Why Are DDoS Mitigation Providers Needed?
DDoS mitigation providers are vendors or service companies that offer solutions to defend against distributed denial-of-service (DDoS) attacks. Major DDoS mitigation providers include Radware, Cloudflare, and Akamai.
DDoS attacks can overwhelm web applications, APIs, or entire networks with malicious traffic, aiming to disrupt normal operations and deny service to legitimate users. DDoS mitigation providers deploy infrastructure, technology, and expertise to identify, absorb, and neutralize harmful traffic before it affects customer systems, ensuring business continuity.
For organizations without dedicated in-house resources or expertise, partnering with a DDoS mitigation provider can be crucial. These providers typically operate large, globally distributed networks capable of handling high volumes of attack traffic. Their services may be delivered through cloud-based platforms, on-premise appliances, or hybrid approaches.
This is part of a series of articles about DDoS solutions.
In this article:
DDoS mitigation providers deliver services that focus on detecting, analyzing, and suppressing DDoS threats as they emerge. Their core mission is to separate legitimate user traffic from malicious data streams, ensuring that attacks do not disrupt normal operations. This often involves traffic monitoring, behavioral analysis, and threat intelligence input to distinguish and block attack vectors such as volumetric floods, protocol attacks, and application-level assaults.
Beyond attack filtering, these providers support incident response teams, deliver reporting, and conduct post-attack analysis to strengthen future security posture. Some services include real-time dashboards for visibility, customizable mitigation policies, and proactive alerts. By quickly identifying DDoS activity and deploying countermeasures, these services help organizations restore normal operations with minimal downtime.
Mitigation Capacity
Mitigation capacity refers to the maximum volume of attack traffic a provider can absorb before their defenses are overwhelmed. A leading DDoS mitigation provider should offer high-capacity scrubbing centers distributed globally, enabling them to withstand multi-terabit-per-second attacks. The provider’s ability to dynamically scale resources based on attack severity ensures protection for both small and large organizations, regardless of the nature or intensity of the assault.
Detection Speed and Response Time
Detection speed and response time are critical parameters for any DDoS mitigation provider. Rapid identification of malicious traffic enables swift action to minimize downtime and service interruptions. Top vendors utilize real-time monitoring, automated detection algorithms, and pre-configured response mechanisms that initiate mitigation within seconds of an attack being detected. The faster the detection and response, the less impact the organization will experience from the attack.
Coverage Across Layers
DDoS attacks can target multiple layers of the OSI model, from volumetric assaults at the network layer (Layer 3/4) to application-level attacks at Layer 7. A mitigation provider must deliver layered coverage, defending against threats at both the infrastructure and application levels. Network-layer protection typically requires high-capacity filtering, while application-layer protection demands analytics to uncover subtler, protocol-based or behavioral threats.
Traffic Routing and Latency Impact
Traffic routing is a core function of DDoS mitigation, as attack traffic is diverted to scrubbing centers where filtering occurs. The quality and configuration of diversion (via DNS changes, BGP rerouting, or inline solutions) influence both the effectiveness of mitigation and user experience. Misconfigured or inefficient routing may introduce delays or create additional points of failure, impacting legitimate traffic flow. Latency impact is an important consideration, since excessive delays can degrade the end-user experience as much as a successful attack.
Integration with Existing Infrastructure
Smooth integration with existing infrastructure simplifies deployment and maximizes the effectiveness of DDoS protection. A top-tier provider should offer APIs, deployment templates, and flexible architecture to support diverse environments, including cloud, on-premise, and hybrid systems. Compatibility with current networking hardware, security tools, and traffic management solutions enables organizations to implement protection with minimal disruption or re-architecture.
False Positive Control
Effective DDoS mitigation blocks hostile traffic while allowing legitimate users through. Excessive false positives, where valid requests are mistaken for attack traffic, can disrupt business, damage reputation, and necessitate manual intervention. Leading providers excel at accurate traffic classification, using algorithms, machine learning, and continuously updated threat intelligence to reduce false positives.
