Mr Hamza is a prominent hacktivist group that has claimed over 250 DDoS attacks within the past three months alone. Allegedly run by Moroccan actors, the group operates at the intersection of ideology and commercialization, and it drives an anti-Israel and pro-Palestinian agenda. The group not only executes attacks aligned with its geopolitical agenda but also advertises and sells malicious tools, including DDoS-as-a-Service platforms such as EliteStress, Onyx, Cortex, Blank, Luno Botnet, Trident Network and others. The group maintains a strong presence on Telegram and additional communication such as X (formerly Twitter).
Figure 1: Mr Hamza's X account (source: X)
Mr Hamza is well connected in the hacktivism ecosystem on Telegram, frequently forwarding attack claims from other prominent groups and other members of the Holy League hacktivist collecting. This includes NoName057(16), Hezi Rash, Server Killers, DieNet and Moroccan Black Cyber Army.
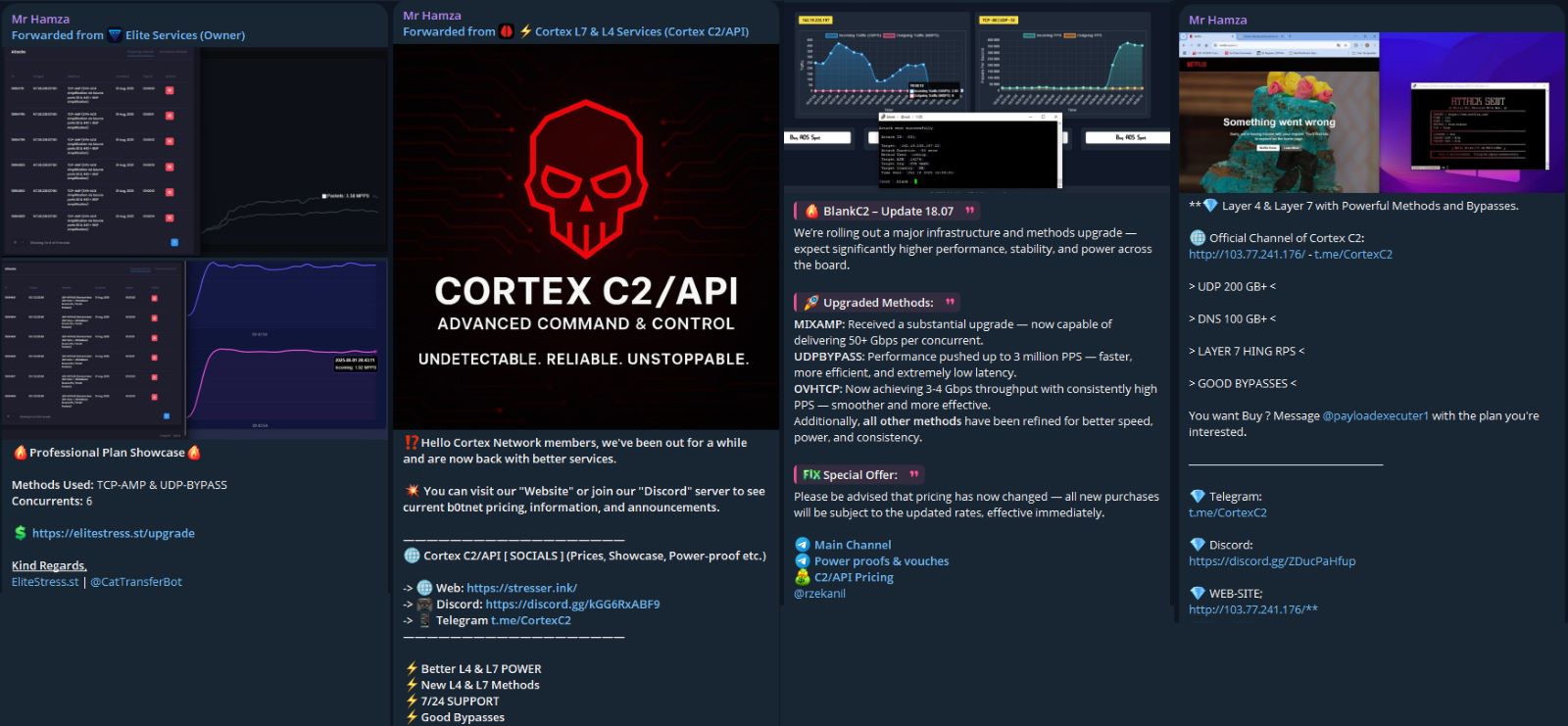
Figure 2: Mr Hamza advertises several booter and stresser services on its channel (source: Telegram)
Mr Hamza was also observed sharing the source code of an attack tool named Abyssal DDoS V3 with its Telegram channel members. This Python-based script combines multiple DDoS techniques including layered obfuscation mechanisms that make it an asset in the hands of unexperienced threat actors.
