During the first quarter of 2025, hacktivist activity saw a distinct shift in focus, with the United States emerging as the most targeted country globally. According to collected claims from known hacktivist groups, the U.S. alone accounted for 13.5% of all observed distributed denial-of-service (DDoS) attacks between January 1 and March 31. This equates to a staggering 558 claimed attacks—well ahead of Ukraine (400) and Israel (340), which were the second and third most targeted countries, respectively.
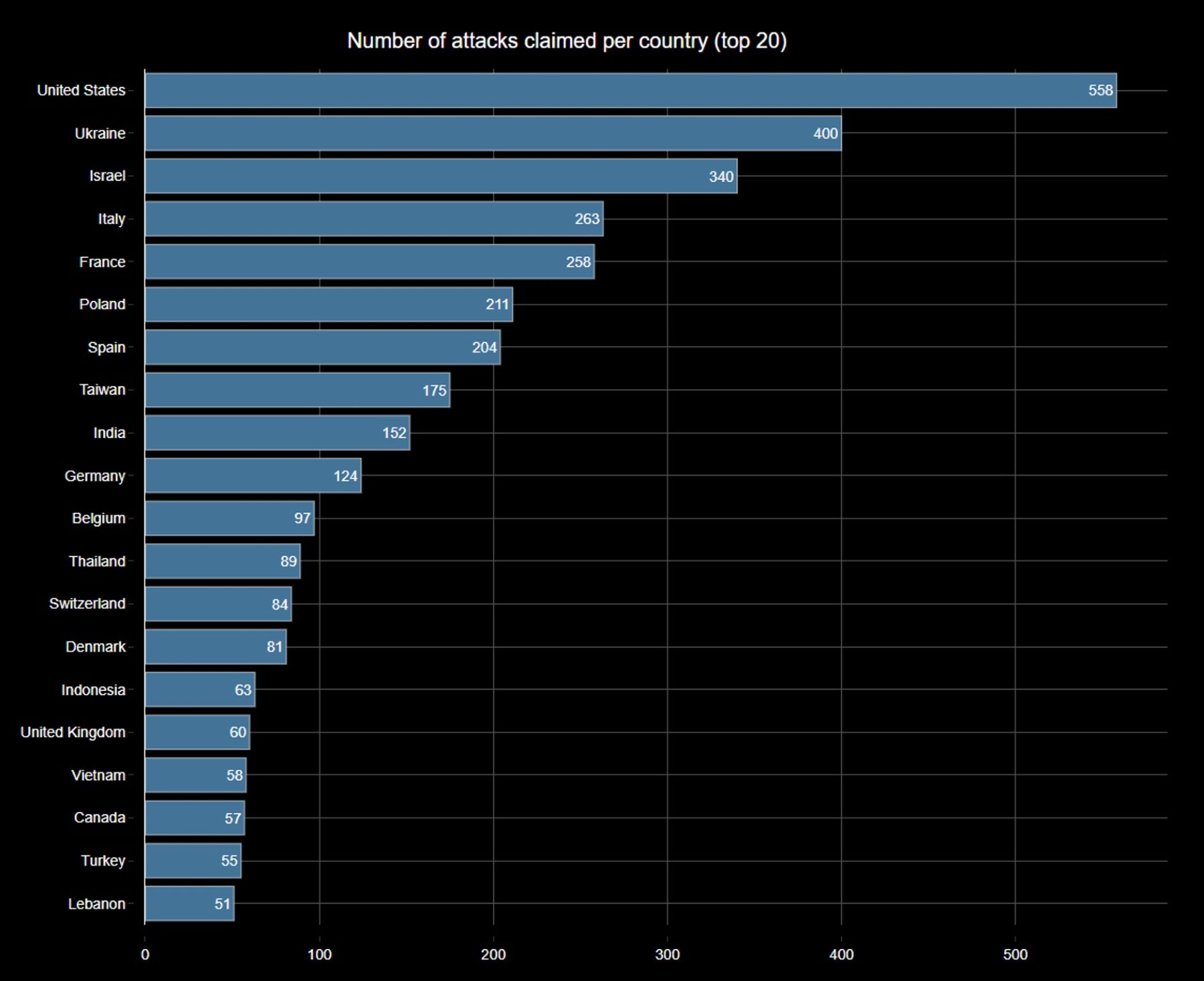
Figure 1: Most targeted countries by hacktivist DDoS in Q1 of 2025 (source: Radware)
The data highlights the broadening geopolitical scope of hacktivist campaigns, with countries such as Italy, France, Poland, and Spain also appearing prominently on the list of top targets. These findings reflect a continuation of the trends observed in 2024, with heightened tensions driving politically and ideologically motivated cyberattacks. Notably, Taiwan and India also made the top ten, suggesting an increased hacktivist focus on areas with ongoing regional or global significance.
