What Is DDoS Mitigation?
DDoS (Distributed Denial of Service) mitigation is a set of tools and techniques that protect networks and systems from distributed denial-of-service (DDoS) attacks. DDoS attacks aim to disrupt the normal functioning of a target, such as a network, server, or web application.
DDoS mitigation typically involves the following stages:
-
Detection: Identifying deviations in traffic flow that may indicate a DDoS attack.
-
Recognition: Recognizing an attack as early as possible.
-
Diversion: Rerouting traffic away from its target.
-
Filtering: Identifying patterns that distinguish between legitimate and malicious traffic.
-
Analysis: Learning from the DDoS attack to improve mitigation against future attacks.
DDoS mitigation can be achieved through the use of:
-
Cloud-based protection services: Software solutions or cloud-based services to identify, mitigate, and recover from DDoS attacks.
-
Network equipment: Specially designed network equipment to mitigate the threat.
-
Blackholing/null routing: Directs malicious traffic to a nonexistent or null route, discarding it to protect the target infrastructure.
-
Sinkholing: Redirects malicious traffic to a controlled server for analysis and containment, providing insights into attack patterns.
-
Scrubbing: Filters incoming traffic through dedicated centers to separate malicious data from legitimate requests, ensuring uninterrupted service.
-
Anycast network diffusion: An approach that scatters attack traffic across a network of distributed servers to absorb the traffic.
This is part of a series of articles about DDoS protection.
In this article:
DDoS mitigation is critical because attacks can disrupt businesses, leading to downtime, loss of revenue, and reputational damage. The time during which services are unavailable can lead to significant financial losses, especially for eCommerce and financial services. Beyond immediate cost, long-term trust and reliability are compromised, potentially resulting in lost customers.
DDoS attacks can also serve as a smokescreen for more malicious activities, such as data exfiltration or ransomware deployment. An effective DDoS mitigation strategy makes it easier for organizations to identify and react to parallel attack activities.
Tangible Costs of DDoS Attacks
The direct financial impacts of DDoS attacks include the immediate costs of downtime across affected services. For popular online platforms, every minute of downtime can lead to lost sales, reduced productivity, and increased operational costs. Other direct costs include:
- Cost of manpower across the organization to restore systems to normal operations.
- Penalties for not meeting service level agreements (SLAs) with clients.
- Cost of scaling up infrastructure to mitigate attacks.
- Legal and regulatory penalties for organizations subject to strict compliance requirements.
Intangible Costs of DDoS Attacks
Intangible costs are often more complex to quantify but may include erosion of brand reputation and customer trust. In competitive markets, downtime can drive clients towards competitors, leading to loss in market share. Public relations efforts to restore the company's image can be extensive and costly, and may not always bear fruit.
Employee morale may also suffer, especially if they are overburdened during an attack. The general perception of a company's technological resilience can be impacted, influencing future business opportunities. This perceived vulnerability can have long-term effects on market position and business partnerships.
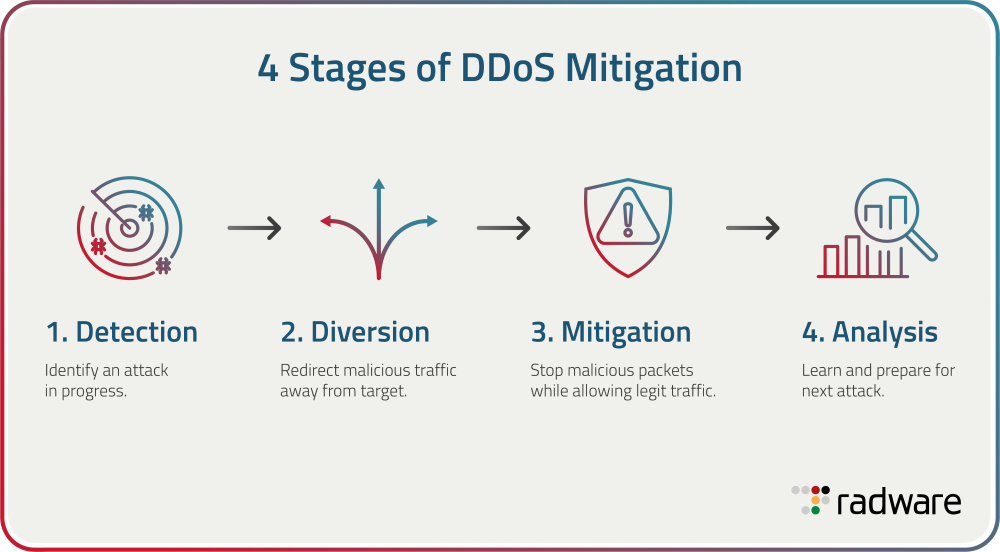
Figure 1: 4 Stages of DDoS Mitigation
1. Detection
The detection stage focuses on identifying an attack in progress. Early detection involves monitoring traffic patterns to spot anomalies that may indicate a DDoS attack. This involves tools and technologies that continuously inspect data flow and alert administrators and security teams to potential threats.