1. Radware DDoS Protection

Radware DDoS Protection is a comprehensive, multi-layer defense solution that safeguards networks, applications, and data centers from both high-volume volumetric floods and sophisticated application-layer attacks. Backed by an extensive global mitigation fabric, Radware can absorb massive attack traffic, delivering 15 Tbps of total scrubbing capacity across 21 fully meshed Anycast scrubbing centers worldwide, ensuring that malicious traffic is filtered close to its source with minimal impact on legitimate traffic. Using patented behavioral-based algorithms and real-time threat intelligence, Radware automatically detects and neutralizes even novel or encrypted attacks in real time. Available as cloud (always-on or on-demand), on-premises, or hybrid deployment, the solution provides flexible protection tailored to any environment and around-the-clock expert support.
Key features include:
- Global mitigation network: 15 Tbps of total capacity across 21 globally distributed scrubbing centers. These nodes are fully connected via Anycast, so traffic is analyzed and cleaned at the nearest point to its source, minimizing latency and collateral impact.
- Multi-layered defense: Protects across network (L3/4) and application (L7) layers to cover all major attack vectors. It deploys specialized filtering and intelligence for volumetric floods, protocol exploits, DNS/SSL attacks, and web-layer DDoS.
- Behavioral AI & zero-day detection: Patented behavioral-based algorithms continuously learn legitimate traffic patterns to automatically identify and block sophisticated and previously unknown threats in real time, including IoT botnet floods, encrypted SSL/TLS attacks, and ransom-style application-layer assaults.
- Automated, rapid mitigation: Supports instant activation and auto-scaling to engage scrubbing as soon as an attack is detected. Radware’s solutions can deploy within minutes and mitigate multi-vector attacks with minimal manual intervention.
- 24/7 expert support: Radware’s Emergency Response Team (ERT) provides continuous monitoring, real-time threat analysis, and hands-on assistance during incidents. This helps organizations maintain continuity and strengthen defenses during and after an attack.
- Flexible deployment: Offered as physical or virtual appliances, cloud-based scrubbing services, or hybrid models, supporting diverse environments from enterprise data centers to service providers and multi-cloud networks.
2. Cloudflare DDoS Protection
Cloudflare DDoS Protection is a high-capacity, globally distributed service to block large-scale DDoS attacks without affecting legitimate traffic or degrading performance. With a mitigation network capacity of 449 Tbps, it absorbs attack traffic at edge locations in more than 330 cities. This proximity-based approach reduces latency by filtering malicious data close to its source.
Key features include:
- Global capacity: 449 Tbps of mitigation bandwidth for absorbing even the largest attacks
- Edge-based filtering: Attack traffic is mitigated at the nearest data center, minimizing latency
- Layered protection: Defends infrastructure and applications across OSI layers 3, 4, and 7
- Fast deployment: Protection can be enabled in minutes; emergency hotline for real-time assistance
- 24/7 support: Global support via phone and email, with enterprise-grade response readiness
3. Akamai DDoS Protection
Akamai DDoS Protection is a multi-layered defense solution built on dedicated infrastructure to detect and stop sophisticated attacks before they impact business operations. It protects internet-facing systems across cloud, on-premises, and hybrid environments. Akamai filters traffic at the edge, allowing organizations to maintain uptime while shielding applications.
Key features include:
- Dedicated infrastructure: Purpose-built backbone designed to absorb complex and persistent attacks
- Edge-based defense: Stops malicious traffic in the cloud before it reaches internal servers
- Layered coverage: Protects across all layers, including applications, APIs, infrastructure, and DNS
- Flexible deployment: Supports in-cloud, on-premises, and hybrid environments
- Resilient DNS services: High availability through segmented DNS across nonoverlapping clouds
4. Imperva DDoS Protection
Imperva DDoS Protection delivers automated mitigation against volumetric, protocol-based, and application-layer attacks, ensuring uptime during large-scale assaults. Built on a global, low-latency network, the solution detects and neutralizes DDoS traffic within seconds, supported by a 3-second SLA for Layers 3 and 4.
Key features include:
- Comprehensive multi-layer defense: Protects against volumetric (L3), protocol-based (L4), and application-level (L7) attacks
- Ultra-fast mitigation: Guarantees mitigation within 3 seconds for network-layer attacks
- Automated protection: Fully automated detection and response with no manual intervention required
- Adaptive Layer 7 defense: Dynamically identifies and blocks sophisticated application-layer DDoS threats
- Global low-latency network: 95% of users experience sub-50 ms latency through optimized Anycast routing
5. F5 Networks DDoS Attack Protection Services
F5 Networks offers layered DDoS attack protection across layers 3, 4, and 7 to defend both network infrastructure and applications from high-volume, multi-vector attacks. The solution suite includes cloud-based, on-premises, and containerized deployment models, providing flexibility for various environments.