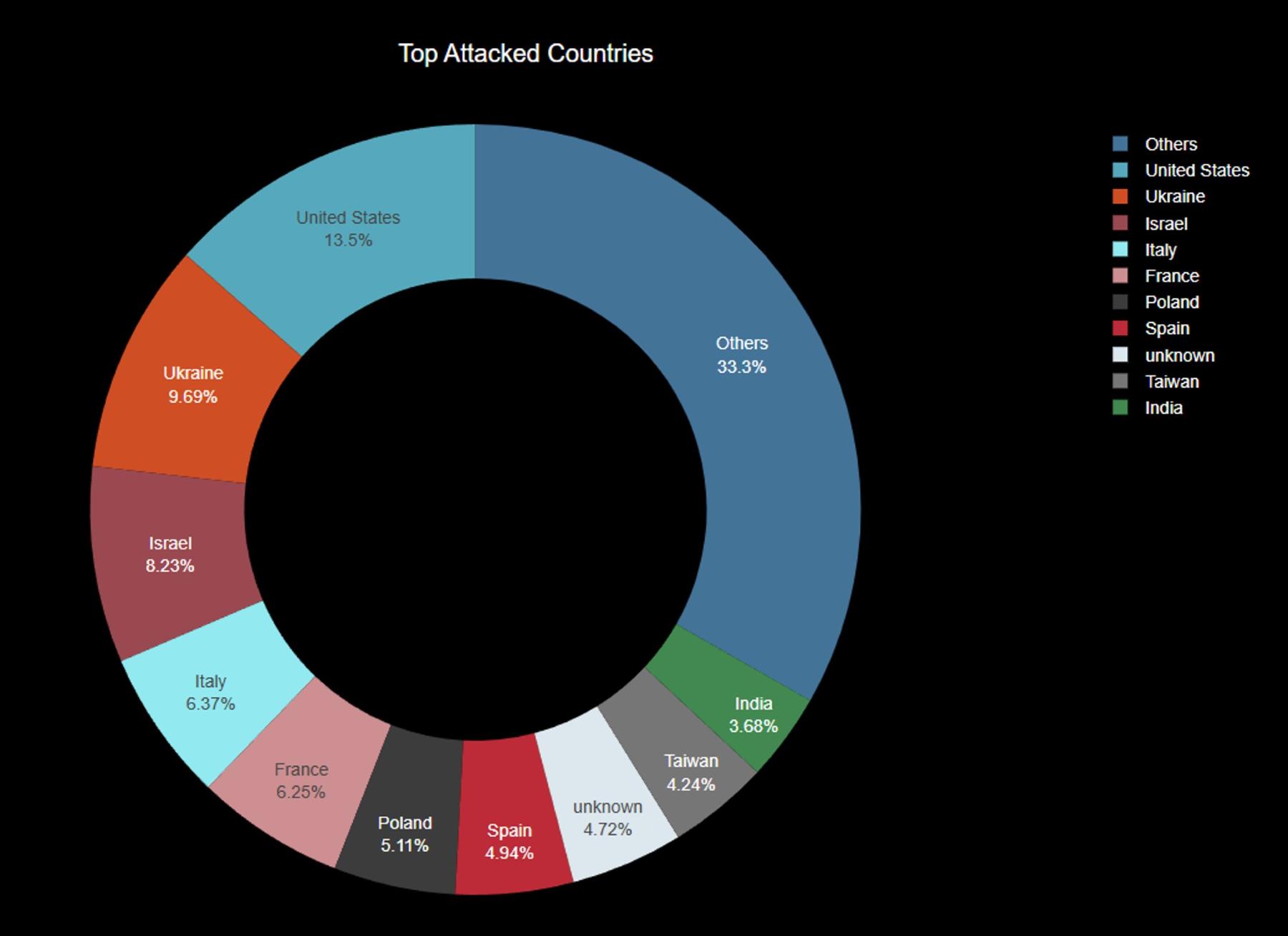
Figure 2: Most targeted countries by hacktivist DDoS in Q1 of 2025 (source: Radware)
The chart in Figure 1 also shows a long tail of activity, with dozens of countries experiencing smaller volumes of attacks. However, the concentration of claims in the top five—particularly the dominance of the U.S.—suggests that hacktivist groups are increasingly aligning their operations with Western targets, either as a reaction to foreign policy decisions, support for specific allies, or to garner visibility and promote their services.