Modern DDoS detection systems use machine learning algorithms to distinguish between legitimate and malicious traffic. Effective detection reduces response times, allowing security personnel to enact countermeasures quickly. Automated detection systems provide a real-time assessment of threats, which is critical in mitigating the impact of the attack.
2. Recognition
The recognition stage involves confirming that anomalies in traffic are part of a DDoS attack rather than benign spikes in usage. This requires analyzing the nature, source, and patterns of the traffic to differentiate between legitimate surges (e.g., a product launch) and malicious activity. Tools like deep packet inspection (DPI) and behavioral analysis help identify key indicators such as spoofed IP addresses, repetitive request patterns, and volumetric anomalies.
Effective recognition relies on maintaining up-to-date threat intelligence. By comparing observed traffic against known attack signatures and leveraging machine learning, recognition systems can accurately classify the type and scope of the attack. Early and precise recognition ensures the deployment of appropriate countermeasures, reducing potential damage and disruption.
3. Diversion
Diversion involves redirecting malicious traffic away from its target, often by sending it to scrubbing centers (facilities that can absorb and inspect a huge volume of malicious traffic). This strategy aims to separate harmful traffic from legitimate user requests to ensure that only clean data reaches the intended server or application. Diversion serves as a buffer, reducing direct strain on network resources.
This process requires technology to handle massive volumes of captured traffic without delay. Diversion complements other mitigation techniques by ensuring normal operations can continue unaffected by the high volume of attacks typical in DDoS scenarios.
4. Mitigation
Mitigation involves cutting off malicious packets while allowing legitimate traffic to proceed. This involves specialized software or hardware that can scrutinize incoming data according to predefined rules. The key is creating filters to block attack patterns without hindering legitimate service requests.
Modern filtering techniques use a combination of signature and anomaly-based detection. Implementing dynamic filtering rules can adapt to the evolving nature of DDoS threats. This ensures the DDoS mitigation system can block all malicious packets while allowing legitimate ones to pass, avoiding impact on the organization and its users.
5. Analysis
Analysis follows mitigation and focuses on learning from the attack to strengthen defenses. Post-incident analysis examines the attack vector, methodologies utilized, and the effectiveness of the mitigation controls. Analysis aims to identify vulnerabilities and optimize defense strategies for future threats.
This stage involves reviewing logs, examining attack patterns, and updating threat intelligence databases. Analysis provides actionable insights, helping to enhance the responsiveness and resilience of the existing cybersecurity infrastructure.
Here are a few ways DDoS protection systems identify, divert, and mitigate attack traffic.
Cloud-Based Protection Services
Cloud-based protection services offer scalable, distributed solutions to counteract DDoS attacks. These services rely on globally distributed infrastructure to absorb and neutralize malicious traffic before it reaches the target. By leveraging the cloud's extensive bandwidth and compute resources, organizations can defend against even the largest volumetric attacks.
These services often include real-time analytics, AI-driven detection, and customizable policies based on relevant threats. Cloud-based protection is particularly effective for organizations without the resources to maintain on-premises mitigation infrastructure, offering an accessible and cost-effective way to protect critical assets.
Network Equipment
Network equipment for DDoS mitigation includes routers, firewalls, and intrusion prevention systems (IPS) that incorporate advanced filtering and traffic management capabilities. These devices can identify suspicious traffic patterns, block known attack vectors, and enforce rate limiting to prevent overwhelming the target infrastructure.
Modern network equipment often integrates real-time monitoring tools and threat intelligence feeds. These features enable proactive defense by adapting to emerging attack signatures and ensuring that legitimate traffic experiences minimal disruption. The deployment of specialized network hardware can offer localized protection and reduce reliance on external mitigation services.
Blackholing/Null Routing
Blackholing, or null routing, involves directing unwanted traffic to a nonexistent route. This method effectively removes harmful packets from the network. It's a straightforward technique aiming to protect the targeted service from traffic overload by discarding network packets at the routing level.
While blackholing is simple to implement, indiscriminate use can result in collateral damage, affecting legitimate traffic. Its effectiveness lies in its ability to quickly mitigate the impact of high-volume attacks but requires precise configuration to minimize adverse effects on service availability.
Sinkholing
Sinkholing directs malicious traffic to a controlled stop where it can be analyzed. Unlike blackholing, sinkholing allows some traffic insights, which may be useful for forensic analysis and understanding attack patterns. By absorbing attack data, organizations can refine detection and mitigation strategies.
Implementing sinkholing requires investments in controlled infrastructure. It involves cooperation with ISPs and network fabric providers to ensure robust redirection of harmful streams. This method centers on creating resilience by controlling exposure to unwanted network activities.