Abyssal DDoS
A review of the script's structure reveals a guided, interactive flow designed to walk the operator through the attack configuration process. Upon execution, the tool presents a large logo branded with “Mr Hamza” and a legal disclaimer, followed by a sequence of input prompts. These include:
- Target selection – The user is prompted to input a target, either a domain name or an IP address.
- Port selection – The user specifies the target port.
- Attack duration – The user sets how long the attack should last (in seconds).
- Attack type selection – The user chooses from a list of 32 attack techniques, covering various network- and application-layer methods.
- Stealth mode prompt – The tool offers an optional stealth mode, designed to enhance evasion and bypass security mechanisms.
- Thread count configuration – The user defines the number of concurrent threads to use for the attack, affecting intensity and concurrency.
Figure 3: Mr. Hamza's tool-logo (source: Radware)
Attack Vectors
The tool offers 32 attack methods, targeting various layers of the network and application stack. Here are several prominent examples:
-
HTTP(S) flood
This method overwhelms the target server by sending HTTP(S) requests. The attack method includes JavaScript powered Cloudflare bypass, geo-distributed simulations and proxy cycling. This attack vector is aimed at exhausting server resources at the application layer (Layer 7) and targeting specific websites or online APIs.
-
SSDP Amplification
This well-known reflection and amplification DDoS attack vector abuses publicly exposed Simple Service Discovery Protocol (SSDP) services. SSDP is a UDP-based protocol used for advertisement and discovery of network services and presence information. The attack method spoofs the victim’s IP address in SSDP discovery requests, causing the reflection devices to respond with large payloads to the victim, amplifying the attack bandwidth with ratios up to 20x and the packet throughput up to 7x.
-
HTTP/2 Frame Flood
Leveraging the multiplexing capabilities of HTTP/2, the attacker opens multiple simultaneous streams and sends hundreds of small frames per stream. This consumes significant memory and CPU on web servers that haven't properly implemented HTTP/2 stream or frame rate limiting, leading to resource exhaustion.
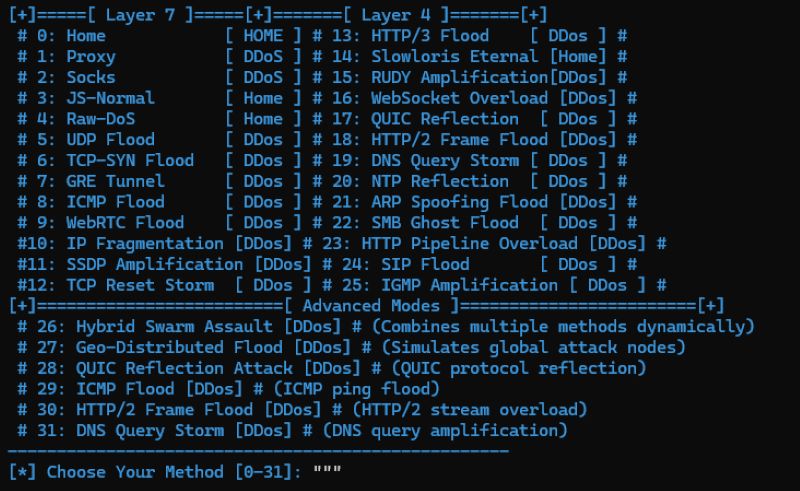
Figure 4: The list of attack methods the tool provides (source: Radware)
Additional Capabilities and Accessibility
Beyond the various attack methods, Abyssal DDoS also includes features aimed at increasing the tool’s effectiveness and usability. The tool generates randomized HTTP request headers, such as User-Agent, Accept and Referrer, which adds a layer of obfuscation and may help avoid simple header-based classification.
Despite being a command-line tool written in Python, the script is designed to be user-friendly, with clear step-by-step prompts that guide the user through each decision. This makes it accessible even for individuals without technical background, lowering the entry barrier to perform or participate in DDoS activity.
Conclusion
The emergence of tools like Abyssal DDoS demonstrates a growing trend in the hacktivist landscape: making sophisticated attack capabilities available to a broader audience. By combining user-friendly design with multiple attack vectors, the tool lowers the technical threshold required to participate in digital offensives.