Threat Groups Targeting U.S. Organizations
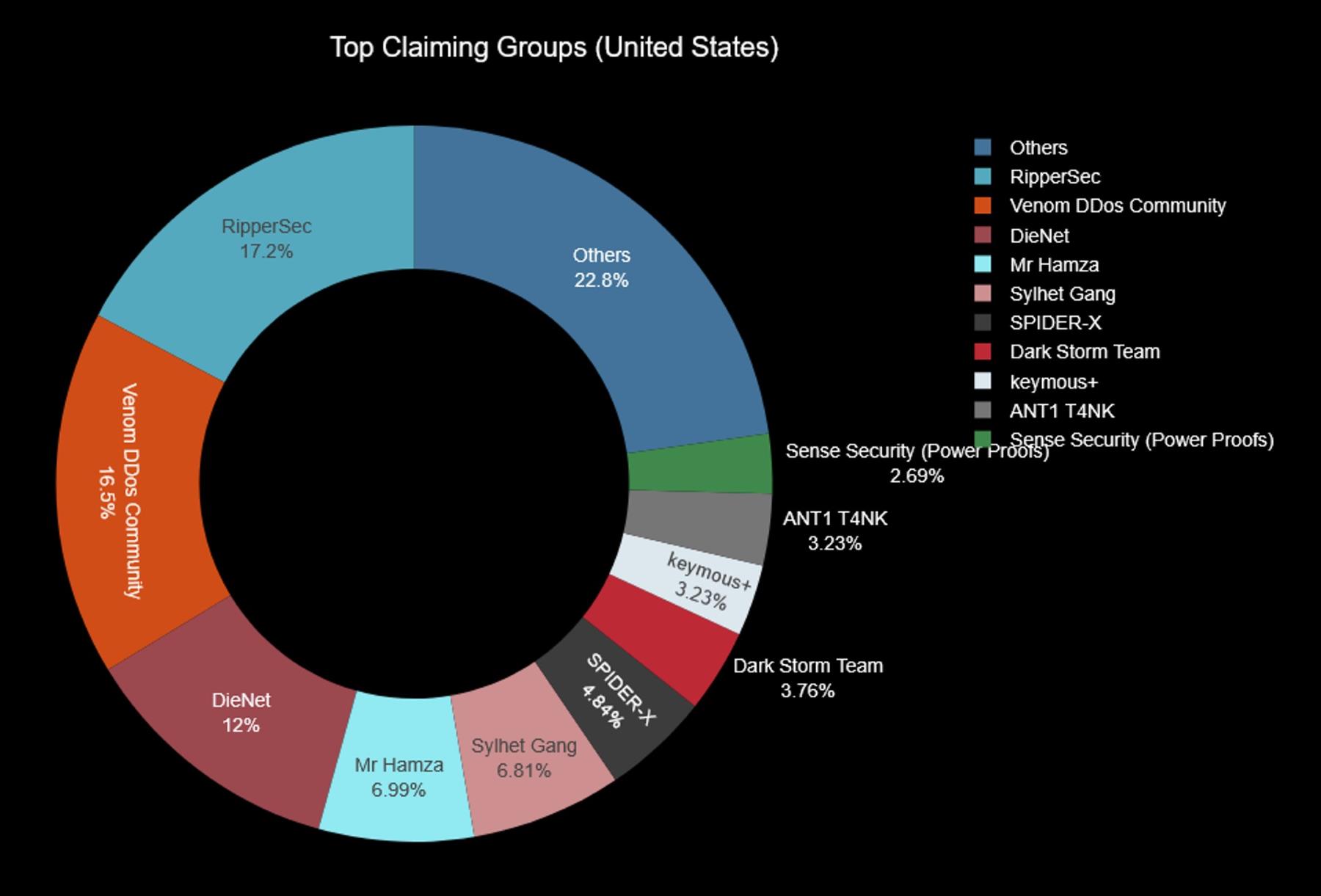
Figure 3: Top claiming threat groups targeting United States organizations in Q1 of 2025 (source: Radware)
We observed a marked shift from DDoS attack claims for advertisement by DDoS-for-Hire Services to more politically driven threat groups and messaging. The top claiming groups include RipperSec, DieNet, Mr Hamza, Sylhet Gang, Spider-X and KMP Group (keymous+), all politically motivated hacktivist threat groups retaliating against perceived aggressions of American power abroad. Earlier this month, we alerted about activity from DieNet that was escalating against US organizations.
