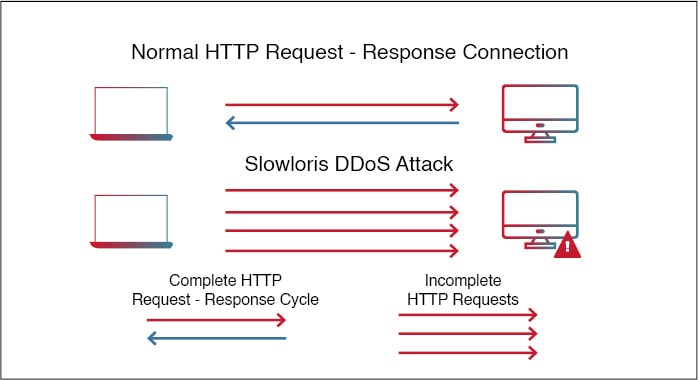
Slowloris is a type of Distributed Denial of Service (DDoS) attack that works by flooding a server with incomplete HTTP requests. The attacks are designed to exploit the limited number of connections that web and application servers can support and the time it takes for the server to close them. In a Slowloris attack, malicious actors send numerous partial requests to the targeted server, preventing legitimate users from being able to access it.
Slowloris works by exploiting what is known as the “Keep-Alive” header of an HTTP request. This header informs the server that there will be additional requests in the future, so an attacker can send multiple incomplete requests and keep them open until the server reaches its connection limit, at which point it will be unable to process new requests from legitimate users.
The attacker then sends additional incomplete requests to maintain control over existing connections and prevent legitimate users from accessing the server. By sending just enough data with each request, without completing it, attackers can effectively tie up resources on a webserver for extended periods of time without using too much bandwidth or computing power.
There are several steps organizations can take to mitigate Slowloris attacks:
- Increase webserver connection limits: This can help reduce vulnerability to Slowloris attacks as it increases the maximum number of open connections that an attacker needs to maintain control over resources on the target webserver.
- Implement rate limiting: Rate limiting involves restricting incoming requests from any given IP address in order to prevent DoS attacks such as those launched by Slowloris attackers. It is essential for organizations to regularly monitor their networks for traffic abnormalities that could indicate malicious activity and take immediate action if necessary.
- Use load balancers and web application firewalls (WAFs): WAFs help protect against application DDoS attacks such as those launched using Slowloris techniques by identifying and blocking malicious traffic before it reaches your network or applications. They also provide logs which organizations can review in order to identify any potential threats or anomalies quickly and take action accordingly. Load balancers and reverse proxies can buffer connections and implement multiple connection management techniques to prevent incomplete HTTP requests from affecting applications and web servers.
- Organizations should also consider using services such as cloud-based DDoS protection or botnet tracking solutions in order to identify suspicious activity quickly and respond appropriately.
- Additionally, security best practices such as keeping software updated and patching vulnerabilities regularly should be followed at all times in order to minimize risk and protect against all types of threats, including those posed by malicious actors who use techniques like slowloris DDoS attacks.
- Radware DDoS protection, WAF service, and application delivery solutions mitigate slowloris attacks by using approaches that block attacks without impacting legitimate traffic. Radware uses machine-learning and behavioral-based algorithms to understand what constitutes a legitimate behavior profile and then automatically blocks malicious attacks while managing user connections effectively, without impacting legitimate HTTP requests. This increases protection accuracy while minimizing false positives and disruption to legitimate users