Key features include:
- Layered DDoS defense: Protects across L3, L4, and L7 with mitigation against volumetric and application-targeted attacks
- Multiple deployment options: Available as managed service, hardware appliance, software, virtual machine, or containerized solution
- Real-time detection and mitigation: Scrubs malicious traffic before it impacts applications or data centers
- Cloud-delivered scalability: Distributed Cloud DDoS Mitigation provides scalable protection via F5’s global scrubbing centers
- Application-aware security: Layer 7 protection for HTTP, DNS floods, slowloris, and other app-level threats
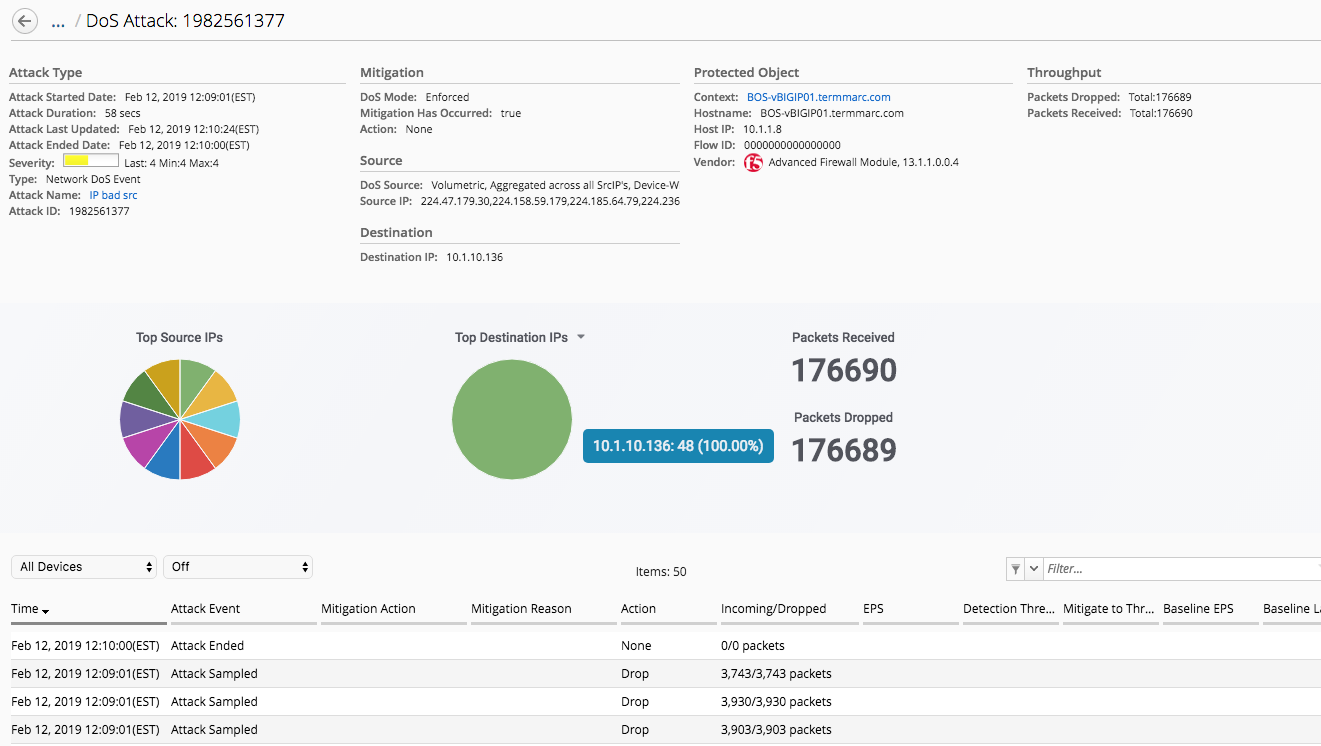
Source: F5
Related content: Read our guide to DDoS mitigation tools.
Conclusion
DDoS mitigation providers play a critical role in protecting digital infrastructure from increasingly sophisticated and high-volume attacks. By offering scalable, real-time defense mechanisms across multiple network layers, these providers ensure service availability and performance even during large-scale disruptions. Key capabilities such as rapid detection, behavioral traffic analysis, automated response, and global scrubbing infrastructure enable organizations to maintain business continuity without internal operational strain.