Dark Storm Team, Venom DDoS, ANT1 T4NK Cyber Team, and Sense Security operate as DDoS-for-Hire services, using high-profile attacks on prominent U.S. targets as a means of advertising their offerings. This tactic mirrors the approach taken by Executor DDoS, which was the top threat group by number of claimed attacks targeting U.S. organizations in 2024.
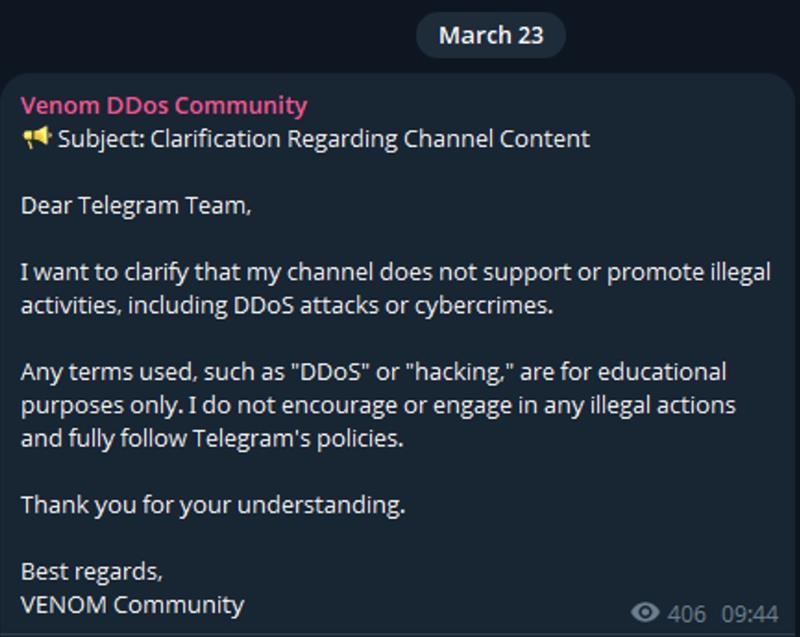
Figure 4: Venom DDoS messages posted on Telegram (source: Telegram)
Figure 5: Sense Security announcement on Telegram (source: Telegram)
Most Targeted U.S. Industries
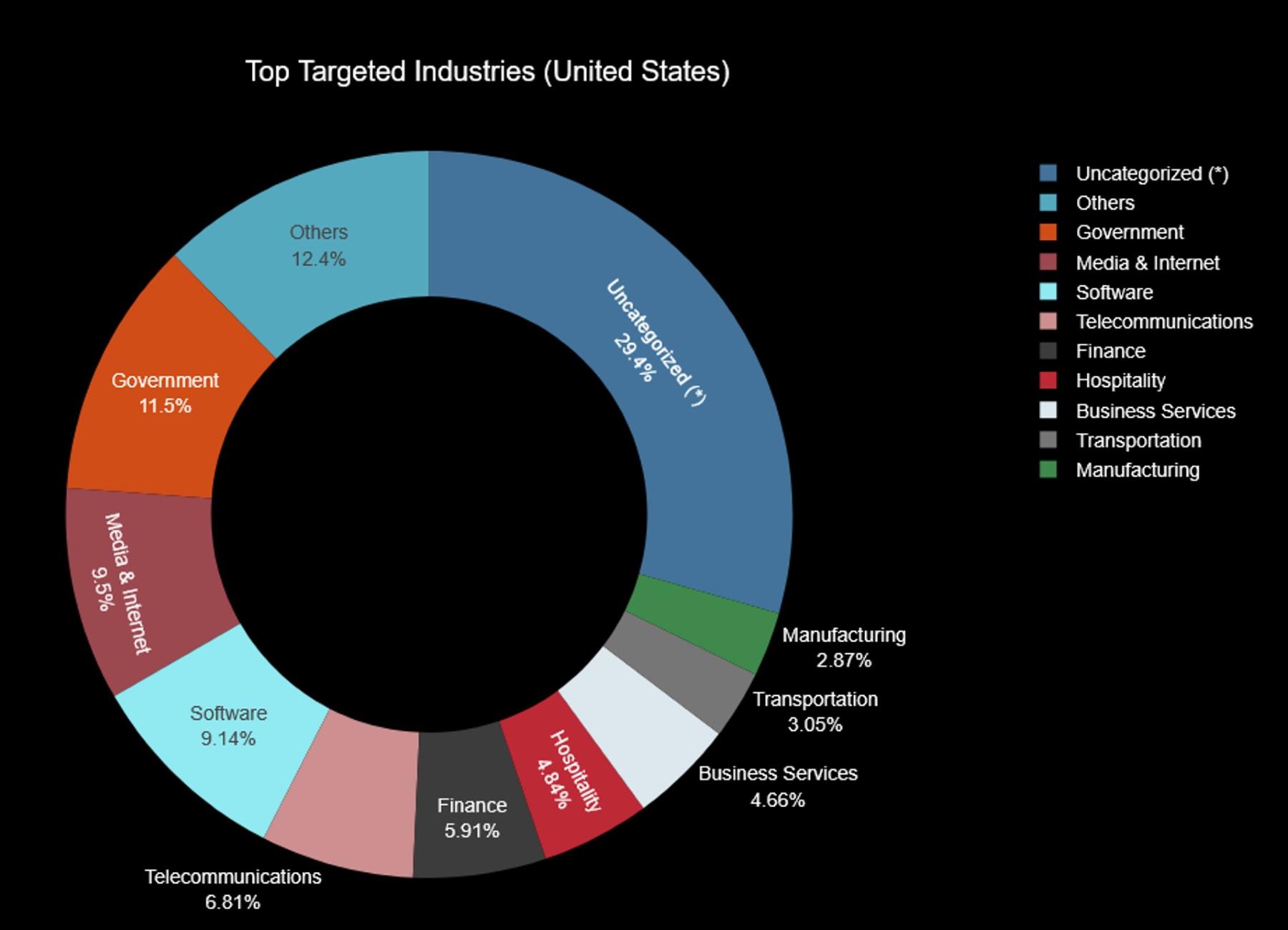
Figure 6: Top targeted U.S. industries for Q1 2025 (source: Radware)
The chart above highlights the top targeted industries in the United States during Q1 2025, revealing key sectors most affected by hacktivist groups. Government organizations accounted for 11.5% of claimed attacks, underscoring their continued status as high-value targets for politically motivated threat actors. Media & Internet companies followed closely at 9.5%, reflecting the strategic appeal of platforms that influence public opinion or serve as major communication hubs. The software sector wasn’t far behind at 9.14%, indicating persistent interest in disrupting critical digital infrastructure and SaaS providers.
Telecom and finance were also notably impacted, making up 6.81% and 5.91% of the attack claims, respectively. Sectors that, if taken offline, can cause widespread service disruptions and economic ripple effects. Business services (4.66%), hospitality (4.48%), transportation (3.05%), and manufacturing (2.87%) rounded out the most affected industries. Together, these trends point to a deliberate and increasingly diversified approach by threat actors who aim to maximize visibility, chaos, or impact by targeting essential and widely used services across the U.S. economy.
Threat Groups and Motivations
RipperSec
