP 5 server.
/wp-config.php
14% of all web services hits.
Sensitive Data Exposure vulnerability of WordPress configuration files.
WordPress is the most popular content management system (CMS) in the world. WordPress is an open source CMS. According to w3techs, it has a market share of 36% of all the websites globally and 62.8% of all CMS based websites, making it a highly targeted system by malicious actors.
‘wp-config.php’ is an important WordPress configuration file. The file contains the base configuration details for the website, such as database connection information and certificates. An attacker with access to ‘wp-config.php’ file can retrieve sensitive information about the server and use it to gain control of the WordPress instance and its associated database.
/ctrlt/DeviceUpgrade_1
11% of all web services hits.
Huawei HG532 routers Remote Code Execution vulnerability – port 37215.
Huawei HG532 is a high-speed wireless router designed for household and small offices (SOHO). In November 2017, Huawei published a security advisory regarding a remote code execution (RCE) vulnerability, CVE-2017-17215. By sending malicious requests to port 37215, an attacker could remotely execute arbitrary code without authentication.
/nice%20ports%2C/Tri%6Eity.txt%2ebak
9% of all web services hits.
Unescaped URI: /nice ports,/Trinity.txt.bak
Information disclosure vulnerabilities web servers.
The URI above indicates a network scan in attempt to find vulnerable web server. The request was originally crafted for Nmap scanner, but attacks can use it with other tools or scripts.
Nmap is a network scanner which used to discover hosts and services on a computer network by sending packets and analyzing the responses. In this request the attacker uses ASCII escaped characters in attempt to generate HTTP 404 error message to probe a web server. A successful scan can reveal important information about the web server code and possibly even vulnerabilities through response headers and error messages.
/phpMyAdmin/scripts/setup.php
9% of all web services hits.
phpMyAdmin Remote Code Execution vulnerability.
phpMyAdmin is a free and open source administration tool written in PHP for MySQL and MariaDB. phpMyAdmin frequently used as databases and permissions managing tool and therefore highly targeted by attackers. In March 2009, phpMyAdmin project released security advisory PMASA-2009-3 for phpMyAdmin 2 versions before 2.11.9.5 and phpMyAdmin 3 versions before 3.1.3.1.
The vulnerability, CVE-2009-1151 is a PHP Remote Code Execution vulnerability. One of phpMyAdmin components - setup.php allows remote attackers to inject arbitrary PHP code into a configuration file via the save action. A remote unauthenticated attacker can craft a malicious POST request to inject code on the victim’s machine which can result in execution of an arbitrary malicious PHP code in the context of the webserver process.
/wls-wsat/CoordinatorPortType11
7% of all web services hits.
Oracle WebLogic server Remote Code Execution vulnerability.
Oracle WebLogic Server is an application server for building and deploying Java Enterprise Edition applications. In October 2017 Oracle have published Critical Patch Update Advisory which covered CVE-2017-10271, affected versions are 10.3.6.0.0, 12.1.3.0.0, 12.2.1.1.0 and 12.2.1.2.0.
The vulnerability, CVE-2017-10271 is a Remote Code Execution vulnerability. WLS Security component of WebLogic fails to properly deserialize unsafe XML. A remote unauthenticated attacker can craft a malicious XML request which will run his code on the victim’s machine which can result in complete takeover of Oracle WebLogic server.
/editBlackAndWhiteList
5% of all web services hits.
NVMS-9000 Digital Video Recorder hardcoded admin credentials and Remote Code Execution vulnerabilities.
NVMS-9000 Digital Video Recorder is a popular DVR appliance from Shenzhen TVT Digital Technology Co. Ltd (TVT). In April 2018, TVT have published Critical advisory and a firmware update which covers the 3 vulnerabilities.
The observed vulnerability is a Remote Code Execution vulnerability NVMS-9000 Digital Video Recorder. NVMS-9000 had a hardcoded authentication admin credentials. A remote unauthenticated attacker can use the hardcoded admin credentials to run his code on the victim’s machine.
[adbutler zone_id="276005"]
/HNAP1
2% of all web services hits.
HNAP protocol Authentication Bypass vulnerabilities.
Scanning attempt in order to find routers with open HNAP interface.
Network Administration Protocol (HNAP) is a proprietary network device management protocol developed by Pure Networks and later acquired by Cisco. It allows advanced programmatic configuration and management by remote entities. Starting at 2010, many vulnerabilities were discovered in devices that implemented HNAP such as D-Link and Linksys routers for example CVE-2014-8244 vulnerability.
/_async/AsyncResponseService
1% of all web services hits.
Oracle WebLogic server Deserialization Remote Code Execution vulnerability.
Oracle WebLogic Server is an application server for building and deploying enterprise Java EE applications. The vulnerability was found in WebLogic versions 10.3.6.0.0 and 12.1.3.0.0 and discovered and published by China National Vulnerability Database on April 17, 2019.
The vulnerability, CVE-2019-2725 is a Remote Code Execution vulnerability. One of Oracle WebLogic components fails to properly deserialize the input data. A remote unauthenticated attacker can craft a malicious XML request to run code on the victim’s machine which can result in complete takeover of Oracle WebLogic server.
/GponForm/diag_Form?images/
1% of all web services hits.
GPON home routers vulnerable to authentication bypass and remote command execution vulnerability.
GPON routers is a high-speed wireless router designed for household and small office customers. GPON is a type of passive optical network that uses fiber-optics. Most of GPON routers are provided by ISPs which made the router is very popular as home router. The estimation is millions of GPON routers are in use in the global.
The vulnerabilities CVE-2018-10561 and CVE-2018-10562 are authentication bypass and remote command execution respectively. The vulnerabilities allow remote attacker to execute arbitrary command in affected version of Gpon routers.
Attackers never stop their expansion efforts to scan and exploit known vulnerabilities in the entire cyberspace. The chronological charts show that when a new vulnerability discovered and there is an exploit to it, in a matter of days the attackers will add it to their targets list and will try to exploit it.
Their focus is not necessary on new attacks and attack vector as one can expect, but rather on popular technologies and devices with known, easy to exploit vulnerabilities, going back to vulnerabilities initially reported in 2009 – yes, some organizations lag so much behind with either upgrading or patching and should upgrade their assets as soon as possible.

Read Radware's “2019-2020 Global Application & Network Security Report” to learn more.
Download Now