Scrubbing
Scrubbing centers use filtering mechanisms to clean incoming traffic. This method separates malicious data from legitimate user requests, ensuring business operations remain uninterrupted. Scrubbing can be integrated into the network infrastructure or provided by third-party services.
A scrubbing center’s scalability is crucial for defending against large-scale DDoS attacks. By analyzing incoming data packets and removing harmful content, scrubbing supports ongoing service continuity and reduces latency. This method demands massive computing power, typically leveraging globally distributed data centers, to be able to handle large traffic volumes in real time.
Anycast Network Diffusion
Anycast network diffusion disperses incoming traffic across multiple servers in geographically diverse locations. By routing requests to the nearest server, this approach reduces latency for legitimate users while diluting the impact of DDoS attacks. The distributed nature of anycast ensures that no single server becomes overwhelmed, maintaining service availability.
This technique is particularly effective against volumetric attacks, as it leverages the aggregate bandwidth of the network. Anycast also increases resiliency by providing redundancy; even if one server is compromised, others remain operational, minimizing the risk of service disruption.
Learn more in our detailed guide to DDoS attack prevention.
Here are a few key considerations when selecting a DDoS mitigation solution.
Latency
Latency is a critical concern for DDoS mitigation services, as they can introduce delays when serving legitimate traffic. Effective solutions must minimize additional latency while processing legitimate traffic through mitigation systems. Low latency ensures business operations remain fluid, with no noticeable slowdown for end-users.
When evaluating latency, consider the service’s geographic distribution, infrastructure design, and the latency it introduces during attack scenarios. A balance must be achieved where mitigation effectiveness does not come at the cost of a degraded user experience. Prioritizing services with minimal latency footprints is essential in maintaining operational efficiency.
Scalability
A service’s scalability determines its ability to handle varying attack volumes. As attack sizes grow, scalable solutions need to automatically adapt, ensuring protection without manual intervention. Scalability supports performance by adjusting resources based on incoming threat levels, particularly crucial during unexpected surges.
DDoS services should be elastically scalable and have access to global cloud infrastructure, to accommodate both current and projected attack traffic. They must provide flexible resource allocation that matches fluctuating demands, guaranteeing uninterrupted service during peak attack periods.
Flexibility
Flexibility in a DDoS mitigation service allows it to adapt to diverse network environments and threat landscapes. This flexibility is necessary to accommodate various infrastructure setups and integrate with existing security frameworks.
Look for services offering customizable configurations and a variety of deployment models, including on-premises, cloud, or hybrid approaches. This ensures the best fit for current technology ecosystems and anticipates needs driven by evolving cyber threats.
Reliability
Reliability involves a service’s ability to provide continuous protection against DDoS attacks without interruptions. Reliable services have infrastructure with redundancies and failover mechanisms to ensure constant uptime. Reliability is crucial to maintaining trust, upholding service-level agreements, and meeting compliance requirements.
The reliability of a mitigation solution is often backed by a proven track record and transparent performance metrics. Assessing these attributes ensures continued protection alongside adaptive threat management.
Network Size
Network size impacts the capacity of a DDoS mitigation service to distribute traffic and offer protection across expansive service areas. Larger networks provide greater absorption capabilities for massive traffic volumes, and the ability to mitigate more extensive attacks. The network’s breadth and capacity directly influence its efficacy.
When considering network size, assess the service's global reach, relationships with ISPs, and traffic-handling capabilities. A large network with ample points of presence can effectively disseminate attack loads and provide broader protection. This ensures a layered defense and robust mitigation across different regions.
Learn more in our detailed guide to DDoS protection services.
Radware offers a range of DDoS protection solutions designed to meet the needs of businesses of all sizes.
Radware DefensePro X
DefensePro X offers automated, behavioral-based detection and mitigation for a range of network multi-vector and DDoS attack campaigns, IoT botnets, application vulnerability exploitation, malware and other types of cyberattacks. The platform uses dedicated hardware to help mitigate incoming attacks without affecting non-malicious traffic. Through its patented AI-powered and machine-learning technology, it detects incoming threats quickly, coordinating patterns to help block future threats and reducing the potential for false positives.
Radware Cloud DDoS Protection Service
Cloud DDoS Protection Service offers multi-layered defense against DDoS attacks using advanced behavioral algorithms and automatic real-time signature creation. It provides infrastructure DDoS protection against network-layer flooding attacks, secures DNS infrastructure against attacks and protects apps from application-layer DDoS attacks.
Radware Cloud Application Protection Service
Cloud Application Protection Service offers integrated, AI-powered security including industry-leading protection against DDoS attacks. Its unique behavioral detection distinguishes between legitimate and malicious traffic and automatically generates granular signatures in real time. This DDoS protection works with API protection, client-side protection, WAF and bot management capabilities to ensure 360 degrees of protection.
Learn more about Radware