RipperSec is a pro-Palestinian hacktivist group based in Malaysia. They have been active on Telegram since June 2023, amassing over 5,000 followers on their channel before it was banned by Telegram on March 22, 2025. RipperSec’s DDoS attack claim posts consistently follow a recognizable pattern that reveals both their intentions and style. Each post boldly announces disruption of U.S.-based organizations’ websites, often accompanied by hashtags like #OpClean, #FreePalestine, and #StopGenocide. These messages reflect a hacktivist agenda rooted in political protest and social defiance. The content regularly features aggressive slogans and direct calls to action, targeting institutions in industries ranging from finance and government to religion and hospitality.
RipperSec members rely primarily on a Web DDoS attack tool named MegaMedusa for their DDoS attacks. The tool’s source code is maintained and published on Github by a member of the RipperSec group. While its JavaScript code is obfuscated, it is easy enough to deobfuscate and recover readable code. MegaMedusa is a command-line tool to be executed using the Node.js cross-platform JavaScript runtime environment. Node.js provides asynchronous and non-blocking I/O, allowing it to handle multiple requests concurrently. This makes it highly efficient for I/O-bound tasks such as managing large amounts of encrypted web connections. Node.js applications also can run on multiple platforms (Windows, macOS, Linux) without the need for platform-specific code. The author of MegaMedusa provides an installation script and steps to install and run the tool on the code repository’s GitHub landing page. Only five simple commands are needed to download and install the Node.js runtime environment and all required dependencies. Anyone who runs a Linux-based system at home or rents a Linux-based virtual private system in a public or bulletproof cloud can gear up to launch highly scalable Web DDoS attacks against targets of their choice in only a few minutes.
DieNet
Based on Telegram posts from their channel, hacktivist group DieNet has been carrying out a deliberate and ideologically driven DDoS campaign against various U.S. targets. Their actions are framed as a direct response to President Donald Trump, whom they repeatedly accuse of arrogance, tyranny, and criminal behavior. Many of their messages include explicit threats and statements aimed at Trump personally, blaming him for the perceived injustices that motivate their attacks. The group has also linked its actions to broader geopolitical causes, citing solidarity with Palestine and Yemen, and positioning their cyberattacks as retaliation for U.S.-backed violence or right-wing extremism.
Beyond the political and humanitarian messaging, DieNet appears to be using these attacks as a form of symbolic warfare, targeting critical sectors such as finance, energy, telecom and transportation. High-profile institutions like Nasdaq, American Express, PG&E, and the Port of Los Angeles have been among their targets, reflecting an intent to demonstrate the vulnerability of U.S. infrastructure. Their campaign combines attempts at digital disruption with a clear narrative designed to amplify their grievances and project power through cyber means.
Mr. Hamza
Mr. Hamza is a politically motivated hacktivist group suspected to be managed by individuals of Moroccan origin. Emerging in October 2024, the group has primarily conducted DDoS attacks and claimed responsibility for data breaches targeting government institutions, intelligence and cybersecurity agencies, energy infrastructure, financial services, and military sectors. Their operations are mainly directed against countries perceived to support Israel or Western interests, aligning with their anti-Israel and pro-Palestinian agenda.
The organizational structure of Mr. Hamza is decentralized at the operational level but maintains centralized leadership, coordinated through platforms like Telegram. They collaborate with other hacktivist groups and associations, such as the Holy League, NoName057(16), and Z-Pentest, to amplify their impact. Beyond cyberattacks, Mr. Hamza is involved in developing and selling malicious tools, with financing reportedly stemming from these sales as well as donations. Their tactics include leveraging strong ideological messages to recruit members, utilizing social media for global outreach, and offering training sessions to enhance the technical skills of their affiliates.
The group has claimed a wide range of DDoS attacks throughout the first quarter of 2025, targeting U.S. government institutions, military agencies, financial platforms, and culturally symbolic websites. Mr. Hamza’s claims are heavily driven by ideological and political motivations. The messaging behind the attacks frequently references campaigns like #Op_USA and #Op_Corruption, presenting their actions as part of a broader cyber resistance against what they frame as Western hegemony, moral decay, or injustice.
Key targets included prominent domains belonging to the FBI, Department of Homeland Security, U.S. Army, and U.S. Special Operations Command, all of which were described as symbolic strikes against the United States. In addition to state entities, Mr. Hamza also claimed attacks on commercial platforms like Amazon Pay, Microsoft Support, and Pornhub, with claims often tied to themes of financial disruption or moral opposition. Their language emphasizes coordinated operations, often referencing affiliations with other actors like Velvet Team.
Sylhet Gang SG
Since early 2025, the hacktivist collective known as Sylhet Gang SG has intensified its cyber offensive against high-profile American digital infrastructure. The group has launched a series of DDoS attacks targeting major platforms such as Microsoft, Outlook, Pinterest, Rumble, Coinbase, and even critical U.S. government and healthcare systems, including NASA, the FBI's CJIS division, the Department of Education, and Massachusetts General Hospital. These incidents are not isolated stunts; they are strategically executed and publicly shared through Telegram, often accompanied by alleged disruption reports and inflammatory rhetoric directed at U.S. leadership, particularly President Trump.
Sylhet Gang’s messaging, often co-branded with affiliates like DieNet and Dark Storm Team, frames their operations as acts of retribution for U.S. foreign policy, especially its stance on conflicts in Palestine and Yemen. The language used in their posts is emotionally charged and politically loaded, calling their actions justice for oppressed populations. While they target both private tech giants and public institutions, their ultimate message is consistent: retaliation against the perceived aggressions of American power abroad.
Spider-X
Spider-X is an Indonesian hacktivist group known for launching cyberattacks against various targets, particularly in Malaysia. On January 28, 2025, Spider-X conducted a Distributed Denial-of-Service (DDoS) attack on a Malaysian military website. These actions were part of escalating cyber conflicts between Malaysian and Indonesian hacktivists, sparked by geopolitical tensions.
Since January 2025, the hacktivist group has claimed responsibility for a wave of DDoS attacks targeting high-profile U.S.-based organizations. These include major media outlets like CNBC and CNN, as well as prominent technology and e-commerce platforms such as Amazon. The attacks appear to be politically and ideologically motivated, rooted in the group’s opposition to U.S. foreign policy and perceived injustices against Muslim communities.
One recurring theme is the group’s vocal support for the Palestinian cause, with slogans like “Free Palestine” and hashtags such as #Hack_For_Humanity featuring prominently in their communications. The group also positions itself against U.S. actions in the Middle East, particularly the classification of certain militant groups as terrorist organizations. In several posts, Spider-X references the U.S. designation of Ansar Allah, also known as the Houthi movement, as a terrorist entity and describes its campaigns as retribution for what it considers American complicity in regional violence.
Dark Storm Team
Since the start of 2025, the Dark Storm Team has been responsible for a growing number of cyberattacks on U.S.-based digital infrastructure. Specializing in DDoS tactics, the group has repeatedly targeted major platforms like ChatGPT, Binance.US, X (Twitter), Flickr, and public institutions including the FBI, LAPD, and multiple American airports.
What sets Dark Storm Team apart from many hacktivist collectives is their commercial motivation. Unlike groups that operate primarily under ideological or political banners, Dark Storm’s operations appear to be a form of advertisement for their DDoS-for-Hire services. Their attacks serve as live demonstrations of their capabilities—takedowns of well-known entities meant to impress potential clients and establish credibility in the cybercrime marketplace. This shift from pure hacktivism to cyber mercenary work represents a growing trend in the underground economy, where threat actors blend activism, chaos, and commerce.
Despite their lack of overt political messaging, there are hints of anti-authority sentiment in some of their campaigns, such as targeting law enforcement or government sites. But the broader narrative is one of calculated brand-building. By continuously targeting high-visibility websites and services, Dark Storm Team amplifies its name, drawing attention from both the cybersecurity community and potential buyers looking to outsource digital disruption.
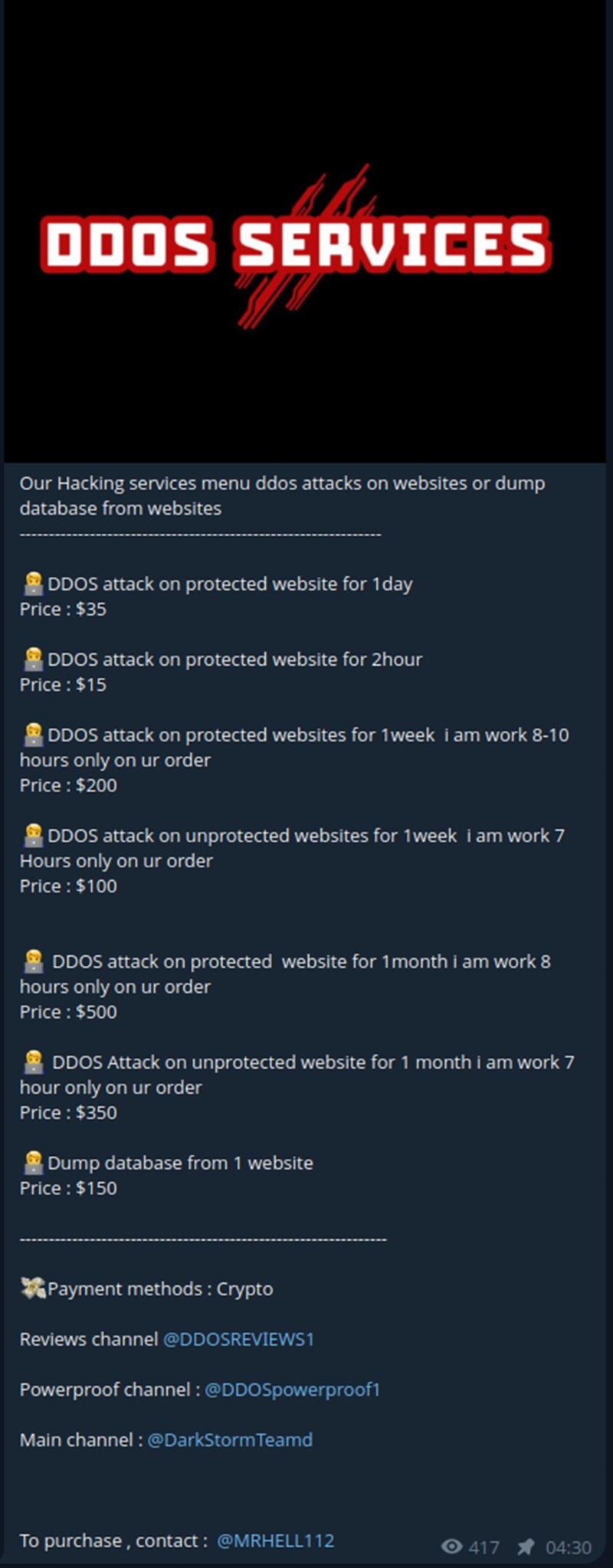
Figure 7: DDoS Services offered by Dark Storm Team on their Telegram channel (source: Telegram)
KMP Group
In early 2025, KMP Group, operating from a Telegram channel named keymous+, a lesser known but increasingly aggressive hacktivist group, ramped up its operations against a broad range of U.S. financial institutions and public services. Within a span of just a few hours on April 2, the group launched a coordinated digital offensive that targeted multiple small-to-midsize regional banks across the United States—including Liberty Bank, Bryant Bank, Northrim Bank, Gateway Bank, and the Bank of Stockton.
KMP Group has primarily focused its efforts on the financial sector, targeting banks from Delaware to Alaska, but it has also expanded into government and healthcare systems both in the U.S. and abroad. Notably, the group previously claimed responsibility for attacks targeting Coinbase, AT&T, MediaCom, and InfraGard, and has allegedly disrupted government portals in Iraq and Yemen.
While KMP Group lacks the polish or ideological clarity of more prominent hacktivist actors, their persistence and the breadth of their targets suggest a group that’s both opportunistic and looking to build name recognition. Some messages include references to other threat groups, indicating possible coordination or mutual amplification strategies.
For now, KMP Group remains a wildcard in the hacktivist space: less structured, more erratic, and difficult to pin down in terms of purpose. But with attacks growing in frequency and geographical spread, the group is carving out its own space among the noisy, fragmented world of politically charged cyberattacks. Whether their endgame is chaos, protest, or profit, their evolving campaign suggests they’re not going anywhere quietly.
ANT1 T4NK Cyber Team
Based on ANT1 T4NK Cyber Team’s claimed attacks during Q1 2025, their activity appears to be driven primarily by commercial motivation. Many of the group’s posts were used to promote a DDoS-for-Hire service known as “Lucky Stresser” with multiple messages including phrases like “BUY PLAN? CLICK HERE” and links to Telegram sales channels. This strongly suggests that the group's primary objective is not political or ideological, but instead to advertise and monetize their capabilities through paid stress-testing or attack services.
Their U.S.-based targets span several industries, with a noticeable focus on retail, telecom, and government sectors. These include small businesses such as Rechek's Food Pride and Pim's Thai Catering, as well as larger organizations like AdGuard Software, CoinBrain, and Eastern Arizona College. Government-related domains like health.gov and regional law enforcement websites were also targeted. In some posts, ANT1 T4NK associates themselves with broader attack collectives or alliances, referencing other threat groups and cyber teams—potentially to signal legitimacy or bolster reputation within underground communities.
Ultimately, the data reveals that ANT1 T4NK’s attacks serve as a hybrid between opportunistic DDoS demonstrations and advertising campaigns for cybercriminal services, rather than being part of a politically motivated hacktivist agenda.
In Conclusion
The first quarter of 2025 marked a significant escalation in hacktivist activity against U.S. organizations, driven by both political agendas and commercial interests. While ideologically motivated groups like RipperSec, DieNet, and Mr. Hamza framed their DDoS attacks as digital resistance against American foreign policy or in solidarity with global causes, others like ANT1 T4NK Cyber Team and Dark Storm Team capitalized on the visibility of high-profile attacks to promote DDoS-for-Hire services. The United States’ dominance as a target—surpassing even conflict zones like Ukraine and Israel—underscores its central role in the geopolitical narratives that fuel these campaigns.
The diversity of threat actors and their motivations also reflects a broader shift in the threat landscape, where lines between activism, cybercrime, and propaganda continue to blur. From attacks on federal agencies and critical infrastructure to symbolic disruptions of cultural and media platforms, threat groups are increasingly strategic in selecting targets that maximize attention, impact, or marketability. Whether driven by ideology or profit, their activities point to a growing normalization of politically charged cyber disruption and a continuing need for vigilance, resilience, and response from both public and private sectors.
Download Our Threat Report